已更新docker版,1分钟部署完成
https://90apt.com/4604
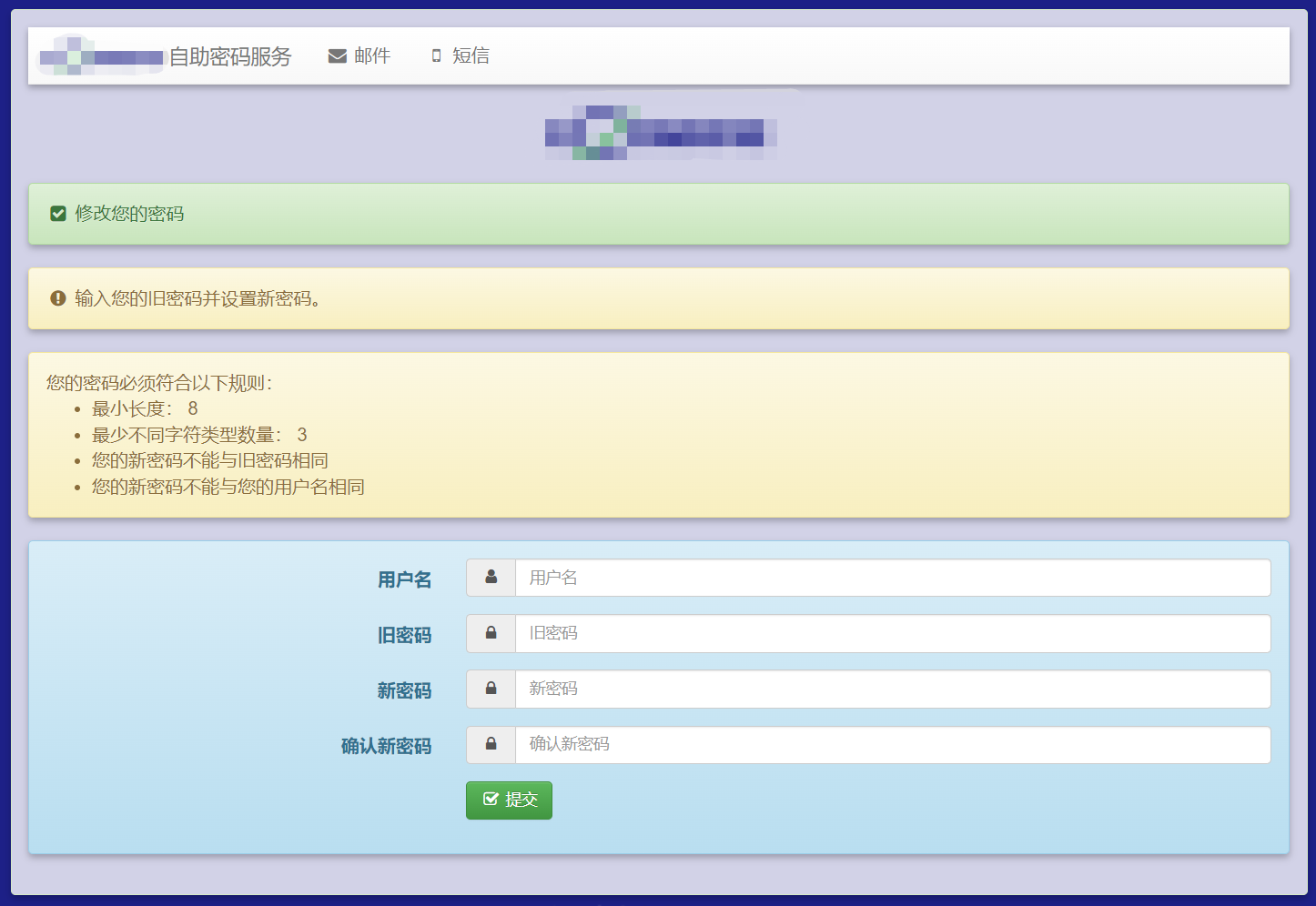
项目官网:
https://www.ltb-project.org/documentation/self-service-password.html
github:
https://github.com/ltb-project/self-service-password
文档:
https://self-service-password.readthedocs.io/en/latest/
本文采用oracle linux8系统安装
安装:
1、安装php-smarty
https://pkgs.org/download/php-Smarty
Download latest remi-release rpm from
http://rpms.remirepo.net/enterprise/8/remi/x86_64/
Install remi-release rpm:
rpm -Uvh remi-release*rpm
Install php-Smarty rpm package:
dnf --enablerepo=remi install php-Smarty2、安装self-service-password
Configure the yum repository:
/etc/yum.repos.d/ltb-project.repo
[ltb-project-noarch]
name=LTB project packages (noarch)
baseurl=https://ltb-project.org/rpm/$releasever/noarch
