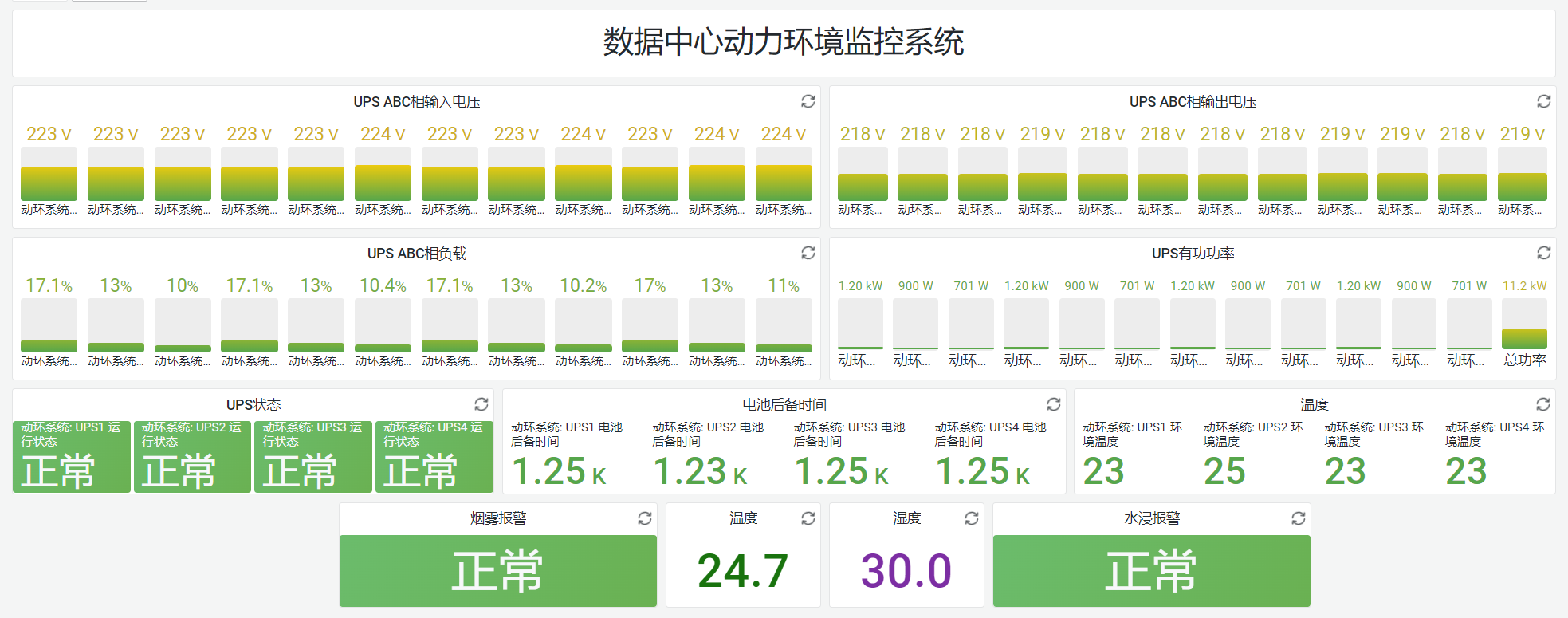
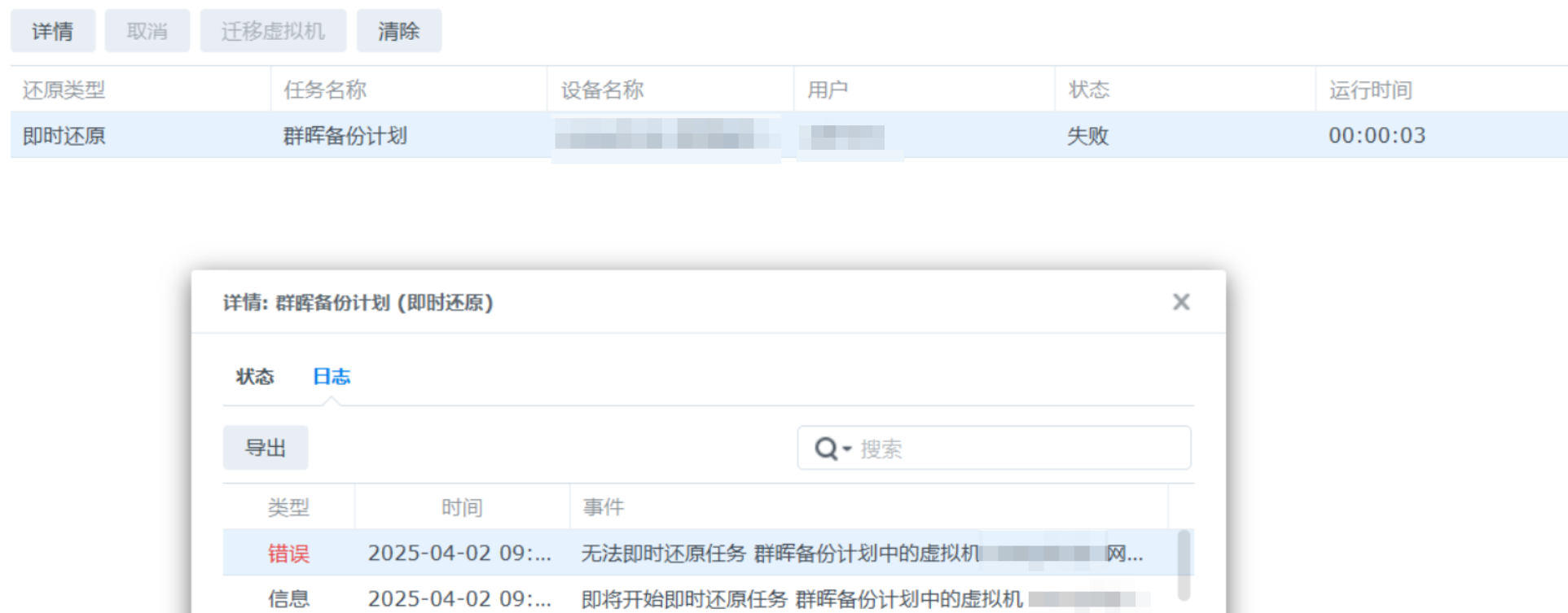
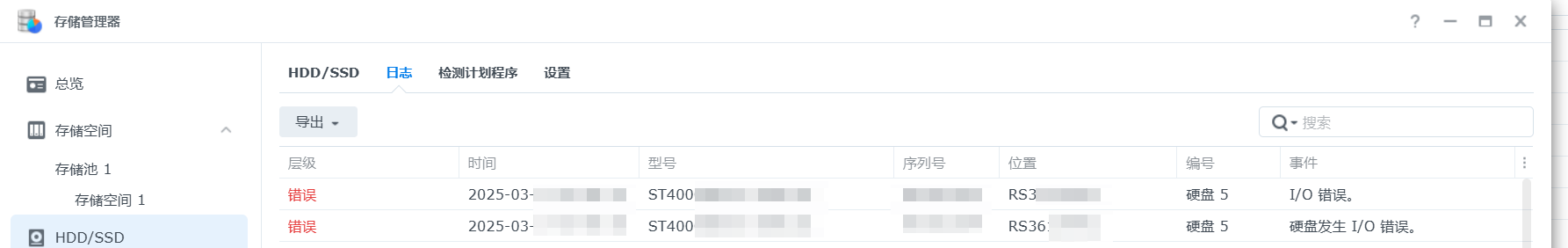
搜索到
317
篇与
的结果
-
 【90APT开源免费】第三代哈弗H6、哈弗大狗、H6经典版、坦克300华阳安波福车机开启无线ADB、升级地图、安装软件全流程 {message type="info" content="最后更新时间:2026.2.20"/}{message type="error" content="一旦导致车机损坏,4S更换费用为6000元,不包含工时费,请量力而行。"/}防骗指南:90APT教程、原理、软件完全开源公开免费,收费即为骗子{alert type="success"}哈弗车机技术交流QQ群:468902455 仅车友间技术讨论,不是提问群,不收费也不提供服务{/alert}{alert type="success"}本文适用于2025年升级后的(华阳100A、安波福403A) 第三代哈弗H6、哈弗大狗、H6经典版、部分型号的坦克300,本方案为密码开启或网络重定向智能手册更新包来安装无线ADB工具,实现车机的第三方软件安装和卸载,并将此行为定义为破解;对车机升级高德地图版本、安装自定义软件的行为,会降低车辆安全性,安装带有后门、或不稳定的软件,会对行车安全造成严重危害,对车机软件的修改造成故障,不属于车辆质保范畴,厂家和4S有权拒保,当你使用本文所提到的方法时,请确保自身能够承担相应后果。90APT是当前互联网唯一提供全套长城汽车第三代哈弗H6、哈弗大狗、H6经典版、部分型号的坦克300免费破解、升级地图、安装第三方软件方案的站点,王忘杰为其中一位免费开发者,更多开发者请查看90APT名人堂,90APT从未也不会授权任何人进行收费活动。当前抖音、QQ、微信等渠道出现的 “哈弗益达99元破解” “哈弗益达金牌代理” “哈弗益达空调插件宣传” 等 仿冒90APT开发者的宣传行为;再次声明,与90APT完全无关,90APT只提供免费教程,如出现财产损失,请向公安机关报案。{/alert}免责声明{alert type="success"}本文和工具不是为了让“车友”在使用车机时,自己进行破解使用。然而,我认为每个人都应该有测试和备份自己车机程序的选择。本文原理和工具完全免费,仅供研究车机原理测试使用,任何个人和组织不得以任何形式进行出售,任何商业行为与我本人没有任何关系,并非我的本意。如果你车机有任何问题,请前往长城4S店处理。本人不鼓励自行破解,对于不正确的使用,请自行承担责任。我不会同意以任何形式进行车机破解和不负责任的非法使用。当且仅当你拥有了软件的完整副本时,那么你可以将这些程序用于备份目的,且仅用于备份目的。最终用户许可协议(EULA)的影响如何,还有待观察,它不能取代法律,请务必牢记。此外,不对使用工具可能发生的损失或任何数据错误承担任何责任。如果你使用本工具,则表示你自动同意上述书面协议,因此,有关 EULA 影响的任何责任和后果请自负。根据 2013 年 1 月 30 日《计算机软件保护条例》的第十七条规定:为了学习和研究软件内含的设计思想和原理,通过安装、显示、传输或者存储软件等方式使用软件的,可以不经软件著作权人许可,不向其支付报酬。本文和工具作为原理研究、交流使用,完全免费,任何人不得用于商业用途,且下载后请务必于 24 小时内删除,如果是付费获得,那么你肯定被骗了!!!{/alert}{message type="info" content="灵控球2026年2月更新安波福方向盘变为空调控制,可能是bug,可临时关闭空调小组件等待厂家更新空调插件 手势划出空调遥控器 手势两次上划安波福空调插件 方向盘控制任意界面 悬浮歌词零控球 壁纸轮播灵控球 皮肤更新等新年皮肤........-当前最新版本华阳100A、安波福403A,目前无法通过在线更新,仅U盘升级升级1、修复7.1.7地图闪退2、修复安波福HUD不记忆3、修复HUD导航箭头缺失问题4、修复爱趣听播放暂停5、其他问题修复等"/}长城汽车哈弗售后体系{message type="info" content="1、对包修期内的产品提供质量保证: a.三包有效期实施2年或5万公里; b.在售PHEV车型:整车包修期实施6年或15万公里;动力电池包总成、驱动电机、电机控制器提供首任车主终身保修,非首任车主8年或15万公里保修; c.在售燃油车型:整车包修期实施3年或10万公里,其中发动机、变速箱提供首任车主终身保修(备注②); 注:①以上提及的三包期及包修期是指自车辆交付之日开始计算,时间或里程,两者以先到者为准,具体细则以随车三包凭证为准; ②已停产车型质保政策,具体细则以随车三包凭证为准。 2、如产品使用超出保修期,长城汽车股份有限公司提供维修、保养、救援、配件等有偿服务。"/}网盘资源网盘中软件均为网络收集,使用后果自负。90APT资源分享:123网盘 手机使用123网盘APP,转存到自己的网盘后下载不限速https://www.123912.com/s/UaOljv-vuRHv?提取码:kC2Nhttps://www.123865.com/s/UaOljv-vuRHv?提取码:kC2N百度网盘 不开会员下的慢链接: https://pan.baidu.com/s/1R1lEFLQ7l3K8NlbD9WX0fA?pwd=pqmc 提取码: pqmc车友资源分享:长城 & 哈弗 车机【系统包】、【软件包】【地图包】高德7.5/8.5/9.1安波福&华阳:下载链接:https://www.123865.com/s/S8YPvd-Vtfpd?pwd=29pk#备用链接:https://www.123684.com/s/S8YPvd-Vtfpd?pwd=29pk#第三方资源分享:与90APT无关,自行搜索使用,自行检测软件安全性迅雷APP或迅雷电脑版搜索 “迪粉玩车” “手机互联”红绿灯插件,免费音乐软件等软件尽在其中各种魔改地图 从QQ频道搜 #高德地图地图适配情况高德4.x 忽略高德6.x 忽略高德7.1.7 原厂全适配 HUD 驾驶屏 中控屏卡片 语音 没有绿灯读秒 没有巡航红绿灯高德7.5 全适配 HUD 驾驶屏 中控屏卡片 语音 巡航红绿灯高德8.1 忽略高德8.5 HUD 语音 巡航红绿灯高德9.1 HUD 语音 巡航红绿灯 红绿灯悬浮窗查看视频B站 王忘杰抖音 王忘杰{message type="success" content="90APT哈弗车友群名人堂 排名不分先后 "/}昵称项目The kingdom车友群创建者、早期免费教程公布者王忘杰90APT车机教程网站、笔记本一键包、服务器一键包、华阳原厂地图恢复哇偶工程模式安装助手扁豆docker版工程模式安装TEST华阳MCU二级密码解密Nintaus发现德赛西威无线ADB工具适配华阳安波福情深华阳无线ADB工具开发者kinsey车友群在线地图代码提供者小刀移除内置地图可随意安装地图软件Desire安波福原厂地图恢复小虫兮安波福系统签名提取Desire安波福签名高德地图,实现任意版本安装study安波福华阳空调插件余生余生高德7.5全适配星光星光高德7.5全适配低调魔改地图珂魔改地图null华阳安波福M键星键方向盘控制APP{lamp/}OTA后已知BUG1、灵控球白天夜间模式切换会导致亿连闪退,建议设置为白天或夜间模式,不自动切换2、安波福不能连接5GHz wifi据悉403A仍存在问题一、 原车功能1、原车地图7.1.7当前时间白天黄昏 导航模式才显示红绿灯 仪表屏和中控屏分别设置仪表盘:全屏、导航模式、3D模式、放大最大中控屏:全屏、3D模式当前时间夜间 导航模式才显示红绿灯 仪表屏和中控屏分别设置仪表盘:全屏、导航模式、3D模式、放大最大中控屏:全屏、3D模式仪表盘设置方向盘右侧房子按键+上下左右OK,选到导航全屏按右选择3D中控屏设置右侧GPS图标点击切换3D2、CarPlay、亿连若你对车机导航、音乐等功能不满意,推荐先使用原车手机互联功能,车机内置CarPlay、亿连,均支持有线和无线方式,详细请咨询长城汽车官方。示例:vivo车载 https://www.bilibili.com/video/BV1Li69YJEPG/ 示例:CarPlay{lamp/}二、安装无线ADB、升级地图、安装软件华阳车机1、华阳整体流程恭喜你,你和王工同款华阳车机,你的破解之路毫无阻碍基于难度考虑,仅保留 安卓手机OTG+公对公USB数据线 方法视频教程:B站https://www.bilibili.com/video/BV1qTXMYREnv/视频仅为操作指导,具有时效性,以网站最新文字教程为准1.1识别车机系统厂家分为安波福主机、华阳主机1.2安装无线ADB工具1)使用MCU密码配合 安卓手机OTG+公对公USB数据线,通过甲壳虫直接安装德赛西威无线ADB工具1.3升级地图使用应用管家移除内置地图后,即可任意安装卸载任何版本的高德地图1.4安装软件、调优连接无线ADB后,可通过手机甲壳虫软件安装、软件全屏调整等操作。2、详细步骤2.1识别车机系统打开车机系统设置-多次点击版本号出现密码框,输入密码,根据密码可判断车机版本adayo2002能够进入,为华阳车机2.2安装无线ADB工具1)使用MCU密码配合 安卓手机OTG + 公对公USB数据线,通过甲壳虫直接安装德赛西威无线ADB工具(开发者test)需要花4块钱购买一个 安卓OTG线 和 公对公USB数据线即可,我使用VIVO X80和红米note7pro测试没问题,华为手机可能不行系统设置-系统信息-连续点击系统版本号-输入密码 adayo2002 进入工厂模式-连续点击 MCU_Version 后面的版本号,输入密码(英文半角符号)@Fygw50*找到其他设置-就会出现usb mode device ADB开关,开启后即可通过USB连接车机手机,打开甲壳虫,插拔车机口的USB,检测到车机后,甲壳虫安装德赛西威无线ADB工具2.3华阳本地任意版本地图安装、返回原厂看视频 https://www.bilibili.com/video/BV1rNAkenEdr/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准2.3.1、基础准备车机准备车机安装德赛西威无线ADB工具、安装应用管家使用德赛西威无线ADB工具打开无线ADB(推荐),或在 应用管家-实验室中直接开启无线ADB(尝试)2.3.2、移除内置地图应用管家移除内置地图https://www.bilibili.com/video/BV1jEp9zJEKy/视频仅为操作指导,具有时效性,以网站最新文字教程为准应用管家-实验室-adb提权adbroot并挂载系统读写文件管理删除 根/system/app/Navigation删除 内置存储/amapauto9重启车机2.3.3、任意安装地图卸载上面移除内置地图之后就,后续安装地图就用甲壳虫、应用管家都行了车机连接手机热点,开启无线ADB开关,甲壳虫安装地图{alert type="warning"}每次安装地图后必须重启车机,给高德APP清数据给权限不重启车机,不会出现HUD不清除数据,旧地图数据可能干扰新地图不给权限,启动黑屏启动 设置app,找到高德应用,进行清数据,并把权限都打开{/alert}{message type="success" content="此步骤无风险"/}安装其他版本高德地图先从车机自带应用商店中卸载后,再用甲壳虫、应用商店等安装地图全屏、状态栏、导航栏显示如需全屏可以用甲壳虫安装一个应用管家,再设置应用沉浸式,此方法简单高德地图车机版声音调整若升级后高德地图8.1 8.5 9.1声音异常、无声、声音巨大、无法单独调整先清空高德地图APP数据、给予权限,然后调整声道,华阳高德声道第1个选11,第2个1,第7个1,第14个1,第17个1高德设置-播报图标连续点击10次-进入隐藏设置 https://www.bilibili.com/video/BV1GQApeEEgx/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准2.3.4、还原原厂7.1.7华阳直装版(开发者王忘杰){message type="success" content="此步骤无风险"/}在车机应用商店中卸载现有的高德地图甲壳虫连接车机后安装高德地图90apt华阳7.1.7.1234即可恢复原厂2.3.5、其他软件1)甲壳虫连接车机后直接安装2)甲壳虫连接车机后安装一个应用管家,再通过应用管家安装{lamp/}安波福车机你是安波福车机,你的破解之路会比较坎坷,教程均为群友制作,你加油吧如果你遇到搜不到5Gwifi、甲壳虫安装不上软件、调试模式安装不上、地图安装不上等问题,请你自己多试试或者换其他方法,因为安波福就这样。1、整体流程1.1识别车机系统厂家分为安波福主机、华阳主机1.2安装无线ADB工具安波福无线ADB工具用调试模式.apk安波福可以使用免费DNS安装调试模式开启无线ADB或自己购买云服务器使用90apt云服务器一键脚本安装开启无线ADB1.3升级地图可以直接安装安波福直装版地图1.4安装软件、调优连接无线ADB后,可通过应用管家、手机甲壳虫软件安装、软件全屏调整等操作。2、详细步骤2.1识别车机系统打开车机系统设置-多次点击版本号出现密码框,输入密码(英文半角符号),根据密码可判断车机版本*#34434ab *#4435ab *#1138ab *#1831aa能够进入,为安波福车机2.2安装无线ADB工具前提:安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限{message type="success" content="安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限"/}2.2.1、使用笔记本电脑安装无线ADB工具{message type="success" content="安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限"/}前提:安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限1)90APT笔记本一键包5.0更新时间2025.11.10从网盘下载,里面有说明https://www.bilibili.com/video/BV1dakkBSE2N/视频仅为操作指导,具有时效性,以网站最新文字教程为准2.2.2、使用DNS方法免费DNS免费DNS由车友提供,90apt不保证安全性和可用性当前暂无免费DNS47.108.148.36 已失效115.120.216.97 已失效111.229.158.142 已失效若你有国内外云服务器,可以联系我搭建免费DNS、共享给所有车友使用本DNS为免费DNS,由90APT.com提供搭建和教程,点击可查看详细教程,由于免费行为触动车圈某些收费人的利益,群号和DNS持续被举报,因此DNS失效时间不确定,收费均为骗子,谨防上当。手机DNS使用方法{message type="success" content="安波福安装调试模式,车机需要关闭移动网络,并给予智能手册存储权限,智能手册可能需要先更新一次"/}0) 安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限1) 准备一个wifi或手机热点,提供一个稳定的WIFI网络2) 准备第二部手机,第二部需要连接上面的wifi并且能够同时共享热点3) 第二部手机的wifi修改DNS域名为免费DNS的IP4) 车辆,车辆连接第二部手机的热点,点击智能手册,即可安装工装工程模式使用ADBDNS是否有效验证方法https://www.bilibili.com/video/BV1YnwVe9ERD/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准DNS简单测试这种是挂了,无响应nslookup dzsms.gwm.com.cn 81.68.72.155 DNS request timed out. timeout was 2 seconds. 服务器: UnKnown Address: 81.68.72.155 DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. *** 请求 UnKnown 超时这种是成功,返回了IPnslookup dzsms.gwm.com.cn 115.120.216.97 服务器: Address: 115.120.216.97 名称: dzsms.gwm.com.cn Address: 115.120.216.972.2.2、自行搭建无线ADB部署DNS服务器 (开发者王忘杰)可试用国内云服务器或购买国内外云服务器,需要公网IP服务器,90APT开发 更新时间2025.12.2,可安装无线ADB工具只支持almalinux8、anolis8、opencloudos8、oraclelinux8、rockylinux8、centos8操作系统,请先在云服务面板安全组放行 53UDP 80TCP 443TCP 8888TCP端口云服务器一键部署2.0 curl -O http://gwm.90apt.com/linux/gwm90apt2.sh;bash gwm90apt2.sh 云服务器一键部署1.0 curl -O http://gwm.90apt.com/linux/gwm90apt.sh;bash gwm90apt.sh无线ADB部署DNS服务器搭建 https://www.bilibili.com/video/BV16rcUeAEfP 视频仅为操作指导,具有时效性,以网站最新文字教程为准2.3安波福地图安装、返回原厂、安装第三方软件基于难度考虑,仅保留直装版方法2.3.1、直接安装安波福直装版地图1)直接安装安波福直装版地图,在90APT网盘中,安波福直装地图打开调试开关,使用手机甲壳虫或车机应用管家即可安装地图通过自带应用商店卸载后还能返回原厂2)你想自己制作直装版地图手机下载MT工具箱免费版、安波福签名文件https://www.bilibili.com/video/BV1XxXvY4EkC/视频仅为操作指导,具有时效性,以网站最新文字教程为准如果地图打不开黑屏退出,启动 系统设置,进行清数据给权限{alert type="warning"}每次安装地图后必须重启车机,给高德APP清数据给权限不重启车机,不会出现HUD不清除数据,旧地图数据可能干扰新地图不给权限,启动黑屏启动 设置app,找到高德应用,进行清数据,并把权限都打开{/alert}{message type="success" content="此步骤无风险"/}安装其他版本高德地图先从车机自带应用商店中卸载后,再用甲壳虫、应用商店等安装地图全屏、状态栏、导航栏显示如需全屏可以用甲壳虫安装一个应用管家,再设置应用沉浸式,此方法简单高德地图车机版声音调整若升级后高德地图8.1 8.5声 9.1音异常、无声、声音巨大、无法单独调整先清空高德地图APP数据、给予权限,然后调整声道,安波福高德声道第3个1即可,若还有异常可参考华阳设置自行调整。