enabled=1
gpgcheck=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-LTB-project
Then update:
yum update
Import repository key:
rpm --import https://ltb-project.org/documentation/_static/RPM-GPG-KEY-LTB-project
You are now ready to install:
yum install self-service-password3、安装openldap
yum install -y openldap4、AD域导出证书
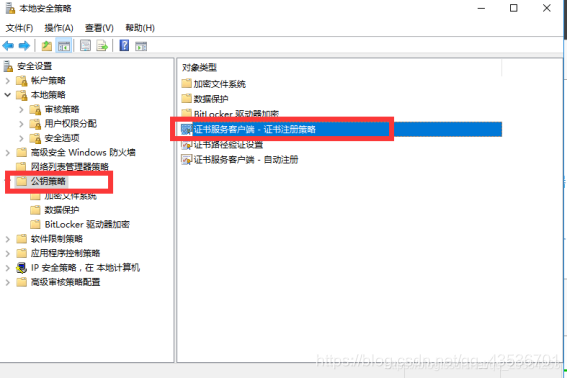
Self Service Password必须以LDAPS方式连接域控,因此需要加载证书
添加角色和功能-AD证书服务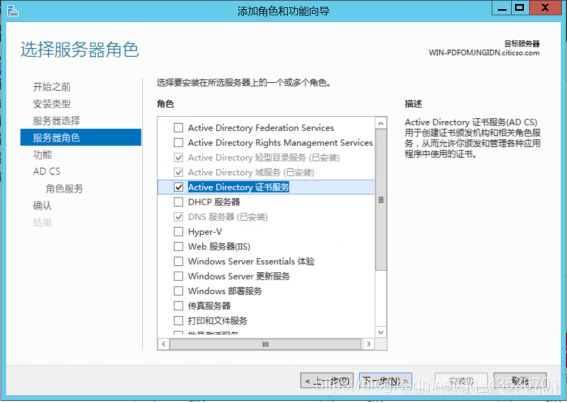
证书颁发机构web注册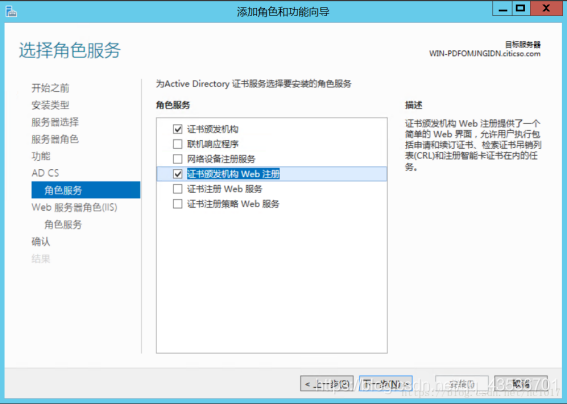
配置证书服务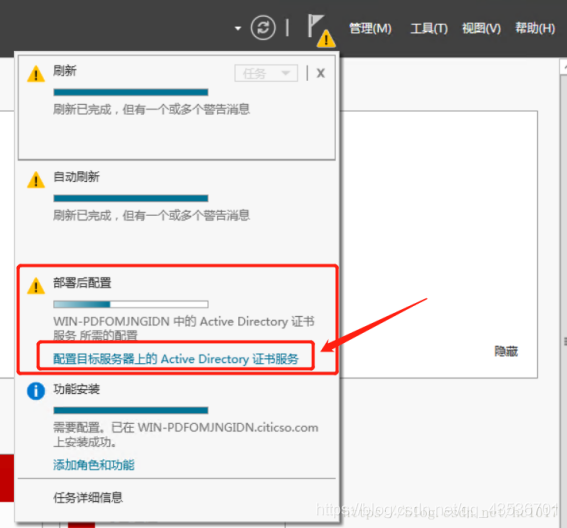
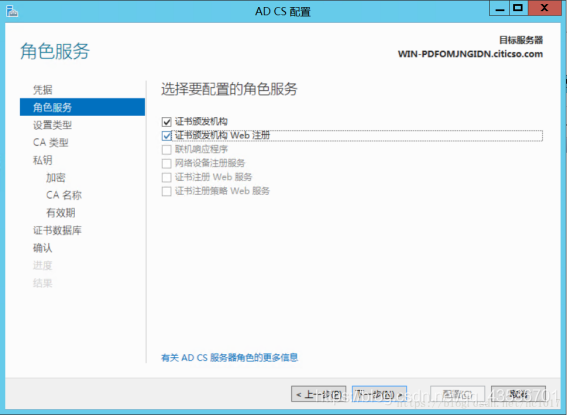
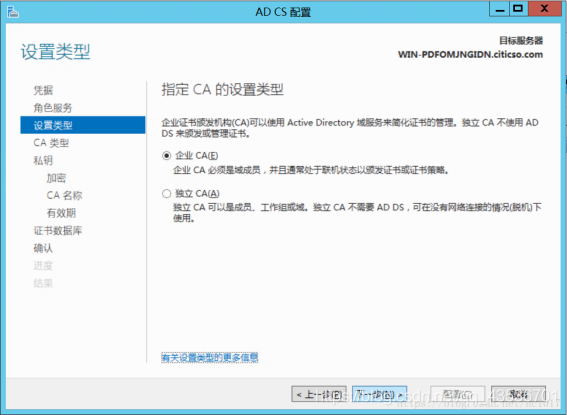
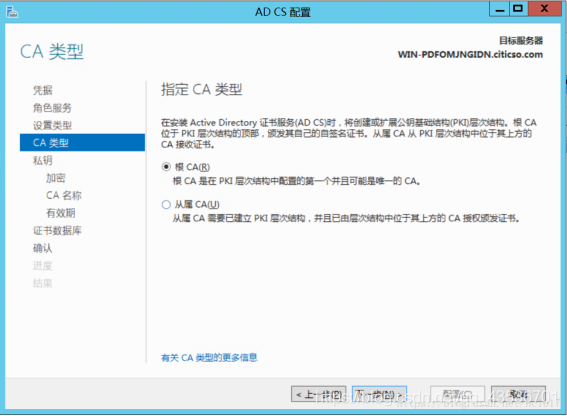
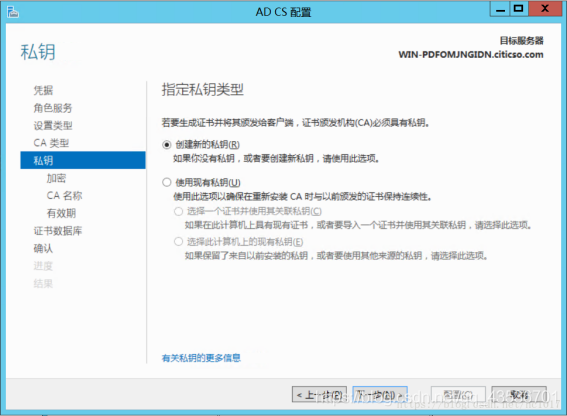