高德设置-播报图标连续点击10次-进入隐藏设置 https://www.bilibili.com/video/BV1GQApeEEgx/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准6)还原原厂7.1.7安波福直装版(开发者努力){message type="success" content="此步骤无风险"/}在车机应用商店中卸载现有的高德地图使用甲壳虫或应用管家直接安装 高德地图努力安波福7.1.7.1232原厂终极安全方法{message type="success" content="此步骤安全"/}去4S刷回原车系统{lamp/}更多玩法,成为高玩0、应用管家车机必备软件!1、软件全屏1)使用应用管家设置沉浸式2)甲壳虫运行ADB命令软件名从甲壳虫查全屏沉浸: adb shell settings put global policy_control immersive.full=软件1,软件2 沉浸状态栏: adb shell settings put global policy_control immersive.status=软件1,软件2 沉浸导航栏: adb shell settings put global policy_control immersive.navigation=软件1,软件2 我们还可以单独控制哪些app不沉浸,例如以下代码设置google即时桌面不沉浸,其他程序沉浸: adb shell settings put global policy_control immersive.full=apps,-com.google.android.googlequicksearchbox 如果想恢复到正常模式,运行下面的代码: adb shell settings put global policy_control null2、亿连自动启动安装自动启动APK,使用ADB命令设置软件全屏,勾选亿连设置自动启动即可3、CarLife群里和网盘中有此应用,手机互联更快更稳定4、百度地图车机版32位32位版本不卡顿,只用来巡航,自动进入巡航,显示的红绿灯比高德多,能显示前面三个路口的红绿灯,非常好声道自己测试下网盘里32位百嘟地图20.10.2小迪悬浮(氢)车道级工程去更新5、安波福华阳U盘安装OTA更新固件包视频教程https://www.bilibili.com/video/BV1F36oYPE1M/视频仅为操作指导,具有时效性,以网站最新文字教程为准U盘使用分区助手,调整为MBR分区格式,分区格式化为FAT32华阳目录格式:U盘根目录下只有一个complete_adayo_update_files文件夹,文件夹中只有两个文件U盘根目录 - complete_adayo_update_files - HS5003A_V4.01.13.iso HUT_SYS_OS_V4.01.13.zip安波福目录格式:U盘根目录下直接存放boot、CHWM_V3等11个文件U盘根目录 - boot CHWM_V3 CHWM_V3_64 emergency extbin ota_transfer R7 system vbmeta vendor ota_transfer_attr.txt{lamp/}三、高级玩法1、一部安卓手机实现服务器功能,直接给车机装无线ADB调试工具{message type="warning" content="此步骤可能有风险,不是高手别整"/}手机插SIM卡后开热点,车机连接热点,点击智慧手册即可 https://www.bilibili.com/video/BV14vk2Y9EzA/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准注意,手机root后失去保修,量力而行。 技术架构部署服务我使用的是红米note7pro,解锁BL安装面具magisk,注入boot,刷入,获取root权限tsu后成功获取root权限激活自带的Systemless Hosts模块下面文件均需root权限编辑sudo su修改hosts文件,劫持dzsms.gwm.com.cn请求路径 /data/adb/modules/hosts/system/etc/hostsIP为手机热点的IP,可以用其他手机连上看看网关我这里红米为192.168.43.1 dzsms.gwm.com.cn保存重启手机,面具会将这个hosts文件作为系统请求的hosts部署nginx服务,将需要的代码和脚本都放入指定手机中,使用root运行nginx测试安装nginxpkg install nginx无线ADB工具放置位置,命名为 3.0.apk/data/data/com.termux/files/usr/share/nginx/html/3.0.apkssl证书放置位置/data/data/com.termux/files/usr/etc/nginx/cert.pem/data/data/com.termux/files/usr/etc/nginx/key.pem配置文件/data/data/com.termux/files/usr/etc/nginx/nginx.confuser root; worker_processes 1; #error_log logs/error.log; #error_log logs/error.log notice; #error_log logs/error.log info; #pid logs/nginx.pid; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; #log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; sendfile on; #tcp_nopush on; #keepalive_timeout 0; keepalive_timeout 65; #gzip on; server { listen 80; listen 443 ssl; server_name gwm.90apt.com; server_name dzsms.gwm.com.cn; server_name hzsms.gwm.com.cn; ssl_certificate /data/data/com.termux/files/usr/etc/nginx/cert.pem; ssl_certificate_key /data/data/com.termux/files/usr/etc/nginx/key.pem; ssl_prefer_server_ciphers on; ssl_ciphers ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_session_cache shared:SSL:5m; ssl_session_timeout 5m; keepalive_timeout 75s; keepalive_requests 100; root /data/data/com.termux/files/usr/share/nginx/html; gzip off; charset utf-8; location / { index index.html index.htm index.php; autoindex on; charset utf-8; } location /apiv2/car_apk_update { default_type application/json; return 200 '{ "code": 200, "message": "\u67e5\u8be2\u6210\u529f", "data": { "apk_version": "99999", "apk_url": "https://dzsms.gwm.com.cn/3.0.apk", "apk_msg": "90APT提供,不欢迎哈弗益达使用", "isUpdate": "Yes", "apk_forceUpdate": "Yes", "notice": { "vin_notice": [ "VIN码可以在仪表板左上方(前风挡玻璃后面)和车辆铭牌上获得。", "本应用适用于2019年及之后生产的车型。" ], "add_notice": [ "制造年月可通过车辆铭牌获得。", "本应用适用于2019年及之后生产的车型。" ] }, "notice_en": { "vin_notice": [ ], "add_notice": [ "The date can be obtained from the certification label." ] } } }'; }} # another virtual host using mix of IP-, name-, and port-based configuration # #server { # listen 8000; # listen somename:8080; # server_name somename alias another.alias; # location / { # root html; # index index.html index.htm; # } #} # HTTPS server # #server { # listen 443 ssl; # server_name localhost; # ssl_certificate cert.pem; # ssl_certificate_key cert.key; # ssl_session_cache shared:SSL:1m; # ssl_session_timeout 5m; # ssl_ciphers HIGH:!aNULL:!MD5; # ssl_prefer_server_ciphers on; # location / { # root html; # index index.html index.htm; # } #} } 使用root权限启动nginxsudo nginx此手机开启热点后,其他设备连接后访问https://dzsms.gwm.com.cn/ 能显示3.0.apk即为成功直接实战手机升级高德地图8.1长城三代哈弗H6哈弗大狗坦克300安波福华阳笔记本一键部署3.1DNS工程模式跑代码 https://www.bilibili.com/video/BV14vk2Y9EzA/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准2、原理解析https://www.bilibili.com/video/BV1eXCAYjEi5/ ADB在哪里在第三代哈弗H6车机中,ADB程序位于工程模式中,在2021、2022出厂的车固件中内置,2023年起移除;这个程序只有厂家有,我们可以从2023之前的系统中,用ADB工具将工程模式APP导出。完成第一项:获得ADB程序车机有没有对外请求数据由于没有了ADB程序,我们是无法安装工程模式到车机中的,这时候就需要利用哈弗车机的一个漏洞,即智能手册APP证书无验证漏洞。进入智能手册APP后,APP会向哈弗服务器一个URL发送请求,用来请求最新版本,让车机WIFI连接到我们的设备进行抓包,查看请求状态,智能手册APP会解析JSON格式的回复内容判断是否下载APK升级。完成第二项:获取一个系统漏洞怎么把ADB装进去我们参照官方服务器,自行搭建DNS和web服务器,让车机连到我们的DNS服务器上,进行请求的劫持,这样,我们自己的APP就会被以程序更新的方式发送到车机中进行安装。完成第三项:将ADB注入到车机中,重新取得ADB权限ADB安装软件开启无线ADB或使用有线ADB,都可以使用ADB工具进行软件安装,如安卓内置命令pm、电脑搞机工具箱、手机甲壳虫。3、高德地图车机版去签名验证、修改导航栏遮蔽去签名验证使用apktool M 删除签名校验使用MT管理器打开classes.dex,搜索apks将文件最后的0x0改为0x1删除包中的 lib\armeabi-v7a\libsgsecuritybody.so文件保存编译即可修改导航栏遮蔽方法一(不推荐)https://www.bilibili.com/video/BV1Y2ApeDExW/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准用Android Killer修改地图文件配置文件位置res\layout\main_map_view.xmlbackground_dark 框架层ui_surface UI层map_surface 地图层android:layout_marginLeft="100.0dip" 左侧避让100dipandroid:layout_marginTop="64.0dip" 上侧避让100dip例如左侧地图层规避、上侧元素层规避 <com.autonavi.amapauto.view.MapSurfaceViewEx android:id="@id/map_surface" android:layout_width="fill_parent" android:layout_height="fill_parent" android:layout_marginLeft="100.0dip" /> <SurfaceView android:id="@id/ui_surface" android:layout_width="fill_parent" android:layout_height="fill_parent" android:layout_marginLeft="100.0dip" android:layout_marginTop="64.0dip" />4) 使用MT管理器 重新签名修改导航栏遮蔽方法二(推荐)使用MT管理器导出FuncConfig.dat位于高德apk/assets/res/HmiRes/使用FuncConfig.dat 在线加解密 https://fun.cccyn.cc/解密出txt后,修改DysmorphismInfo,四个数字是左上右下的边距,statusBarColor是华阳的状态栏透明华阳左侧上侧规避状态栏透明 "DysmorphismInfo": "60,50,0,0", "statusBarColor": "-1",安波福左侧上侧规避状态栏透明 "DysmorphismInfo": "60,50,0,0", "statusBarColor": "0", "IgnoreInvalidLaneExport": "0", "ImmersiveMode": "9472", 将FuncConfig.txt加密成dat文件,塞回去自动编译即可4、把无线ADB软件移动到系统目录,还原不丢失termux中执行连接IP,写无线ADB开关里提示的IPadb connect IP地址查看当前连接的设备是否连接成功,成功后进行后续操作adb devices{message type="info" content="此步骤无风险,但可能移除后无线ADB软件就找不到了,此步骤可以不执行"/}termux中执行adb root;adb wait-for-device;adb remount;adb root;adb wait-for-device;adb remount;adb shell mv /data/app/com.example.xadb* /system/app/;adb shell mv /data/app/com.tencent.sotainstaller* /system/app/;adb shell pm path com.tencent.sotainstaller;adb shell pm path com.example.xadb5、使用termux移除内置地图adb shell pm clear com.autonavi.amapauto;adb root;adb wait-for-device;adb remount;adb root;adb wait-for-device;adb remount;adb shell am force-stop com.autonavi.amapauto;adb shell am force-stop com.autonavi.amapauto;adb shell rm -rf /system/app/Navigation;adb shell rm -rf /system/app/Navigation;adb shell rm -rf /system/app/AutoMap;adb shell rm -rf /system/app/AutoMap;adb reboot{lamp/}四、小结哈哈哈哈哈哈哈
【90APT开源免费】第三代哈弗H6、哈弗大狗、H6经典版、坦克300华阳安波福车机开启无线ADB、升级地图、安装软件全流程 {message type="info" content="最后更新时间:2026.2.20"/}{message type="error" content="一旦导致车机损坏,4S更换费用为6000元,不包含工时费,请量力而行。"/}防骗指南:90APT教程、原理、软件完全开源公开免费,收费即为骗子{alert type="success"}哈弗车机技术交流QQ群:468902455 仅车友间技术讨论,不是提问群,不收费也不提供服务{/alert}{alert type="success"}本文适用于2025年升级后的(华阳100A、安波福403A) 第三代哈弗H6、哈弗大狗、H6经典版、部分型号的坦克300,本方案为密码开启或网络重定向智能手册更新包来安装无线ADB工具,实现车机的第三方软件安装和卸载,并将此行为定义为破解;对车机升级高德地图版本、安装自定义软件的行为,会降低车辆安全性,安装带有后门、或不稳定的软件,会对行车安全造成严重危害,对车机软件的修改造成故障,不属于车辆质保范畴,厂家和4S有权拒保,当你使用本文所提到的方法时,请确保自身能够承担相应后果。90APT是当前互联网唯一提供全套长城汽车第三代哈弗H6、哈弗大狗、H6经典版、部分型号的坦克300免费破解、升级地图、安装第三方软件方案的站点,王忘杰为其中一位免费开发者,更多开发者请查看90APT名人堂,90APT从未也不会授权任何人进行收费活动。当前抖音、QQ、微信等渠道出现的 “哈弗益达99元破解” “哈弗益达金牌代理” “哈弗益达空调插件宣传” 等 仿冒90APT开发者的宣传行为;再次声明,与90APT完全无关,90APT只提供免费教程,如出现财产损失,请向公安机关报案。{/alert}免责声明{alert type="success"}本文和工具不是为了让“车友”在使用车机时,自己进行破解使用。然而,我认为每个人都应该有测试和备份自己车机程序的选择。本文原理和工具完全免费,仅供研究车机原理测试使用,任何个人和组织不得以任何形式进行出售,任何商业行为与我本人没有任何关系,并非我的本意。如果你车机有任何问题,请前往长城4S店处理。本人不鼓励自行破解,对于不正确的使用,请自行承担责任。我不会同意以任何形式进行车机破解和不负责任的非法使用。当且仅当你拥有了软件的完整副本时,那么你可以将这些程序用于备份目的,且仅用于备份目的。最终用户许可协议(EULA)的影响如何,还有待观察,它不能取代法律,请务必牢记。此外,不对使用工具可能发生的损失或任何数据错误承担任何责任。如果你使用本工具,则表示你自动同意上述书面协议,因此,有关 EULA 影响的任何责任和后果请自负。根据 2013 年 1 月 30 日《计算机软件保护条例》的第十七条规定:为了学习和研究软件内含的设计思想和原理,通过安装、显示、传输或者存储软件等方式使用软件的,可以不经软件著作权人许可,不向其支付报酬。本文和工具作为原理研究、交流使用,完全免费,任何人不得用于商业用途,且下载后请务必于 24 小时内删除,如果是付费获得,那么你肯定被骗了!!!{/alert}{message type="info" content="灵控球2026年2月更新安波福方向盘变为空调控制,可能是bug,可临时关闭空调小组件等待厂家更新空调插件 手势划出空调遥控器 手势两次上划安波福空调插件 方向盘控制任意界面 悬浮歌词零控球 壁纸轮播灵控球 皮肤更新等新年皮肤........-当前最新版本华阳100A、安波福403A,目前无法通过在线更新,仅U盘升级升级1、修复7.1.7地图闪退2、修复安波福HUD不记忆3、修复HUD导航箭头缺失问题4、修复爱趣听播放暂停5、其他问题修复等"/}长城汽车哈弗售后体系{message type="info" content="1、对包修期内的产品提供质量保证: a.三包有效期实施2年或5万公里; b.在售PHEV车型:整车包修期实施6年或15万公里;动力电池包总成、驱动电机、电机控制器提供首任车主终身保修,非首任车主8年或15万公里保修; c.在售燃油车型:整车包修期实施3年或10万公里,其中发动机、变速箱提供首任车主终身保修(备注②); 注:①以上提及的三包期及包修期是指自车辆交付之日开始计算,时间或里程,两者以先到者为准,具体细则以随车三包凭证为准; ②已停产车型质保政策,具体细则以随车三包凭证为准。 2、如产品使用超出保修期,长城汽车股份有限公司提供维修、保养、救援、配件等有偿服务。"/}网盘资源网盘中软件均为网络收集,使用后果自负。90APT资源分享:123网盘 手机使用123网盘APP,转存到自己的网盘后下载不限速https://www.123912.com/s/UaOljv-vuRHv?提取码:kC2Nhttps://www.123865.com/s/UaOljv-vuRHv?提取码:kC2N百度网盘 不开会员下的慢链接: https://pan.baidu.com/s/1R1lEFLQ7l3K8NlbD9WX0fA?pwd=pqmc 提取码: pqmc车友资源分享:长城 & 哈弗 车机【系统包】、【软件包】【地图包】高德7.5/8.5/9.1安波福&华阳:下载链接:https://www.123865.com/s/S8YPvd-Vtfpd?pwd=29pk#备用链接:https://www.123684.com/s/S8YPvd-Vtfpd?pwd=29pk#第三方资源分享:与90APT无关,自行搜索使用,自行检测软件安全性迅雷APP或迅雷电脑版搜索 “迪粉玩车” “手机互联”红绿灯插件,免费音乐软件等软件尽在其中各种魔改地图 从QQ频道搜 #高德地图地图适配情况高德4.x 忽略高德6.x 忽略高德7.1.7 原厂全适配 HUD 驾驶屏 中控屏卡片 语音 没有绿灯读秒 没有巡航红绿灯高德7.5 全适配 HUD 驾驶屏 中控屏卡片 语音 巡航红绿灯高德8.1 忽略高德8.5 HUD 语音 巡航红绿灯高德9.1 HUD 语音 巡航红绿灯 红绿灯悬浮窗查看视频B站 王忘杰抖音 王忘杰{message type="success" content="90APT哈弗车友群名人堂 排名不分先后 "/}昵称项目The kingdom车友群创建者、早期免费教程公布者王忘杰90APT车机教程网站、笔记本一键包、服务器一键包、华阳原厂地图恢复哇偶工程模式安装助手扁豆docker版工程模式安装TEST华阳MCU二级密码解密Nintaus发现德赛西威无线ADB工具适配华阳安波福情深华阳无线ADB工具开发者kinsey车友群在线地图代码提供者小刀移除内置地图可随意安装地图软件Desire安波福原厂地图恢复小虫兮安波福系统签名提取Desire安波福签名高德地图,实现任意版本安装study安波福华阳空调插件余生余生高德7.5全适配星光星光高德7.5全适配低调魔改地图珂魔改地图null华阳安波福M键星键方向盘控制APP{lamp/}OTA后已知BUG1、灵控球白天夜间模式切换会导致亿连闪退,建议设置为白天或夜间模式,不自动切换2、安波福不能连接5GHz wifi据悉403A仍存在问题一、 原车功能1、原车地图7.1.7当前时间白天黄昏 导航模式才显示红绿灯 仪表屏和中控屏分别设置仪表盘:全屏、导航模式、3D模式、放大最大中控屏:全屏、3D模式当前时间夜间 导航模式才显示红绿灯 仪表屏和中控屏分别设置仪表盘:全屏、导航模式、3D模式、放大最大中控屏:全屏、3D模式仪表盘设置方向盘右侧房子按键+上下左右OK,选到导航全屏按右选择3D中控屏设置右侧GPS图标点击切换3D2、CarPlay、亿连若你对车机导航、音乐等功能不满意,推荐先使用原车手机互联功能,车机内置CarPlay、亿连,均支持有线和无线方式,详细请咨询长城汽车官方。示例:vivo车载 https://www.bilibili.com/video/BV1Li69YJEPG/ 示例:CarPlay{lamp/}二、安装无线ADB、升级地图、安装软件华阳车机1、华阳整体流程恭喜你,你和王工同款华阳车机,你的破解之路毫无阻碍基于难度考虑,仅保留 安卓手机OTG+公对公USB数据线 方法视频教程:B站https://www.bilibili.com/video/BV1qTXMYREnv/视频仅为操作指导,具有时效性,以网站最新文字教程为准1.1识别车机系统厂家分为安波福主机、华阳主机1.2安装无线ADB工具1)使用MCU密码配合 安卓手机OTG+公对公USB数据线,通过甲壳虫直接安装德赛西威无线ADB工具1.3升级地图使用应用管家移除内置地图后,即可任意安装卸载任何版本的高德地图1.4安装软件、调优连接无线ADB后,可通过手机甲壳虫软件安装、软件全屏调整等操作。2、详细步骤2.1识别车机系统打开车机系统设置-多次点击版本号出现密码框,输入密码,根据密码可判断车机版本adayo2002能够进入,为华阳车机2.2安装无线ADB工具1)使用MCU密码配合 安卓手机OTG + 公对公USB数据线,通过甲壳虫直接安装德赛西威无线ADB工具(开发者test)需要花4块钱购买一个 安卓OTG线 和 公对公USB数据线即可,我使用VIVO X80和红米note7pro测试没问题,华为手机可能不行系统设置-系统信息-连续点击系统版本号-输入密码 adayo2002 进入工厂模式-连续点击 MCU_Version 后面的版本号,输入密码(英文半角符号)@Fygw50*找到其他设置-就会出现usb mode device ADB开关,开启后即可通过USB连接车机手机,打开甲壳虫,插拔车机口的USB,检测到车机后,甲壳虫安装德赛西威无线ADB工具2.3华阳本地任意版本地图安装、返回原厂看视频 https://www.bilibili.com/video/BV1rNAkenEdr/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准2.3.1、基础准备车机准备车机安装德赛西威无线ADB工具、安装应用管家使用德赛西威无线ADB工具打开无线ADB(推荐),或在 应用管家-实验室中直接开启无线ADB(尝试)2.3.2、移除内置地图应用管家移除内置地图https://www.bilibili.com/video/BV1jEp9zJEKy/视频仅为操作指导,具有时效性,以网站最新文字教程为准应用管家-实验室-adb提权adbroot并挂载系统读写文件管理删除 根/system/app/Navigation删除 内置存储/amapauto9重启车机2.3.3、任意安装地图卸载上面移除内置地图之后就,后续安装地图就用甲壳虫、应用管家都行了车机连接手机热点,开启无线ADB开关,甲壳虫安装地图{alert type="warning"}每次安装地图后必须重启车机,给高德APP清数据给权限不重启车机,不会出现HUD不清除数据,旧地图数据可能干扰新地图不给权限,启动黑屏启动 设置app,找到高德应用,进行清数据,并把权限都打开{/alert}{message type="success" content="此步骤无风险"/}安装其他版本高德地图先从车机自带应用商店中卸载后,再用甲壳虫、应用商店等安装地图全屏、状态栏、导航栏显示如需全屏可以用甲壳虫安装一个应用管家,再设置应用沉浸式,此方法简单高德地图车机版声音调整若升级后高德地图8.1 8.5 9.1声音异常、无声、声音巨大、无法单独调整先清空高德地图APP数据、给予权限,然后调整声道,华阳高德声道第1个选11,第2个1,第7个1,第14个1,第17个1高德设置-播报图标连续点击10次-进入隐藏设置 https://www.bilibili.com/video/BV1GQApeEEgx/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准2.3.4、还原原厂7.1.7华阳直装版(开发者王忘杰){message type="success" content="此步骤无风险"/}在车机应用商店中卸载现有的高德地图甲壳虫连接车机后安装高德地图90apt华阳7.1.7.1234即可恢复原厂2.3.5、其他软件1)甲壳虫连接车机后直接安装2)甲壳虫连接车机后安装一个应用管家,再通过应用管家安装{lamp/}安波福车机你是安波福车机,你的破解之路会比较坎坷,教程均为群友制作,你加油吧如果你遇到搜不到5Gwifi、甲壳虫安装不上软件、调试模式安装不上、地图安装不上等问题,请你自己多试试或者换其他方法,因为安波福就这样。1、整体流程1.1识别车机系统厂家分为安波福主机、华阳主机1.2安装无线ADB工具安波福无线ADB工具用调试模式.apk安波福可以使用免费DNS安装调试模式开启无线ADB或自己购买云服务器使用90apt云服务器一键脚本安装开启无线ADB1.3升级地图可以直接安装安波福直装版地图1.4安装软件、调优连接无线ADB后,可通过应用管家、手机甲壳虫软件安装、软件全屏调整等操作。2、详细步骤2.1识别车机系统打开车机系统设置-多次点击版本号出现密码框,输入密码(英文半角符号),根据密码可判断车机版本*#34434ab *#4435ab *#1138ab *#1831aa能够进入,为安波福车机2.2安装无线ADB工具前提:安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限{message type="success" content="安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限"/}2.2.1、使用笔记本电脑安装无线ADB工具{message type="success" content="安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限"/}前提:安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限1)90APT笔记本一键包5.0更新时间2025.11.10从网盘下载,里面有说明https://www.bilibili.com/video/BV1dakkBSE2N/视频仅为操作指导,具有时效性,以网站最新文字教程为准2.2.2、使用DNS方法免费DNS免费DNS由车友提供,90apt不保证安全性和可用性当前暂无免费DNS47.108.148.36 已失效115.120.216.97 已失效111.229.158.142 已失效若你有国内外云服务器,可以联系我搭建免费DNS、共享给所有车友使用本DNS为免费DNS,由90APT.com提供搭建和教程,点击可查看详细教程,由于免费行为触动车圈某些收费人的利益,群号和DNS持续被举报,因此DNS失效时间不确定,收费均为骗子,谨防上当。手机DNS使用方法{message type="success" content="安波福安装调试模式,车机需要关闭移动网络,并给予智能手册存储权限,智能手册可能需要先更新一次"/}0) 安波福安装调试模式,车机使用移动数据,打开“智能手册”正确选择,更新一次数据;然后关闭移动网络,并给予智能手册存储权限1) 准备一个wifi或手机热点,提供一个稳定的WIFI网络2) 准备第二部手机,第二部需要连接上面的wifi并且能够同时共享热点3) 第二部手机的wifi修改DNS域名为免费DNS的IP4) 车辆,车辆连接第二部手机的热点,点击智能手册,即可安装工装工程模式使用ADBDNS是否有效验证方法https://www.bilibili.com/video/BV1YnwVe9ERD/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准DNS简单测试这种是挂了,无响应nslookup dzsms.gwm.com.cn 81.68.72.155 DNS request timed out. timeout was 2 seconds. 服务器: UnKnown Address: 81.68.72.155 DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. *** 请求 UnKnown 超时这种是成功,返回了IPnslookup dzsms.gwm.com.cn 115.120.216.97 服务器: Address: 115.120.216.97 名称: dzsms.gwm.com.cn Address: 115.120.216.972.2.2、自行搭建无线ADB部署DNS服务器 (开发者王忘杰)可试用国内云服务器或购买国内外云服务器,需要公网IP服务器,90APT开发 更新时间2025.12.2,可安装无线ADB工具只支持almalinux8、anolis8、opencloudos8、oraclelinux8、rockylinux8、centos8操作系统,请先在云服务面板安全组放行 53UDP 80TCP 443TCP 8888TCP端口云服务器一键部署2.0 curl -O http://gwm.90apt.com/linux/gwm90apt2.sh;bash gwm90apt2.sh 云服务器一键部署1.0 curl -O http://gwm.90apt.com/linux/gwm90apt.sh;bash gwm90apt.sh无线ADB部署DNS服务器搭建 https://www.bilibili.com/video/BV16rcUeAEfP 视频仅为操作指导,具有时效性,以网站最新文字教程为准2.3安波福地图安装、返回原厂、安装第三方软件基于难度考虑,仅保留直装版方法2.3.1、直接安装安波福直装版地图1)直接安装安波福直装版地图,在90APT网盘中,安波福直装地图打开调试开关,使用手机甲壳虫或车机应用管家即可安装地图通过自带应用商店卸载后还能返回原厂2)你想自己制作直装版地图手机下载MT工具箱免费版、安波福签名文件https://www.bilibili.com/video/BV1XxXvY4EkC/视频仅为操作指导,具有时效性,以网站最新文字教程为准如果地图打不开黑屏退出,启动 系统设置,进行清数据给权限{alert type="warning"}每次安装地图后必须重启车机,给高德APP清数据给权限不重启车机,不会出现HUD不清除数据,旧地图数据可能干扰新地图不给权限,启动黑屏启动 设置app,找到高德应用,进行清数据,并把权限都打开{/alert}{message type="success" content="此步骤无风险"/}安装其他版本高德地图先从车机自带应用商店中卸载后,再用甲壳虫、应用商店等安装地图全屏、状态栏、导航栏显示如需全屏可以用甲壳虫安装一个应用管家,再设置应用沉浸式,此方法简单高德地图车机版声音调整若升级后高德地图8.1 8.5声 9.1音异常、无声、声音巨大、无法单独调整先清空高德地图APP数据、给予权限,然后调整声道,安波福高德声道第3个1即可,若还有异常可参考华阳设置自行调整。