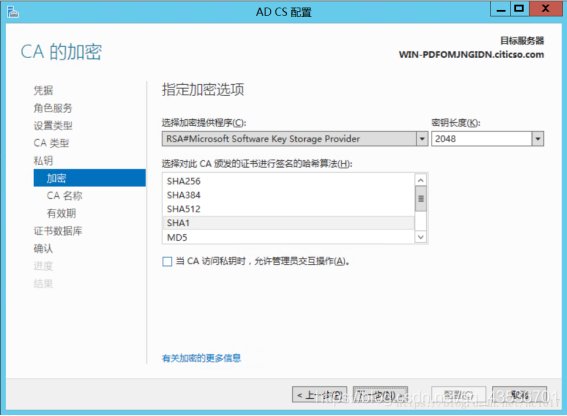
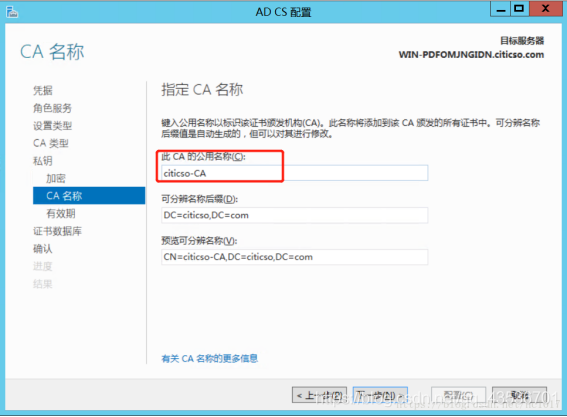
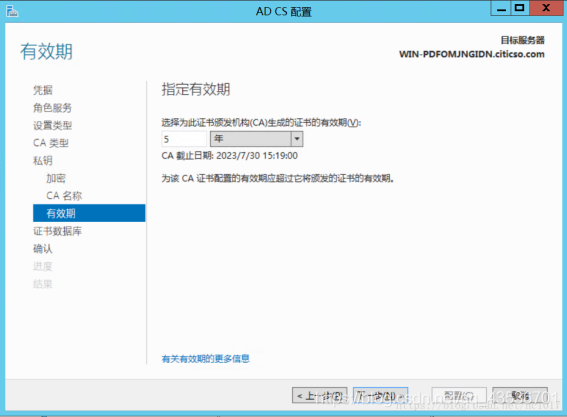
证书颁发机构
开启AD域证书服务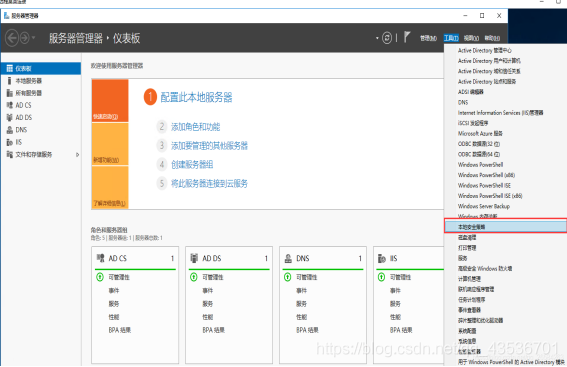
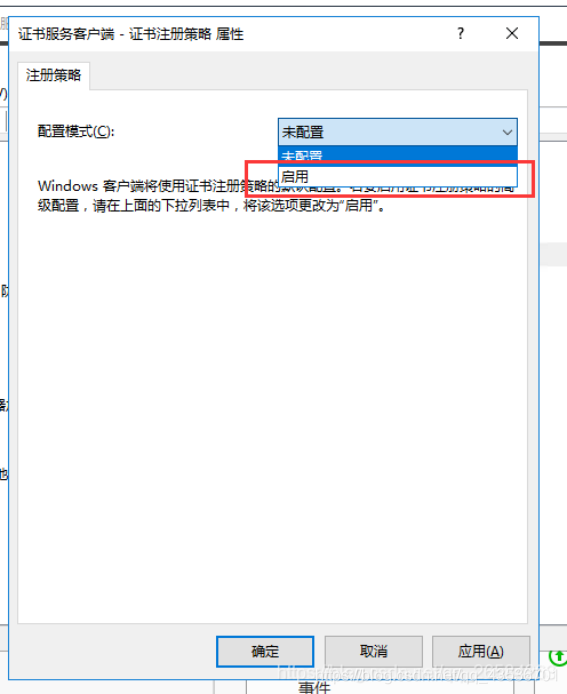
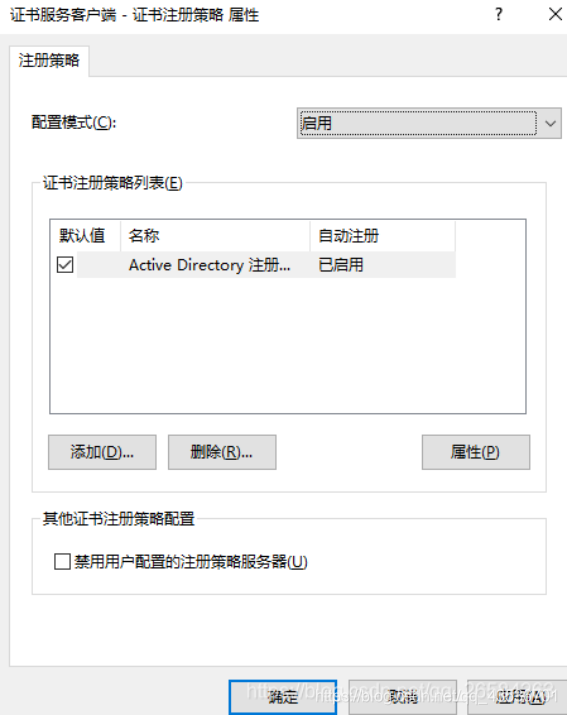
刷新策略
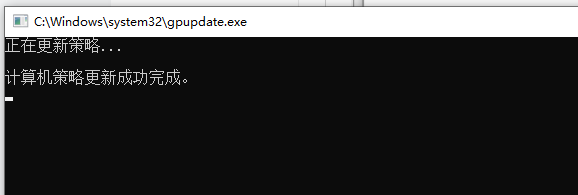
导出证书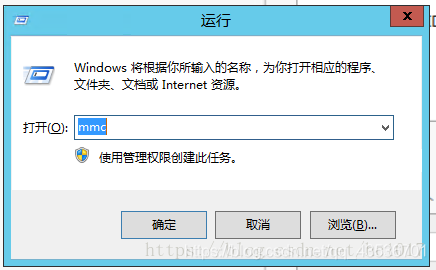
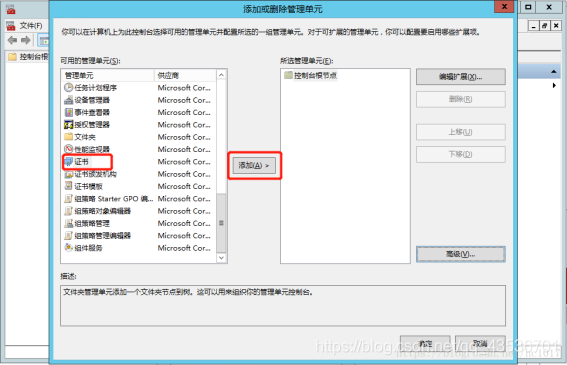

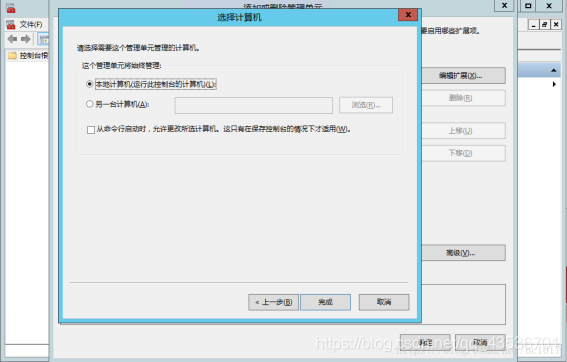
个人证书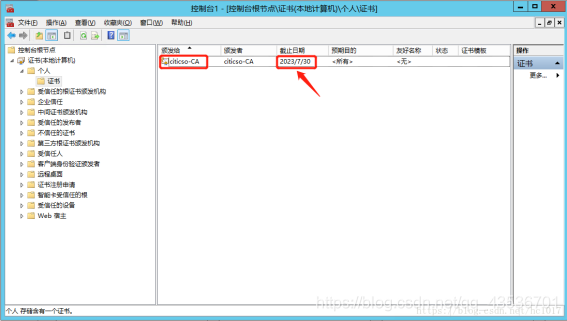
导出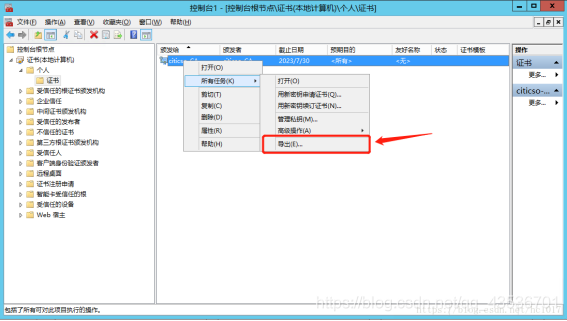
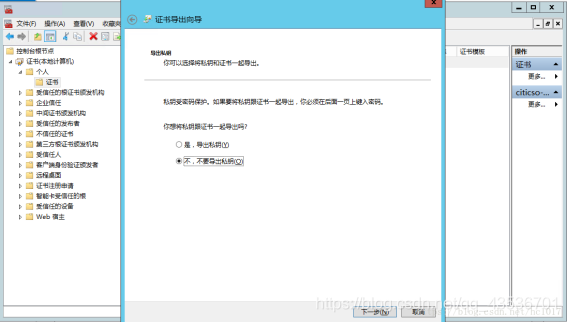
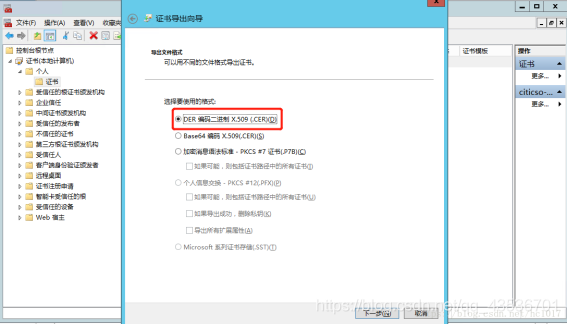
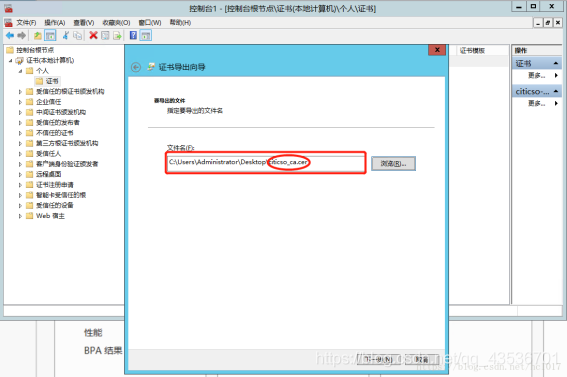
转换证书
openssl x509 -inform der -in ad01.cer -out ad01.pem
cat ad01.pem >> /etc/openldap/certs/ldaps.pemopenldap配置文件