高德设置-播报图标连续点击10次-进入隐藏设置 https://www.bilibili.com/video/BV1GQApeEEgx/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准6)还原原厂7.1.7安波福直装版(开发者努力){message type="success" content="此步骤无风险"/}在车机应用商店中卸载现有的高德地图使用甲壳虫或应用管家直接安装 高德地图努力安波福7.1.7.1232原厂终极安全方法{message type="success" content="此步骤安全"/}去4S刷回原车系统{lamp/}更多玩法,成为高玩0、应用管家车机必备软件!1、软件全屏1)使用应用管家设置沉浸式2)甲壳虫运行ADB命令软件名从甲壳虫查全屏沉浸: adb shell settings put global policy_control immersive.full=软件1,软件2 沉浸状态栏: adb shell settings put global policy_control immersive.status=软件1,软件2 沉浸导航栏: adb shell settings put global policy_control immersive.navigation=软件1,软件2 我们还可以单独控制哪些app不沉浸,例如以下代码设置google即时桌面不沉浸,其他程序沉浸: adb shell settings put global policy_control immersive.full=apps,-com.google.android.googlequicksearchbox 如果想恢复到正常模式,运行下面的代码: adb shell settings put global policy_control null2、亿连自动启动安装自动启动APK,使用ADB命令设置软件全屏,勾选亿连设置自动启动即可3、CarLife群里和网盘中有此应用,手机互联更快更稳定4、百度地图车机版32位32位版本不卡顿,只用来巡航,自动进入巡航,显示的红绿灯比高德多,能显示前面三个路口的红绿灯,非常好声道自己测试下网盘里32位百嘟地图20.10.2小迪悬浮(氢)车道级工程去更新5、安波福华阳U盘安装OTA更新固件包视频教程https://www.bilibili.com/video/BV1F36oYPE1M/视频仅为操作指导,具有时效性,以网站最新文字教程为准U盘使用分区助手,调整为MBR分区格式,分区格式化为FAT32华阳目录格式:U盘根目录下只有一个complete_adayo_update_files文件夹,文件夹中只有两个文件U盘根目录 - complete_adayo_update_files - HS5003A_V4.01.13.iso HUT_SYS_OS_V4.01.13.zip安波福目录格式:U盘根目录下直接存放boot、CHWM_V3等11个文件U盘根目录 - boot CHWM_V3 CHWM_V3_64 emergency extbin ota_transfer R7 system vbmeta vendor ota_transfer_attr.txt{lamp/}三、高级玩法1、一部安卓手机实现服务器功能,直接给车机装无线ADB调试工具{message type="warning" content="此步骤可能有风险,不是高手别整"/}手机插SIM卡后开热点,车机连接热点,点击智慧手册即可 https://www.bilibili.com/video/BV14vk2Y9EzA/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准注意,手机root后失去保修,量力而行。 技术架构部署服务我使用的是红米note7pro,解锁BL安装面具magisk,注入boot,刷入,获取root权限tsu后成功获取root权限激活自带的Systemless Hosts模块下面文件均需root权限编辑sudo su修改hosts文件,劫持dzsms.gwm.com.cn请求路径 /data/adb/modules/hosts/system/etc/hostsIP为手机热点的IP,可以用其他手机连上看看网关我这里红米为192.168.43.1 dzsms.gwm.com.cn保存重启手机,面具会将这个hosts文件作为系统请求的hosts部署nginx服务,将需要的代码和脚本都放入指定手机中,使用root运行nginx测试安装nginxpkg install nginx无线ADB工具放置位置,命名为 3.0.apk/data/data/com.termux/files/usr/share/nginx/html/3.0.apkssl证书放置位置/data/data/com.termux/files/usr/etc/nginx/cert.pem/data/data/com.termux/files/usr/etc/nginx/key.pem配置文件/data/data/com.termux/files/usr/etc/nginx/nginx.confuser root; worker_processes 1; #error_log logs/error.log; #error_log logs/error.log notice; #error_log logs/error.log info; #pid logs/nginx.pid; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; #log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; sendfile on; #tcp_nopush on; #keepalive_timeout 0; keepalive_timeout 65; #gzip on; server { listen 80; listen 443 ssl; server_name gwm.90apt.com; server_name dzsms.gwm.com.cn; server_name hzsms.gwm.com.cn; ssl_certificate /data/data/com.termux/files/usr/etc/nginx/cert.pem; ssl_certificate_key /data/data/com.termux/files/usr/etc/nginx/key.pem; ssl_prefer_server_ciphers on; ssl_ciphers ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_session_cache shared:SSL:5m; ssl_session_timeout 5m; keepalive_timeout 75s; keepalive_requests 100; root /data/data/com.termux/files/usr/share/nginx/html; gzip off; charset utf-8; location / { index index.html index.htm index.php; autoindex on; charset utf-8; } location /apiv2/car_apk_update { default_type application/json; return 200 '{ "code": 200, "message": "\u67e5\u8be2\u6210\u529f", "data": { "apk_version": "99999", "apk_url": "https://dzsms.gwm.com.cn/3.0.apk", "apk_msg": "90APT提供,不欢迎哈弗益达使用", "isUpdate": "Yes", "apk_forceUpdate": "Yes", "notice": { "vin_notice": [ "VIN码可以在仪表板左上方(前风挡玻璃后面)和车辆铭牌上获得。", "本应用适用于2019年及之后生产的车型。" ], "add_notice": [ "制造年月可通过车辆铭牌获得。", "本应用适用于2019年及之后生产的车型。" ] }, "notice_en": { "vin_notice": [ ], "add_notice": [ "The date can be obtained from the certification label." ] } } }'; }} # another virtual host using mix of IP-, name-, and port-based configuration # #server { # listen 8000; # listen somename:8080; # server_name somename alias another.alias; # location / { # root html; # index index.html index.htm; # } #} # HTTPS server # #server { # listen 443 ssl; # server_name localhost; # ssl_certificate cert.pem; # ssl_certificate_key cert.key; # ssl_session_cache shared:SSL:1m; # ssl_session_timeout 5m; # ssl_ciphers HIGH:!aNULL:!MD5; # ssl_prefer_server_ciphers on; # location / { # root html; # index index.html index.htm; # } #} } 使用root权限启动nginxsudo nginx此手机开启热点后,其他设备连接后访问https://dzsms.gwm.com.cn/ 能显示3.0.apk即为成功直接实战手机升级高德地图8.1长城三代哈弗H6哈弗大狗坦克300安波福华阳笔记本一键部署3.1DNS工程模式跑代码 https://www.bilibili.com/video/BV14vk2Y9EzA/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准2、原理解析https://www.bilibili.com/video/BV1eXCAYjEi5/ ADB在哪里在第三代哈弗H6车机中,ADB程序位于工程模式中,在2021、2022出厂的车固件中内置,2023年起移除;这个程序只有厂家有,我们可以从2023之前的系统中,用ADB工具将工程模式APP导出。完成第一项:获得ADB程序车机有没有对外请求数据由于没有了ADB程序,我们是无法安装工程模式到车机中的,这时候就需要利用哈弗车机的一个漏洞,即智能手册APP证书无验证漏洞。进入智能手册APP后,APP会向哈弗服务器一个URL发送请求,用来请求最新版本,让车机WIFI连接到我们的设备进行抓包,查看请求状态,智能手册APP会解析JSON格式的回复内容判断是否下载APK升级。完成第二项:获取一个系统漏洞怎么把ADB装进去我们参照官方服务器,自行搭建DNS和web服务器,让车机连到我们的DNS服务器上,进行请求的劫持,这样,我们自己的APP就会被以程序更新的方式发送到车机中进行安装。完成第三项:将ADB注入到车机中,重新取得ADB权限ADB安装软件开启无线ADB或使用有线ADB,都可以使用ADB工具进行软件安装,如安卓内置命令pm、电脑搞机工具箱、手机甲壳虫。3、高德地图车机版去签名验证、修改导航栏遮蔽去签名验证使用apktool M 删除签名校验使用MT管理器打开classes.dex,搜索apks将文件最后的0x0改为0x1删除包中的 lib\armeabi-v7a\libsgsecuritybody.so文件保存编译即可修改导航栏遮蔽方法一(不推荐)https://www.bilibili.com/video/BV1Y2ApeDExW/ 视频仅为操作指导,具有时效性,以网站最新文字教程为准用Android Killer修改地图文件配置文件位置res\layout\main_map_view.xmlbackground_dark 框架层ui_surface UI层map_surface 地图层android:layout_marginLeft="100.0dip" 左侧避让100dipandroid:layout_marginTop="64.0dip" 上侧避让100dip例如左侧地图层规避、上侧元素层规避 <com.autonavi.amapauto.view.MapSurfaceViewEx android:id="@id/map_surface" android:layout_width="fill_parent" android:layout_height="fill_parent" android:layout_marginLeft="100.0dip" /> <SurfaceView android:id="@id/ui_surface" android:layout_width="fill_parent" android:layout_height="fill_parent" android:layout_marginLeft="100.0dip" android:layout_marginTop="64.0dip" />4) 使用MT管理器 重新签名修改导航栏遮蔽方法二(推荐)使用MT管理器导出FuncConfig.dat位于高德apk/assets/res/HmiRes/使用FuncConfig.dat 在线加解密 https://fun.cccyn.cc/解密出txt后,修改DysmorphismInfo,四个数字是左上右下的边距,statusBarColor是华阳的状态栏透明华阳左侧上侧规避状态栏透明 "DysmorphismInfo": "60,50,0,0", "statusBarColor": "-1",安波福左侧上侧规避状态栏透明 "DysmorphismInfo": "60,50,0,0", "statusBarColor": "0", "IgnoreInvalidLaneExport": "0", "ImmersiveMode": "9472", 将FuncConfig.txt加密成dat文件,塞回去自动编译即可4、把无线ADB软件移动到系统目录,还原不丢失termux中执行连接IP,写无线ADB开关里提示的IPadb connect IP地址查看当前连接的设备是否连接成功,成功后进行后续操作adb devices{message type="info" content="此步骤无风险,但可能移除后无线ADB软件就找不到了,此步骤可以不执行"/}termux中执行adb root;adb wait-for-device;adb remount;adb root;adb wait-for-device;adb remount;adb shell mv /data/app/com.example.xadb* /system/app/;adb shell mv /data/app/com.tencent.sotainstaller* /system/app/;adb shell pm path com.tencent.sotainstaller;adb shell pm path com.example.xadb5、使用termux移除内置地图adb shell pm clear com.autonavi.amapauto;adb root;adb wait-for-device;adb remount;adb root;adb wait-for-device;adb remount;adb shell am force-stop com.autonavi.amapauto;adb shell am force-stop com.autonavi.amapauto;adb shell rm -rf /system/app/Navigation;adb shell rm -rf /system/app/Navigation;adb shell rm -rf /system/app/AutoMap;adb shell rm -rf /system/app/AutoMap;adb reboot{lamp/}四、小结哈哈哈哈哈哈哈 -
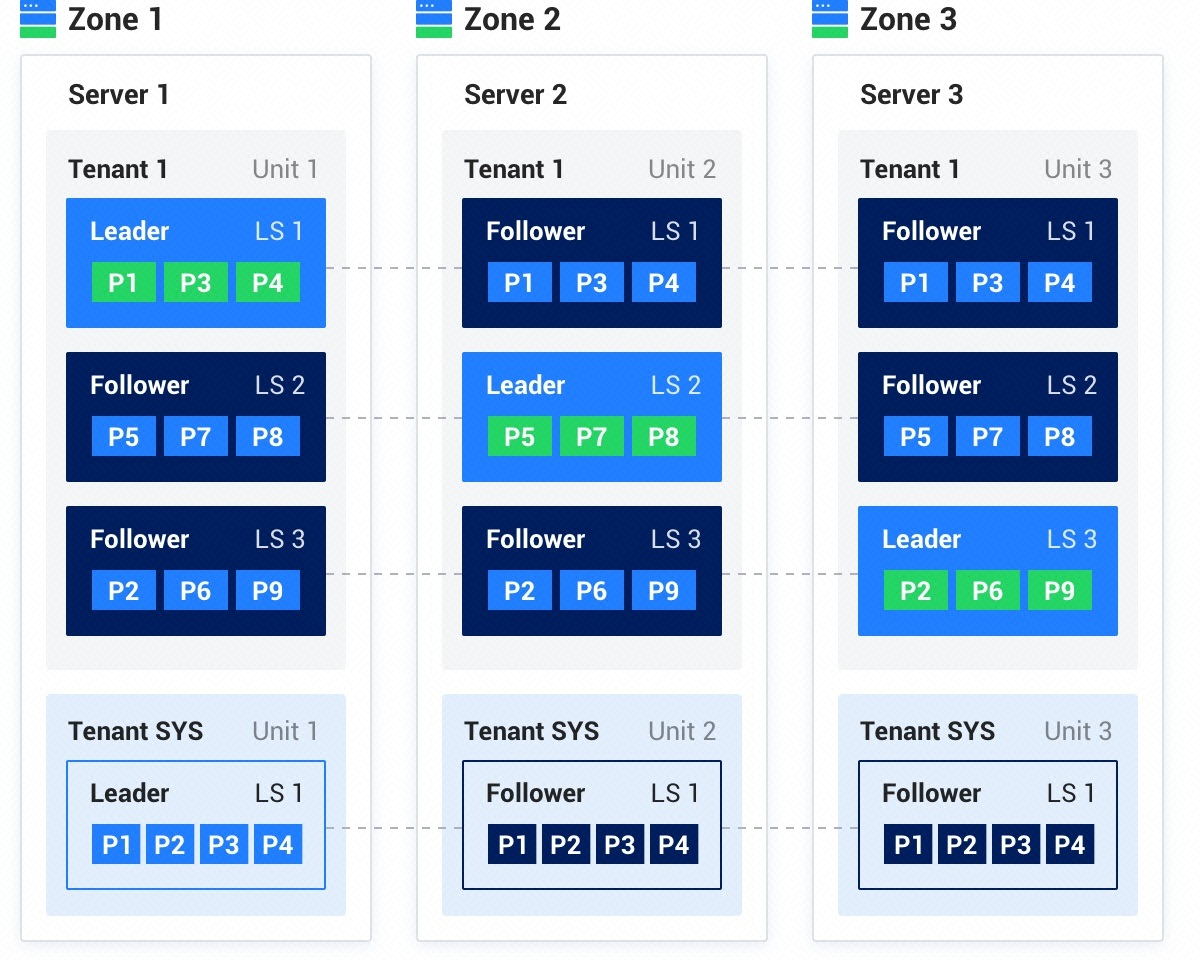
 OceanBase OB原生分布式数据库V4社区版高可用部署、OCP云平台、OMS迁移服务部署zabbix6数据迁移、1Panel面板adminer web数据库管理工具、minio S3备份还原计划、集群扩容缩容、租户扩容缩容、ODC开发者中心、OBProxy集群keepalived高可用主备VIP部署、故障处理、不停机滚动升级 {alert type="info"}本文使用vSAN集群进行真实安装,密码均为随机生成,试验结束后销毁网段和集群;虽为模拟实验,但完全适用于真实生产环境;因为使用的虚拟机,所以硬盘分区无意义,仅一个根分区500G。{/alert}本文已加入 《OceanBase 4.x DBA 进阶教程》用户共建计划https://ask.oceanbase.com/t/topic/35617370/所有参与共建的用户,都会出现在 OceanBase 进阶教程电子书的致谢名单中,欢迎大家加入~一、OceanBase 社区版为现代数据架构打造的开源分布式数据库。兼容 MySQL 的单机分布式一体化国产开源数据库,具有原生分布式架构,支持金融级高可用、透明水平扩展、分布式事务、多租户和语法兼容等企业级特性。OceanBase 内核通过大规模商用场景的考验,已服务众多行业客户;面向未来携手生态伙伴,共建开源开放的数据库内核和生态。文档:https://www.oceanbase.com/docs{lamp/}二、OCP云平台部署OceanBase 云平台(OceanBase Cloud Platform,OCP)是一款为 OceanBase 集群量身打造的企业级管理平台,兼容 OceanBase 所有主流版本。OCP 提供对 OceanBase 图形化管理能力,包括数据库及相关资源的全生命周期管理、监控告警、性能诊断、故障恢复、备份恢复等,旨在协助客户更加高效地管理 OceanBase 数据库,降低企业的IT运维成本和用户的学习成本。https://www.oceanbase.com/docs/ocp1、主机规划本教程部署简化版集群 1ocp 1oms 2proxy 3zone6server 共10台主机,另外独立安装zabbix6和minioocp配置 16C 64G 500G其他主机配置 8C 32G 500G操作系统为anolis8,全部关闭防火墙tntocp 192.168.4.100 tntoms 192.168.4.101 tntproxy1 192.168.4.102 tntproxy2 192.168.4.103 tntob1-1 192.168.4.104 tntob1-2 192.168.4.105 tntob2-1 192.168.4.106 tntob2-2 192.168.4.107 tntob3-1 192.168.4.108 tntob3-2 192.168.4.109 tntzabbix6 192.168.4.110 tntminio 192.168.4.111 tntproxy 192.168.4.99 keepalived虚拟IP2、安装准备下载OceanBase社区版一键安装包 (OceanBase All in One)OceanBase 数据库一键离线安装包,包括 OceanBase 数据库和 OCP(自 V4.3.3 起包含)、obd、OBProxy、OBClient、OCP Express、Prometheus、Grafana,以及诊断和测试工具。