/etc/openldap/ldap.conf
TLS_CACERT /etc/openldap/certs/ldaps.pem
TLS_REQCERT allow5、Self Service Password配置文件
需生成独立配置文件
cd /usr/share/self-service-password/conf/
cp config.inc.php config.inc.local.php我的配置文件config.inc.local.php,主要放上改动的部分和注释
<?php
$debug = false; //debug模式关闭
# LDAP
$ldap_url = "ldaps://ad1.90apt.com:636"; //AD服务器
$ldap_starttls = false;
$ldap_binddn = "CN=wangwangjie,CN=Users,DC=90apt,DC=com"; //使用的域控管理员用户
$ldap_bindpw = "passwd@123"; //上面域控管理员密码
$ldap_base = "OU=王工有限公司,OU=用户OU,DC=90apt,DC=com"; //应用的OU范围
$ldap_login_attribute = "sAMAccountName"; //登陆属性
$ldap_fullname_attribute = "cn"; //全名属性
$ldap_filter = "(&(objectClass=user)(sAMAccountName={login})(!(userAccountControl:1.2.840.113556.1.4.803:=2)))"; //AD需要这么配置
$ldap_use_exop_passwd = false;
$ldap_use_ppolicy_control = false;
$ad_mode = true; //启用AD模式
$ad_options=[];
# Force account unlock when password is changed
$ad_options['force_unlock'] = true; //更改密码时强制解锁账户
# Force user change password at next login
$ad_options['force_pwd_change'] = false;
# Allow user with expired password to change password
$ad_options['change_expired_password'] = true; //允许过期的用户修改密码
# Local password policy
# This is applied before directory password policy
# Minimal length
$pwd_min_length = 8; //最短密码位数
# Maximal length
$pwd_max_length = 0;
# Minimal lower characters
$pwd_min_lower = 0;
# Minimal upper characters
$pwd_min_upper = 0;
# Minimal digit characters
$pwd_min_digit = 0;
# Minimal special characters
$pwd_min_special = 0;
# Definition of special characters
$pwd_special_chars = "^a-zA-Z0-9"; //特殊字符
# Forbidden characters
#$pwd_forbidden_chars = "@%";
# Don't reuse the same password as currently
$pwd_no_reuse = true; //不使用重复密码
# Check that password is different than login
$pwd_diff_login = true; //密码不能与账号相同
# Check new passwords differs from old one - minimum characters count
$pwd_diff_last_min_chars = 0;
# Forbidden words which must not appear in the password
$pwd_forbidden_words = array();
# Forbidden ldap fields
# Respective values of the user's entry must not appear in the password
# example: $pwd_forbidden_ldap_fields = array('cn', 'givenName', 'sn', 'mail');
$pwd_forbidden_ldap_fields = array();
# Complexity: number of different class of character required
$pwd_complexity = 3; //需要不同类别的字符
# use pwnedpasswords api v2 to securely check if the password has been on a leak
$use_pwnedpasswords = false;
# Show policy constraints message:
# always
# never
# onerror
$pwd_show_policy = "always"; //显示约束信息
# Position of password policy constraints message:
# above - the form
# below - the form
$pwd_show_policy_pos = "above"; //在表格上显示
# disallow use of the only special character as defined in `$pwd_special_chars` at the beginning and end
$pwd_no_special_at_ends = false;
# Who changes the password?
# Also applicable for question/answer save
# user: the user itself
# manager: the above binddn
$who_change_password = "manager"; //谁的权限修改
## Token
# Use tokens?
# true (default)
# false
$use_tokens = true;