https://www.oceanbase.com/softwarecenterOCP依赖仅支持 JDK1.8 版本,下载并安装 jre-8u441-linux-x64.rpmhttps://www.java.com/en/download/manual.jsp3、图形化部署OCP所有主机关闭防火墙systemctl stop firewalld && systemctl disable firewalld上传一键安装包至OCP主机、解压安装解压 tar zxf oceanbase-all-in-one-4.3.5_bp1_20250320.el8.x86_64.tar.gz启动obdcd oceanbase-all-in-one/bin source ~/.oceanbase-all-in-one/bin/env.sh obd web install生成网页安装URL进入 OCP 部署向导页面部署OCP云平台并创建全新数据库设置集群名称创建metaDB,我这里使用ocp主机单机部署metaDB,即OCP、数据库节点、OBProxy都是一台服务器OCP 资源规划为20台主机预检查无异常部署中,等待部署完成,记好账号密码{lamp/}三、OCP云平台使用1、登录OCP云平台http://192.168.4.100:8080看到OCP平台初始化失败查看异常为netstat: 未找到命令{message type="info" content="注意,所有OB主机都需要netstat,通过yum安装"/}yum install net-tools -y所有OB主机都需要netstat!全部安装一遍点击重启,执行成功OCP部署成功2、OCP操作流程添加主机-新建集群-创建租户-创建用户-创建OBProxy集群3、添加作为OBProxy集群和OBserver的主机192.168.4.102-109主机标准化分为OBProxy和OceanBase,等待标准化完成OBProxy标准化无异常但也需要修复一下,OceanBase标准化有8个异常,都需要修复修复检查透明大页 echo never > /sys/kernel/mm/transparent_hugepage/enabled 生效 chmod +x /etc/rc.d/rc.local 添加到开机启动 vi /etc/rc.d/rc.local echo never > /sys/kernel/mm/transparent_hugepage/enabled 安装python2.7 yum install python2 -y 禁用swap分区 swapoff -a 删除swap分区 /etc/fstab 安装软件 yum -y install net-tools mtr tar binutils bind-utils curl nc iproute 添加admin用户 groupadd -g 500 admin useradd -m -u 500 -g 500 -s /bin/bash admin id admin 关闭selinux 检查ulimit信息 /etc/security/limits.d/99-oceanbase_limits.conf root soft nofile 655350 root hard nofile 655350 admin soft nofile 655350 admin hard nofile 655350 admin soft stack 10240 admin hard stack 10240 admin soft nproc 655360 admin hard nproc 655360 admin soft core unlimited admin hard core unlimited 检查 clocksource 信息 echo tsc > /sys/devices/system/clocksource/clocksource0/current_clocksource 时间同步 调整端口范围,保留端口 sudo sysctl net.ipv4.ip_local_port_range vi /etc/sysctl.conf net.ipv4.ip_local_port_range = 3500 65535 net.ipv4.ip_local_reserved_ports = 62881-63881 生效 sudo sysctl -p python2软连接到python sudo ln -sf /usr/bin/python2 /usr/bin/python 创建软件目录 mkdir /data/log1 -p mkdir /data/1 -p 重新检查,修复完成4、新建集群新建tntob集群,3zone,每zone 2台主机,由于是实验集群,我没有开启cgroup创建中安装完成5、创建租户创建zabbix6租户Unit规格选择S1并允许所有IP访问创建完成6、创建用户在zabbix6租户中创建用户zabbixdb,先不用创建数据库,一会直接导入一个数据库7、创建OBProxy集群创建tntproxy集群,加入102、103两台主机{message type="info" content="注意:102、103都可以访问集群,而访问地址,一般指的是负载均衡设备的VIP地址,暂不讨论,这里访问地址先填写102"/}创建完成连接到tntob集群8、连接测试使用adminer登陆测试一下连接参数 mysql -h192.168.4.102 -P2883 -uroot@zabbix6#tntob -p登录成功OceanBase分布式数据库集群部署完毕{lamp/}四、OMS迁移服务部署zabbix6数据迁移OMS文档https://www.oceanbase.com/docs/oms-cn1、创建oms租户创建oms租户作为OMS迁移服务的元数据库,需要使用租户的root用户2、安装OMS迁移服务下载软件包 oms_4.2.8-ce.tar.gz 上传到tntoms主机https://www.oceanbase.com/softwarecenter安装dockeryum install -y yum-utils #阿里云加速源 yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo yum install docker-ce docker-ce-cli containerd.io启动dockersystemctl enable --now docker导入镜像docker load -i oms_4.2.8-ce.tar.gz查看镜像名docker images REPOSITORY TAG IMAGE ID CREATED SIZE reg.docker.alibaba-inc.com/oceanbase/oms feature_4.2.8_ce d56598287295 7 weeks ago 10.9GB 获取部署脚本sudo docker run -d --net host --name oms-config-tool reg.docker.alibaba-inc.com/oceanbase/oms:feature_4.2.8_ce bash && sudo docker cp oms-config-tool:/root/docker_remote_deploy.sh . && sudo docker rm -f oms-config-tool 启动部署mkdir /oms bash docker_remote_deploy.sh -o /oms -i 192.168.4.101 -d reg.docker.alibaba-inc.com/oceanbase/oms:feature_4.2.8_ce 安装中 ****CPU**** CPU_Name(System_Name): Intel(R) Xeon(R) Silver 4309Y CPU @ 2.80GHz Total_physical_CPU: 8 Total_core_num: 8 *****Memory****** Total_Mem: 32915048 KB Total_Mem: 31 G *****Disk****** Total_disk_avail: 954 G 提示:输入 <Control-C> 可退出部署 请选择部署模式: ●单地域单节点 单地域多节点 多地域 您选择的部署模式是:单地域单节点部署模式 请选择您所需要进行的任务: ●无配置文件,全新部署 OMS,从生成配置文件开始 已通过脚本[-c]选项传入参考配置文件,基于参考配置文件开始配置 开始配置元信息库,可以是 MySQL 或 OceanBase 数据库 MySQL 租户 (元信息库用于存储 OMS 运行时元数据信息) 请输入元信息数据库 IP:192.168.4.102 请输入元信息数据库端口:2883 请输入元信息数据库用户名:root@oms#tntob 请输入元信息数据库密码:*********************** 请为 OMS 元数据库设置前缀 (示例:当前缀设置为 oms 时,最终库名分别为 oms_rm/oms_cm/oms_cm_hb): 您的元信息库配置如下: { "drc_cm_db": "_cm", "drc_cm_heartbeat_db": "_cm_hb", "drc_rm_db": "_rm", "init_db": "true", "oms_meta_host": "192.168.4.102", "oms_meta_password": "9cb;CcrN1C3f,Xlub)rx{(#", "oms_meta_port": "2883", "oms_meta_user": "root@oms#tntob" } [y/n] 请确认配置信息[y]y 您选择的部署模式为单地域单节点部署模式 [y/n] 是否自定义组件端口号,并配置相关参数?[n]n [y/n] 获取到您的默认 IP 地址:192.168.4.101,请确认是否需要更改?[n]n 您的 OMS 集群配置如下: { "cm_is_default": true, "cm_location": 0, "cm_nodes": [ "192.168.4.101" ], "cm_region": "default", "cm_region_cn": "默认地域", "cm_server_port": "8088", "cm_url": "http://192.168.4.101:8088", "ghana_server_port": "8090", "nginx_server_port": "8089", "sshd_server_port": "2023", "supervisor_server_port": "9000" } [y/n] 请确认配置信息[y]y [y/n] 您是否需要对 OMS 历史数据进行监控?[n]n [y/n] 是否需要开启 OMS 审计日志功能,并将审计日志写入 SLS 服务?[n]n 已加载您的所有配置项,并校验通过。 您的配置如下: { "apsara_audit_enable": "false", "apsara_audit_sls_access_key": "", "apsara_audit_sls_access_secret": "", "apsara_audit_sls_endpoint": "", "apsara_audit_sls_ops_site_topic": "", "apsara_audit_sls_user_site_topic": "", "cm_is_default": true, "cm_location": "0", "cm_nodes": [ "192.168.4.101" ], "cm_region": "default", "cm_region_cn": "默认地域", "cm_server_port": "8088", "cm_url": "http://192.168.4.101:8088", "drc_cm_db": "_cm", "drc_cm_heartbeat_db": "_cm_hb", "drc_rm_db": "_rm", "ghana_server_port": "8090", "init_db": "true", "nginx_server_port": "8089", "oms_meta_host": "192.168.4.102", "oms_meta_password": "9cb;CcrN1C3f,Xlub)rx{(#", "oms_meta_port": "2883", "oms_meta_user": "root@oms#tntob", "sshd_server_port": "2023", "supervisor_server_port": "9000", "tsdb_enabled": "false", "tsdb_password": "", "tsdb_service": "", "tsdb_url": "", "tsdb_username": "" } [y/n] 您是否需要重新配置?[n]n 您是需要在当前执行的机器上 接下来 OMS 需要在节点 ['192.168.4.101'] 上依次执行部署脚本。 请输入节点 192.168.4.101 上预备部署 OMS 的挂载目录:[/oms/]/oms/ 请您确认以下内容: [y/n] 部署 OMS 的 [镜像名/IMAGE-ID] 是:reg.docker.alibaba-inc.com/oceanbase/oms:feature_4.2.8_ce ,请确认是否正确。[y]y [y/n] 是否需要在 OMS 容器中挂载 HTTPS 证书?[n]n [y/n] 192.168.4.101 节点下的配置文件 config.yaml 将写在这个路径:/oms/ 下可以吗?[y]y ....... -------------------------------------------------------------------------------- # 【结束】全部初始化步骤执行成功 -------------------------------------------------------------------------------- 登录控制台,首次登陆设置密码http://192.168.4.101:8089/3、zabbix6安装查看王工zabbix6文章快速部署,部署完成后迁移到OceanBase集群https://90apt.com/2982安装完成4、导出zabbix6数据库结构使用adminer导出数据库结构,不包括数据adminer安装见后面1Panel部分使用adminer导入到zabbix租户中5、OMS全量迁移在OCP中给zabbixuser用户赋予zabbix数据库全部权限添加双方数据源配置迁移任务启动任务迁移完成,进行切换6、zabbix6切换数据库,重启服务、查看日志配置文件修改/etc/zabbix/web/zabbix.conf.php<?php // Zabbix GUI configuration file. $DB['TYPE'] = 'MYSQL'; $DB['SERVER'] = '192.168.4.102'; $DB['PORT'] = '2883'; $DB['DATABASE'] = 'zabbix'; $DB['USER'] = 'zabbixuser@zabbix6#tntob'; $DB['PASSWORD'] = 'r*h(c^rLst8F'; /etc/zabbix/zabbix_server.confDBHost=192.168.4.102 DBName=zabbix DBUser=zabbixuser@zabbix6#tntob DBPassword=r*h(c^rLst8F DBPort=2883重启zabbix服务 systemctl restart zabbix-server查看日志是否有异常/var/log/zabbix/zabbix_server.logUnable to start Zabbix server due to unsupported MySQL database version (5.06.25).修改OBPorxy数据版本,修改为8.0.0再次重启zabbix服务查看日志,无异常zabbix功能正常,采集正常{lamp/}五、1Panel面板minio S3备份还原计划1、安装docker安装dockeryum install -y yum-utils #阿里云加速源 yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo yum install docker-ce docker-ce-cli containerd.io启动dockersystemctl enable --now docker2、安装1Panel面板curl -sSL https://resource.fit2cloud.com/1panel/package/quick_start.sh -o quick_start.sh && sh quick_start.sh安装adminer web数据库管理工具支持MySQL、MariaDB、 SQLite、PostgreSQL、Oracle (beta)、MS SQL3、安装minio,配置S3存储登录1Panel面板安装minio登录minio创建Bucket创建Access Keys4、配置备份计划创建zabbix6租户备份策略存储目录为Bucket名称访问域名为API的URL http://192.168.4.111:9000在填入AK、SK,点击测试即可立即备份备份完成5、进行还原测试误删数据库由于王工上年纪老眼昏花,不小心删除了zabbix数据库,不稳啦!zabbix崩溃进行租户恢复恢复完成创建了新的租户,将原租户改名,新租户改为原来的名,这样业务就不用动了业务恢复了,王工又稳啦!{lamp/}六、集群、租户扩缩容1、集群扩容添加主机-集群管理-添加OBServer、新增Zone添加主机OCP云平台-主机-添加主机主机还是要按之前标准化进行环境修复,修复好再添加再次进行标准化OCP云平台-集群-概览-添加OBServer一段时间后部署模式变为集群 (3-3-3)新增Zone与之相同2、集群缩容https://www.oceanbase.com/docs/common-oceanbase-database-cn-1000000002013120删除OBServer时自动进行Unit迁出完成缩容我这边删除114 115 116三台主机批量删除删除中缩容完成3、租户扩容进入租户修改UnitOCP云平台-租户-概览-修改Unit如,将配置修改为S2,Unit修改为2扩容成功4、租户缩容如,将配置修改为S1,Unit修改为1缩容完成{lamp/}七、ODC开发者中心OceanBase 开发者中心(OceanBase Developer Center,ODC)是开源的企业级数据库协同开发工具,有桌面版、Web 版两种产品形态。 ODC Web 版提供了个人空间和团队空间两种工作模式。