# Crypt tokens?
# true (default)
# false
$crypt_tokens = true;
# Token lifetime in seconds
$token_lifetime = "3600";
## Mail
# LDAP mail attribute
$mail_attributes = array( "userPrincipalName","mail", "gosaMailAlternateAddress", "proxyAddresses" ); //邮箱形式
# Get mail address directly from LDAP (only first mail entry)
# and hide mail input field
# default = false
$mail_address_use_ldap = true; //直接从域控获取邮箱
# Who the email should come from
$mail_from = "wangwangjie@90apt.com";
$mail_from_name = "域账号自助改密解锁服务";
$mail_signature = "本邮件为通过密码自助修改LDAP账号密码,无需回复,如有重置密码遇到问题可以联系运维同学";
# Notify users anytime their password is changed
$notify_on_change = true;
# PHPMailer configuration (see https://github.com/PHPMailer/PHPMailer)
$mail_sendmailpath = '/usr/sbin/sendmail';
$mail_protocol = 'smtp';
$mail_smtp_debug = 0;
$mail_debug_format = 'html';
$mail_smtp_host = 'smtp.90apt.com';
$mail_smtp_auth = true;
$mail_smtp_user = 'wangwangjie@90apt.com';
$mail_smtp_pass = 'passwd@123';
$mail_smtp_port = 25;
$mail_smtp_timeout = 30;
$mail_smtp_keepalive = false;
$mail_smtp_secure = 'tls';
$mail_smtp_autotls = true;
$mail_smtp_options = array();
$mail_contenttype = 'text/plain';
$mail_wordwrap = 0;
$mail_charset = 'utf-8';
$mail_priority = 3;
## SMS
# Use sms
$use_sms = true;
# SMS method (mail, api)
$sms_method = "api";
$sms_api_lib = "lib/smsapi.inc.php"; //自编写短信api,从短信平台的帮助文档里找
# GSM number attribute
$sms_attributes = array( "mobile", "pager", "ipPhone", "homephone" );
# Partially hide number
$sms_partially_hide_number = true;
# Send SMS mail to address. {sms_attribute} will be replaced by real sms number
$smsmailto = "{sms_attribute}@service.provider.com";
# Subject when sending email to SMTP to SMS provider
$smsmail_subject = "Provider code";
# Message
$sms_message = "{smsresetmessage} {smstoken}";
# Remove non digit characters from GSM number
$sms_sanitize_number = false;
# Truncate GSM number
$sms_truncate_number = false;
$sms_truncate_number_length = 10;
# SMS token length
$sms_token_length = 6;
# Max attempts allowed for SMS token
$max_attempts = 5;
# Encryption, decryption keyphrase, required if $use_tokens = true and $crypt_tokens = true, or $use_sms, or $crypt_answer
# Please change it to anything long, random and complicated, you do not have to remember it
# Changing it will also invalidate all previous tokens and SMS codes
$keyphrase = "90apt"; //关键词
# Display menu on top
$show_menu = true; //显示菜单
# Logo
$logo = "images/logo.png"; //logo
# Background image
$background_image = "images/90apt.png"; //壁纸
参考链接:
https://blog.csdn.net/qq_33574974/article/details/128440776
https://blog.csdn.net/qq_43536701/article/details/112290651
https://blog.csdn.net/sunny05296/article/details/87634602
https://blog.csdn.net/jnloverll/article/details/120333488
https://www.cnblogs.com/cf-cf/p/12027495.html
https://hebye.com/docs/ldap/ldap-1d9e6e2dts5av
https://zhuanlan.zhihu.com/p/445700057?utm_id=0
https://cloud.tencent.com/developer/article/1937696
https://blog.csdn.net/weixin_44728369/article/details/117558938
https://blog.csdn.net/weixin_34163313/article/details/115243146
https://blog.csdn.net/hc1017/article/details/81293323?locationNum=1&fps=1
https://www.cnblogs.com/skymyyang/p/13653294.html
https://blog.csdn.net/qq461391728/article/details/115867721?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522162848744116780265427748%2522%252C%2522scm%2522%253A%252220140713.130102334..%2522%257D&request_id=162848744116780265427748&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2~all~sobaiduend~default-1-115867721.pc_search_result_control_group&utm_term=self+service+password+%E5%9F%9F%E8%B4%A6%E5%8F%B7&spm=1018.2226.3001.4187
https://blog.csdn.net/yanchuandong/article/details/119598665
https://blog.51cto.com/u_10630242/2538982


评论