个人空间适合个人开发者使用,为您在浏览器端提供桌面版的体验;团队空间适合开发者和 DBA 协同使用,既是开发工具也是管控协同平台。 ODC 的代码维护在 Github,单击查看详情,加入 ODC 开源社区,一起创造 开发者和 DBA 喜爱的数据库协同开发工具。https://www.oceanbase.com/docs/odc{message type="info" content="注意:按官方教程你很可能装不上,还是看我的吧"/}1、下载OceanBase 开发者中心web镜像上传到OMS主机,我将ODC安装在OMS主机,ODC为docker镜像https://www.oceanbase.com/softwarecenter2、为ODC创建一个mysql租户并创建一个数据库创建tntodc租户 tntodc数据库 root用户{message type="info" content="注意:数据库用户我测试用普通用户无法部署ODC,需要root用户"/}3、加载镜像gunzip -c obodc4.3.3-bp2.tar.gz | docker load查看镜像docker images REPOSITORY TAG IMAGE ID CREATED SIZE reg.docker.alibaba-inc.com/oceanbase/oms feature_4.2.8_ce d56598287295 7 weeks ago 10.9GB oceanbase/odc 4.3.3_bp2 98a74ab3fbe1 7 weeks ago 1.75GB 4、创建安装脚本odcinstall.sh#!/usr/bin/env bash mkdir -p /tntodc/log/odc mkdir -p /tntodc/data/odc docker run -v /tntodc/log/odc:/opt/odc/log -v /tntodc/data/odc:/opt/odc/data \ -d -i -p 8989:8989 --cpu-period 100000 --cpu-quota 400000 --memory 8G --name "obodc" \ -e "DATABASE_HOST=192.168.4.102" \ -e "DATABASE_PORT=2883" \ -e "DATABASE_USERNAME=root@tntodc#tntob" \ -e "DATABASE_PASSWORD=78ABcd##123" \ -e "DATABASE_NAME=tntodc" \ -e "ODC_ADMIN_INITIAL_PASSWORD=78ABcd##123" \ oceanbase/odc:4.3.3_bp2 注意Shell 环境下,字符串中包含 !、$ 等特殊字符时,变量值需要使用单引号。例如:DATABASE_PASSWORD='11111!'。参数 ODC_ADMIN_INITIAL_PASSWORD 用于指定 ODC 管理员账号的初始密码。设置的初始密码需要须满足以下条件:至少 2 个数字。至少 2 个大写字母。至少 2 个小写字母。至少 2 个特殊字符,特殊字符的范围为 ._+@#$%。不包含空格和其他特殊字符,长度为 8-32。{lamp/}5、安装bash odcinstall.sh6、登录成功八、OBProxy集群keepalived高可用主备VIP部署keepalived介绍请看王工其他文章1、安装keepalived两台OBProxy主机分别安装keepalivedyum install -y keepalived2、配置keepalived两台OBProxy主机分别创建Proxy存活检测脚本vi /etc/keepalived/check_obproxy.sh#!/bin/bash # 检查2883端口是否有监听 if ss -tuln | grep -q ':2883\b'; then exit 0 # 检测成功,返回0 else exit 1 # 检测失败,返回1 fitntproxy1配置执行权限chmod +x /etc/keepalived/check_obproxy.sh配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_script check_obproxy { script "/etc/keepalived/check_obproxy.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } unicast_src_ip 192.168.4.102 #本机ip unicast_peer { 192.168.4.103 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.99/24 #VIP(自己网段的) } track_script { check_obproxy } }tntproxy2配置执行权限chmod +x /etc/keepalived/check_obproxy.sh配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_script check_obproxy { script "/etc/keepalived/check_obproxy.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } unicast_src_ip 192.168.4.103 #本机ip unicast_peer { 192.168.4.102 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.99/24 #抢占的VIP也一样 } track_script { check_obproxy } }3、启动服务systemctl enable --now keepalived4、高可用测试将zabbix数据库指向VIP,连续ping 192.168.4.99,并查看zabbix服务状态obproxy1关机,查看ping和zabbix状态正常,业务几乎无感来自 192.168.4.99 的回复: 字节=32 时间=15ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=21ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=28ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=2ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=49ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=1ms TTL=63obproxy2获得VIPinet 192.168.4.103/24 brd 192.168.4.255 scope global noprefixroute ens192 valid_lft forever preferred_lft forever inet 192.168.4.99/24 scope global secondary ens192 valid_lft forever preferred_lft forever obproxy1开机,obproxy服务启动成功后,自动抢回VIP inet 192.168.4.102/24 brd 192.168.4.255 scope global noprefixroute ens192 valid_lft forever preferred_lft forever inet 192.168.4.99/24 scope global secondary ens192 valid_lft forever preferred_lft forever 5、测试结论高可用正常,VIP正常九、故障处理1、任意一台OBServer主机故障关机1台OBServer主机,集群无影响,一段时间后Zone内另一台主机接管此OBServer功能开机此OBServer,一段时间后集群自动修复此主机并上线2、{lamp/}十、不停机滚动升级V4.3.5_CE_BP1_HF1版本信息发布时间:2025 年 04 月 30 日下载数据库rpm安装包oceanbase-ce-4.3.5.1-101010042025042417.el8.x86_64.rpmhttps://www.oceanbase.com/softwarecenter登录OCP平台,进入集群,升级版本上传安装包升级路经确认提示 集群升级缺少社区版依赖包:[oceanbase-ce-utils-4.3.5.1-101010042025042417.x86_64, oceanbase-ce-libs-4.3.5.1-101010042025042417.x86_64]下载并上传oceanbase-ce-libs-4.3.5.1-101010042025042417.el8.x86_64.rpmoceanbase-ce-utils-4.3.5.1-101010042025042417.el8.x86_64.rpm升级中升级前版本升级中如果出现任务失败,根据情况可点击重试,我点了四五次就完成了升级后版本,升级完成,升级过程中业务无感知{lamp/}十一、总结太强了
OceanBase OB原生分布式数据库V4社区版高可用部署、OCP云平台、OMS迁移服务部署zabbix6数据迁移、1Panel面板adminer web数据库管理工具、minio S3备份还原计划、集群扩容缩容、租户扩容缩容、ODC开发者中心、OBProxy集群keepalived高可用主备VIP部署、故障处理、不停机滚动升级 {alert type="info"}本文使用vSAN集群进行真实安装,密码均为随机生成,试验结束后销毁网段和集群;虽为模拟实验,但完全适用于真实生产环境;因为使用的虚拟机,所以硬盘分区无意义,仅一个根分区500G。{/alert}本文已加入 《OceanBase 4.x DBA 进阶教程》用户共建计划https://ask.oceanbase.com/t/topic/35617370/所有参与共建的用户,都会出现在 OceanBase 进阶教程电子书的致谢名单中,欢迎大家加入~一、OceanBase 社区版为现代数据架构打造的开源分布式数据库。兼容 MySQL 的单机分布式一体化国产开源数据库,具有原生分布式架构,支持金融级高可用、透明水平扩展、分布式事务、多租户和语法兼容等企业级特性。OceanBase 内核通过大规模商用场景的考验,已服务众多行业客户;面向未来携手生态伙伴,共建开源开放的数据库内核和生态。文档:https://www.oceanbase.com/docs{lamp/}二、OCP云平台部署OceanBase 云平台(OceanBase Cloud Platform,OCP)是一款为 OceanBase 集群量身打造的企业级管理平台,兼容 OceanBase 所有主流版本。OCP 提供对 OceanBase 图形化管理能力,包括数据库及相关资源的全生命周期管理、监控告警、性能诊断、故障恢复、备份恢复等,旨在协助客户更加高效地管理 OceanBase 数据库,降低企业的IT运维成本和用户的学习成本。https://www.oceanbase.com/docs/ocp1、主机规划本教程部署简化版集群 1ocp 1oms 2proxy 3zone6server 共10台主机,另外独立安装zabbix6和minioocp配置 16C 64G 500G其他主机配置 8C 32G 500G操作系统为anolis8,全部关闭防火墙tntocp 192.168.4.100 tntoms 192.168.4.101 tntproxy1 192.168.4.102 tntproxy2 192.168.4.103 tntob1-1 192.168.4.104 tntob1-2 192.168.4.105 tntob2-1 192.168.4.106 tntob2-2 192.168.4.107 tntob3-1 192.168.4.108 tntob3-2 192.168.4.109 tntzabbix6 192.168.4.110 tntminio 192.168.4.111 tntproxy 192.168.4.99 keepalived虚拟IP2、安装准备下载OceanBase社区版一键安装包 (OceanBase All in One)OceanBase 数据库一键离线安装包,包括 OceanBase 数据库和 OCP(自 V4.3.3 起包含)、obd、OBProxy、OBClient、OCP Express、Prometheus、Grafana,以及诊断和测试工具。https://www.oceanbase.com/softwarecenterOCP依赖仅支持 JDK1.8 版本,下载并安装 jre-8u441-linux-x64.rpmhttps://www.java.com/en/download/manual.jsp3、图形化部署OCP所有主机关闭防火墙systemctl stop firewalld && systemctl disable firewalld上传一键安装包至OCP主机、解压安装解压 tar zxf oceanbase-all-in-one-4.3.5_bp1_20250320.el8.x86_64.tar.gz启动obdcd oceanbase-all-in-one/bin source ~/.oceanbase-all-in-one/bin/env.sh obd web install生成网页安装URL进入 OCP 部署向导页面部署OCP云平台并创建全新数据库设置集群名称创建metaDB,我这里使用ocp主机单机部署metaDB,即OCP、数据库节点、OBProxy都是一台服务器OCP 资源规划为20台主机预检查无异常部署中,等待部署完成,记好账号密码{lamp/}三、OCP云平台使用1、登录OCP云平台http://192.168.4.100:8080看到OCP平台初始化失败查看异常为netstat: 未找到命令{message type="info" content="注意,所有OB主机都需要netstat,通过yum安装"/}yum install net-tools -y所有OB主机都需要netstat!全部安装一遍点击重启,执行成功OCP部署成功2、OCP操作流程添加主机-新建集群-创建租户-创建用户-创建OBProxy集群3、添加作为OBProxy集群和OBserver的主机192.168.4.102-109主机标准化分为OBProxy和OceanBase,等待标准化完成OBProxy标准化无异常但也需要修复一下,OceanBase标准化有8个异常,都需要修复修复检查透明大页 echo never > /sys/kernel/mm/transparent_hugepage/enabled 生效 chmod +x /etc/rc.d/rc.local 添加到开机启动 vi /etc/rc.d/rc.local echo never > /sys/kernel/mm/transparent_hugepage/enabled 安装python2.7 yum install python2 -y 禁用swap分区 swapoff -a 删除swap分区 /etc/fstab 安装软件 yum -y install net-tools mtr tar binutils bind-utils curl nc iproute 添加admin用户 groupadd -g 500 admin useradd -m -u 500 -g 500 -s /bin/bash admin id admin 关闭selinux 检查ulimit信息 /etc/security/limits.d/99-oceanbase_limits.conf root soft nofile 655350 root hard nofile 655350 admin soft nofile 655350 admin hard nofile 655350 admin soft stack 10240 admin hard stack 10240 admin soft nproc 655360 admin hard nproc 655360 admin soft core unlimited admin hard core unlimited 检查 clocksource 信息 echo tsc > /sys/devices/system/clocksource/clocksource0/current_clocksource 时间同步 调整端口范围,保留端口 sudo sysctl net.ipv4.ip_local_port_range vi /etc/sysctl.conf net.ipv4.ip_local_port_range = 3500 65535 net.ipv4.ip_local_reserved_ports = 62881-63881 生效 sudo sysctl -p python2软连接到python sudo ln -sf /usr/bin/python2 /usr/bin/python 创建软件目录 mkdir /data/log1 -p mkdir /data/1 -p 重新检查,修复完成4、新建集群新建tntob集群,3zone,每zone 2台主机,由于是实验集群,我没有开启cgroup创建中安装完成5、创建租户创建zabbix6租户Unit规格选择S1并允许所有IP访问创建完成6、创建用户在zabbix6租户中创建用户zabbixdb,先不用创建数据库,一会直接导入一个数据库7、创建OBProxy集群创建tntproxy集群,加入102、103两台主机{message type="info" content="注意:102、103都可以访问集群,而访问地址,一般指的是负载均衡设备的VIP地址,暂不讨论,这里访问地址先填写102"/}创建完成连接到tntob集群8、连接测试使用adminer登陆测试一下连接参数 mysql -h192.168.4.102 -P2883 -uroot@zabbix6#tntob -p登录成功OceanBase分布式数据库集群部署完毕{lamp/}四、OMS迁移服务部署zabbix6数据迁移OMS文档https://www.oceanbase.com/docs/oms-cn1、创建oms租户创建oms租户作为OMS迁移服务的元数据库,需要使用租户的root用户2、安装OMS迁移服务下载软件包 oms_4.2.8-ce.tar.gz 上传到tntoms主机https://www.oceanbase.com/softwarecenter安装dockeryum install -y yum-utils #阿里云加速源 yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo yum install docker-ce docker-ce-cli containerd.io启动dockersystemctl enable --now docker导入镜像docker load -i oms_4.2.8-ce.tar.gz查看镜像名docker images REPOSITORY TAG IMAGE ID CREATED SIZE reg.docker.alibaba-inc.com/oceanbase/oms feature_4.2.8_ce d56598287295 7 weeks ago 10.9GB 获取部署脚本sudo docker run -d --net host --name oms-config-tool reg.docker.alibaba-inc.com/oceanbase/oms:feature_4.2.8_ce bash && sudo docker cp oms-config-tool:/root/docker_remote_deploy.sh . && sudo docker rm -f oms-config-tool 启动部署mkdir /oms bash docker_remote_deploy.sh -o /oms -i 192.168.4.101 -d reg.docker.alibaba-inc.com/oceanbase/oms:feature_4.2.8_ce 安装中 ****CPU**** CPU_Name(System_Name): Intel(R) Xeon(R) Silver 4309Y CPU @ 2.80GHz Total_physical_CPU: 8 Total_core_num: 8 *****Memory****** Total_Mem: 32915048 KB Total_Mem: 31 G *****Disk****** Total_disk_avail: 954 G 提示:输入 <Control-C> 可退出部署 请选择部署模式: ●单地域单节点 单地域多节点 多地域 您选择的部署模式是:单地域单节点部署模式 请选择您所需要进行的任务: ●无配置文件,全新部署 OMS,从生成配置文件开始 已通过脚本[-c]选项传入参考配置文件,基于参考配置文件开始配置 开始配置元信息库,可以是 MySQL 或 OceanBase 数据库 MySQL 租户 (元信息库用于存储 OMS 运行时元数据信息) 请输入元信息数据库 IP:192.168.4.102 请输入元信息数据库端口:2883 请输入元信息数据库用户名:root@oms#tntob 请输入元信息数据库密码:*********************** 请为 OMS 元数据库设置前缀 (示例:当前缀设置为 oms 时,最终库名分别为 oms_rm/oms_cm/oms_cm_hb): 您的元信息库配置如下: { "drc_cm_db": "_cm", "drc_cm_heartbeat_db": "_cm_hb", "drc_rm_db": "_rm", "init_db": "true", "oms_meta_host": "192.168.4.102", "oms_meta_password": "9cb;CcrN1C3f,Xlub)rx{(#", "oms_meta_port": "2883", "oms_meta_user": "root@oms#tntob" } [y/n] 请确认配置信息[y]y 您选择的部署模式为单地域单节点部署模式 [y/n] 是否自定义组件端口号,并配置相关参数?[n]n [y/n] 获取到您的默认 IP 地址:192.168.4.101,请确认是否需要更改?[n]n 您的 OMS 集群配置如下: { "cm_is_default": true, "cm_location": 0, "cm_nodes": [ "192.168.4.101" ], "cm_region": "default", "cm_region_cn": "默认地域", "cm_server_port": "8088", "cm_url": "http://192.168.4.101:8088", "ghana_server_port": "8090", "nginx_server_port": "8089", "sshd_server_port": "2023", "supervisor_server_port": "9000" } [y/n] 请确认配置信息[y]y [y/n] 您是否需要对 OMS 历史数据进行监控?[n]n [y/n] 是否需要开启 OMS 审计日志功能,并将审计日志写入 SLS 服务?[n]n 已加载您的所有配置项,并校验通过。 您的配置如下: { "apsara_audit_enable": "false", "apsara_audit_sls_access_key": "", "apsara_audit_sls_access_secret": "", "apsara_audit_sls_endpoint": "", "apsara_audit_sls_ops_site_topic": "", "apsara_audit_sls_user_site_topic": "", "cm_is_default": true, "cm_location": "0", "cm_nodes": [ "192.168.4.101" ], "cm_region": "default", "cm_region_cn": "默认地域", "cm_server_port": "8088", "cm_url": "http://192.168.4.101:8088", "drc_cm_db": "_cm", "drc_cm_heartbeat_db": "_cm_hb", "drc_rm_db": "_rm", "ghana_server_port": "8090", "init_db": "true", "nginx_server_port": "8089", "oms_meta_host": "192.168.4.102", "oms_meta_password": "9cb;CcrN1C3f,Xlub)rx{(#", "oms_meta_port": "2883", "oms_meta_user": "root@oms#tntob", "sshd_server_port": "2023", "supervisor_server_port": "9000", "tsdb_enabled": "false", "tsdb_password": "", "tsdb_service": "", "tsdb_url": "", "tsdb_username": "" } [y/n] 您是否需要重新配置?[n]n 您是需要在当前执行的机器上 接下来 OMS 需要在节点 ['192.168.4.101'] 上依次执行部署脚本。 请输入节点 192.168.4.101 上预备部署 OMS 的挂载目录:[/oms/]/oms/ 请您确认以下内容: [y/n] 部署 OMS 的 [镜像名/IMAGE-ID] 是:reg.docker.alibaba-inc.com/oceanbase/oms:feature_4.2.8_ce ,请确认是否正确。[y]y [y/n] 是否需要在 OMS 容器中挂载 HTTPS 证书?[n]n [y/n] 192.168.4.101 节点下的配置文件 config.yaml 将写在这个路径:/oms/ 下可以吗?[y]y ....... -------------------------------------------------------------------------------- # 【结束】全部初始化步骤执行成功 -------------------------------------------------------------------------------- 登录控制台,首次登陆设置密码http://192.168.4.101:8089/3、zabbix6安装查看王工zabbix6文章快速部署,部署完成后迁移到OceanBase集群https://90apt.com/2982安装完成4、导出zabbix6数据库结构使用adminer导出数据库结构,不包括数据adminer安装见后面1Panel部分使用adminer导入到zabbix租户中5、OMS全量迁移在OCP中给zabbixuser用户赋予zabbix数据库全部权限添加双方数据源配置迁移任务启动任务迁移完成,进行切换6、zabbix6切换数据库,重启服务、查看日志配置文件修改/etc/zabbix/web/zabbix.conf.php<?php // Zabbix GUI configuration file. $DB['TYPE'] = 'MYSQL'; $DB['SERVER'] = '192.168.4.102'; $DB['PORT'] = '2883'; $DB['DATABASE'] = 'zabbix'; $DB['USER'] = 'zabbixuser@zabbix6#tntob'; $DB['PASSWORD'] = 'r*h(c^rLst8F'; /etc/zabbix/zabbix_server.confDBHost=192.168.4.102 DBName=zabbix DBUser=zabbixuser@zabbix6#tntob DBPassword=r*h(c^rLst8F DBPort=2883重启zabbix服务 systemctl restart zabbix-server查看日志是否有异常/var/log/zabbix/zabbix_server.logUnable to start Zabbix server due to unsupported MySQL database version (5.06.25).修改OBPorxy数据版本,修改为8.0.0再次重启zabbix服务查看日志,无异常zabbix功能正常,采集正常{lamp/}五、1Panel面板minio S3备份还原计划1、安装docker安装dockeryum install -y yum-utils #阿里云加速源 yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo yum install docker-ce docker-ce-cli containerd.io启动dockersystemctl enable --now docker2、安装1Panel面板curl -sSL https://resource.fit2cloud.com/1panel/package/quick_start.sh -o quick_start.sh && sh quick_start.sh安装adminer web数据库管理工具支持MySQL、MariaDB、 SQLite、PostgreSQL、Oracle (beta)、MS SQL3、安装minio,配置S3存储登录1Panel面板安装minio登录minio创建Bucket创建Access Keys4、配置备份计划创建zabbix6租户备份策略存储目录为Bucket名称访问域名为API的URL http://192.168.4.111:9000在填入AK、SK,点击测试即可立即备份备份完成5、进行还原测试误删数据库由于王工上年纪老眼昏花,不小心删除了zabbix数据库,不稳啦!zabbix崩溃进行租户恢复恢复完成创建了新的租户,将原租户改名,新租户改为原来的名,这样业务就不用动了业务恢复了,王工又稳啦!{lamp/}六、集群、租户扩缩容1、集群扩容添加主机-集群管理-添加OBServer、新增Zone添加主机OCP云平台-主机-添加主机主机还是要按之前标准化进行环境修复,修复好再添加再次进行标准化OCP云平台-集群-概览-添加OBServer一段时间后部署模式变为集群 (3-3-3)新增Zone与之相同2、集群缩容https://www.oceanbase.com/docs/common-oceanbase-database-cn-1000000002013120删除OBServer时自动进行Unit迁出完成缩容我这边删除114 115 116三台主机批量删除删除中缩容完成3、租户扩容进入租户修改UnitOCP云平台-租户-概览-修改Unit如,将配置修改为S2,Unit修改为2扩容成功4、租户缩容如,将配置修改为S1,Unit修改为1缩容完成{lamp/}七、ODC开发者中心OceanBase 开发者中心(OceanBase Developer Center,ODC)是开源的企业级数据库协同开发工具,有桌面版、Web 版两种产品形态。 ODC Web 版提供了个人空间和团队空间两种工作模式。个人空间适合个人开发者使用,为您在浏览器端提供桌面版的体验;团队空间适合开发者和 DBA 协同使用,既是开发工具也是管控协同平台。 ODC 的代码维护在 Github,单击查看详情,加入 ODC 开源社区,一起创造 开发者和 DBA 喜爱的数据库协同开发工具。https://www.oceanbase.com/docs/odc{message type="info" content="注意:按官方教程你很可能装不上,还是看我的吧"/}1、下载OceanBase 开发者中心web镜像上传到OMS主机,我将ODC安装在OMS主机,ODC为docker镜像https://www.oceanbase.com/softwarecenter2、为ODC创建一个mysql租户并创建一个数据库创建tntodc租户 tntodc数据库 root用户{message type="info" content="注意:数据库用户我测试用普通用户无法部署ODC,需要root用户"/}3、加载镜像gunzip -c obodc4.3.3-bp2.tar.gz | docker load查看镜像docker images REPOSITORY TAG IMAGE ID CREATED SIZE reg.docker.alibaba-inc.com/oceanbase/oms feature_4.2.8_ce d56598287295 7 weeks ago 10.9GB oceanbase/odc 4.3.3_bp2 98a74ab3fbe1 7 weeks ago 1.75GB 4、创建安装脚本odcinstall.sh#!/usr/bin/env bash mkdir -p /tntodc/log/odc mkdir -p /tntodc/data/odc docker run -v /tntodc/log/odc:/opt/odc/log -v /tntodc/data/odc:/opt/odc/data \ -d -i -p 8989:8989 --cpu-period 100000 --cpu-quota 400000 --memory 8G --name "obodc" \ -e "DATABASE_HOST=192.168.4.102" \ -e "DATABASE_PORT=2883" \ -e "DATABASE_USERNAME=root@tntodc#tntob" \ -e "DATABASE_PASSWORD=78ABcd##123" \ -e "DATABASE_NAME=tntodc" \ -e "ODC_ADMIN_INITIAL_PASSWORD=78ABcd##123" \ oceanbase/odc:4.3.3_bp2 注意Shell 环境下,字符串中包含 !、$ 等特殊字符时,变量值需要使用单引号。例如:DATABASE_PASSWORD='11111!'。参数 ODC_ADMIN_INITIAL_PASSWORD 用于指定 ODC 管理员账号的初始密码。设置的初始密码需要须满足以下条件:至少 2 个数字。至少 2 个大写字母。至少 2 个小写字母。至少 2 个特殊字符,特殊字符的范围为 ._+@#$%。不包含空格和其他特殊字符,长度为 8-32。{lamp/}5、安装bash odcinstall.sh6、登录成功八、OBProxy集群keepalived高可用主备VIP部署keepalived介绍请看王工其他文章1、安装keepalived两台OBProxy主机分别安装keepalivedyum install -y keepalived2、配置keepalived两台OBProxy主机分别创建Proxy存活检测脚本vi /etc/keepalived/check_obproxy.sh#!/bin/bash # 检查2883端口是否有监听 if ss -tuln | grep -q ':2883\b'; then exit 0 # 检测成功,返回0 else exit 1 # 检测失败,返回1 fitntproxy1配置执行权限chmod +x /etc/keepalived/check_obproxy.sh配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_script check_obproxy { script "/etc/keepalived/check_obproxy.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } unicast_src_ip 192.168.4.102 #本机ip unicast_peer { 192.168.4.103 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.99/24 #VIP(自己网段的) } track_script { check_obproxy } }tntproxy2配置执行权限chmod +x /etc/keepalived/check_obproxy.sh配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_script check_obproxy { script "/etc/keepalived/check_obproxy.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } unicast_src_ip 192.168.4.103 #本机ip unicast_peer { 192.168.4.102 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.99/24 #抢占的VIP也一样 } track_script { check_obproxy } }3、启动服务systemctl enable --now keepalived4、高可用测试将zabbix数据库指向VIP,连续ping 192.168.4.99,并查看zabbix服务状态obproxy1关机,查看ping和zabbix状态正常,业务几乎无感来自 192.168.4.99 的回复: 字节=32 时间=15ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=21ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=28ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=2ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=49ms TTL=63 来自 192.168.4.99 的回复: 字节=32 时间=1ms TTL=63obproxy2获得VIPinet 192.168.4.103/24 brd 192.168.4.255 scope global noprefixroute ens192 valid_lft forever preferred_lft forever inet 192.168.4.99/24 scope global secondary ens192 valid_lft forever preferred_lft forever obproxy1开机,obproxy服务启动成功后,自动抢回VIP inet 192.168.4.102/24 brd 192.168.4.255 scope global noprefixroute ens192 valid_lft forever preferred_lft forever inet 192.168.4.99/24 scope global secondary ens192 valid_lft forever preferred_lft forever 5、测试结论高可用正常,VIP正常九、故障处理1、任意一台OBServer主机故障关机1台OBServer主机,集群无影响,一段时间后Zone内另一台主机接管此OBServer功能开机此OBServer,一段时间后集群自动修复此主机并上线2、{lamp/}十、不停机滚动升级V4.3.5_CE_BP1_HF1版本信息发布时间:2025 年 04 月 30 日下载数据库rpm安装包oceanbase-ce-4.3.5.1-101010042025042417.el8.x86_64.rpmhttps://www.oceanbase.com/softwarecenter登录OCP平台,进入集群,升级版本上传安装包升级路经确认提示 集群升级缺少社区版依赖包:[oceanbase-ce-utils-4.3.5.1-101010042025042417.x86_64, oceanbase-ce-libs-4.3.5.1-101010042025042417.x86_64]下载并上传oceanbase-ce-libs-4.3.5.1-101010042025042417.el8.x86_64.rpmoceanbase-ce-utils-4.3.5.1-101010042025042417.el8.x86_64.rpm升级中升级前版本升级中如果出现任务失败,根据情况可点击重试,我点了四五次就完成了升级后版本,升级完成,升级过程中业务无感知{lamp/}十一、总结太强了 -
 Zabbix7 keepalived VIP高可用部署 对接 OceanBase高可用集群 {alert type="info"}文中密码均为随机生成,网段和主机实验完成后删除{/alert}一、方案规划Anolis8系统192.168.4.50 tntzabbix7虚拟地址 192.168.4.51 tntzabbix7-01 192.168.4.52 tntzabbix7-02 192.168.4.99 oceanbase高可用VIP数据库oceanbase高可用数据库集群见其他文章,为zabbix7创建数据库https://90apt.com/5580二、数据库准备创建zabbix7租户,创建zabbix7用户和数据库,utf8mb4_bin编码mysql -h192.168.4.99 -P2883 -uzabbix7@zabbix7#tntob -p Aq1[R!KM3%,|{sJ?UJ5;u]数据库具备VIP高可用能力三、安装zabbix1、准备主机准备两台主机,关闭防火墙systemctl stop firewalld && systemctl disable firewalld2、安装zabbix两台主机均安装rpm -Uvh https://repo.zabbix.com/zabbix/7.0/alma/8/x86_64/zabbix-release-latest-7.0.el8.noarch.rpm dnf clean all dnf module list php dnf module reset php dnf module install php:8.0 dnf install zabbix-server-mysql zabbix-web-mysql zabbix-nginx-conf zabbix-sql-scripts zabbix-selinux-policy zabbix-agent2 dnf install zabbix-agent2-plugin-mongodb zabbix-agent2-plugin-mssql zabbix-agent2-plugin-postgresql01主机导入数据库先给予zabbix7用户权限,主要是为了给他触发器权限登录zabbix7租户的root用户 yum install mysql mysql -h192.168.4.99 -P2883 -uroot@zabbix7#tntob -p mysql> grant all privileges on zabbix7.* to zabbix7@"%"; mysql> set global log_bin_trust_function_creators = 1; Query OK, 0 rows affected (0.15 sec)修改租户的ob_query_timeout参数,防止导入超时ob_query_timeout 100000000再导入数据库zcat /usr/share/zabbix-sql-scripts/mysql/server.sql.gz | mysql --default-character-set=utf8mb4 -h192.168.4.99 -P2883 -uzabbix7@zabbix7#tntob -p zabbix7无报错就是导入成功导入数据库架构后禁用log_bin_trust_function_creators选项mysql -h192.168.4.99 -P2883 -uroot@zabbix7#tntob -p mysql> set global log_bin_trust_function_creators = 0; mysql> quit;为Zabbix server配置数据库编辑配置文件 /etc/zabbix/zabbix_server.confDBHost=192.168.4.99 DBName=zabbix7 DBUser=zabbix7@zabbix7#tntob DBPassword=Aq1[R!KM3%,|{sJ?UJ5;u] DBPort=2883 HANodeName=tntzabbix7-01 NodeAddress=192.168.4.51:10051配置默认端口和主机名/etc/nginx/conf.d/zabbix.conflisten 8080;启动Zabbix server和agent进程,并为它们设置开机自启systemctl restart zabbix-server zabbix-agent2 nginx php-fpm systemctl enable zabbix-server zabbix-agent2 nginx php-fpm查看日志是否有异常cat /var/log/zabbix/zabbix_server.log数据库提示 Unable to start Zabbix server due to unsupported MySQL database version (8.00.00). Must be at least (8.00.30).修改Oceanbase数据库将版本改为8.0.30 重启服务再次查看日志正常systemctl restart zabbix-server zabbix-agent2 nginx php-fpm cat /var/log/zabbix/zabbix_server.log02主机为Zabbix server配置数据库编辑配置文件 /etc/zabbix/zabbix_server.confDBHost=192.168.4.99 DBName=zabbix7 DBUser=zabbix7@zabbix7#tntob DBPassword=Aq1[R!KM3%,|{sJ?UJ5;u] DBPort=2883 HANodeName=tntzabbix7-02 NodeAddress=192.168.4.52:10051配置默认端口和主机名/etc/nginx/conf.d/zabbix.conflisten 8080;启动Zabbix server和agent进程,并为它们设置开机自启systemctl restart zabbix-server zabbix-agent2 nginx php-fpm systemctl enable zabbix-server zabbix-agent2 nginx php-fpm查看日志是否有异常cat /var/log/zabbix/zabbix_server.log无异常"tntzabbix7-02" node started in "standby" mode3、配置zabbix配置01主机http://192.168.4.51:8080/数据库连接主机名和时区默认账号密码为Admin zabbix配置02主机http://192.168.4.52:8080/与01主机相同,只有主机名不同两台主机的状态四、keepalived高可用部署zabbix高可用切换时,备用主机10051端口关闭,可以利用此端口配置keepalived配置01主机安装keealivedyum install -y keepalived编写zabbix高可用检测脚本vi /etc/keepalived/check_zabbix.sh#!/bin/bash # 检查10051端口是否有监听 if ss -tuln | grep -q ':10051\b'; then exit 0 # 检测成功,返回0 else exit 1 # 检测失败,返回1 fi执行权限chmod +x /etc/keepalived/check_zabbix.sh编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_script check_zabbix { script "/etc/keepalived/check_zabbix.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } unicast_src_ip 192.168.4.51 #本机ip unicast_peer { 192.168.4.52 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.50/24 #VIP(自己网段的) } track_script { check_zabbix } }启动服务systemctl enable --now keepalived配置02主机安装keealivedyum install -y keepalived编写zabbix高可用检测脚本vi /etc/keepalived/check_zabbix.sh#!/bin/bash # 检查10051端口是否有监听 if ss -tuln | grep -q ':10051\b'; then exit 0 # 检测成功,返回0 else exit 1 # 检测失败,返回1 fi执行权限chmod +x /etc/keepalived/check_zabbix.sh编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_script check_zabbix { script "/etc/keepalived/check_zabbix.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } unicast_src_ip 192.168.4.52 #本机ip unicast_peer { 192.168.4.51 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.50/24 #抢占的VIP也一样 } track_script { check_zabbix } }启动服务systemctl enable --now keepalived五、高可用测试登录http://192.168.4.50:8080/显示为tntzabbix7-02tntzabbix7-02重启,刷新网页,切换为zabbix7-01zabbix7-01关闭zabbix服务[root@tntzabbix7-01 ~]# systemctl stop zabbix-server刷新网页,切换为tntzabbix7-02启动zabbix7-01服务后并不会主动切回01[root@tntzabbix7-01 ~]# systemctl start zabbix-serverzabbix7-02关闭zabbix服务[root@tntzabbix7-02 ~]# systemctl stop zabbix-server 刷新网页,切换为tntzabbix7-01测试结论高可用能力正常,满足需求。六、zabbix server地址注意,在配置agent的时候,虽然HA地址是192.168.4.50但配置服务器仍要配置server的地址,使用英文逗号间隔192.168.4.51,192.168.4.52七、其他其他配置可查看我的zabbix6文章https://90apt.com/search/zabbix6/八、小结爽
Zabbix7 keepalived VIP高可用部署 对接 OceanBase高可用集群 {alert type="info"}文中密码均为随机生成,网段和主机实验完成后删除{/alert}一、方案规划Anolis8系统192.168.4.50 tntzabbix7虚拟地址 192.168.4.51 tntzabbix7-01 192.168.4.52 tntzabbix7-02 192.168.4.99 oceanbase高可用VIP数据库oceanbase高可用数据库集群见其他文章,为zabbix7创建数据库https://90apt.com/5580二、数据库准备创建zabbix7租户,创建zabbix7用户和数据库,utf8mb4_bin编码mysql -h192.168.4.99 -P2883 -uzabbix7@zabbix7#tntob -p Aq1[R!KM3%,|{sJ?UJ5;u]数据库具备VIP高可用能力三、安装zabbix1、准备主机准备两台主机,关闭防火墙systemctl stop firewalld && systemctl disable firewalld2、安装zabbix两台主机均安装rpm -Uvh https://repo.zabbix.com/zabbix/7.0/alma/8/x86_64/zabbix-release-latest-7.0.el8.noarch.rpm dnf clean all dnf module list php dnf module reset php dnf module install php:8.0 dnf install zabbix-server-mysql zabbix-web-mysql zabbix-nginx-conf zabbix-sql-scripts zabbix-selinux-policy zabbix-agent2 dnf install zabbix-agent2-plugin-mongodb zabbix-agent2-plugin-mssql zabbix-agent2-plugin-postgresql01主机导入数据库先给予zabbix7用户权限,主要是为了给他触发器权限登录zabbix7租户的root用户 yum install mysql mysql -h192.168.4.99 -P2883 -uroot@zabbix7#tntob -p mysql> grant all privileges on zabbix7.* to zabbix7@"%"; mysql> set global log_bin_trust_function_creators = 1; Query OK, 0 rows affected (0.15 sec)修改租户的ob_query_timeout参数,防止导入超时ob_query_timeout 100000000再导入数据库zcat /usr/share/zabbix-sql-scripts/mysql/server.sql.gz | mysql --default-character-set=utf8mb4 -h192.168.4.99 -P2883 -uzabbix7@zabbix7#tntob -p zabbix7无报错就是导入成功导入数据库架构后禁用log_bin_trust_function_creators选项mysql -h192.168.4.99 -P2883 -uroot@zabbix7#tntob -p mysql> set global log_bin_trust_function_creators = 0; mysql> quit;为Zabbix server配置数据库编辑配置文件 /etc/zabbix/zabbix_server.confDBHost=192.168.4.99 DBName=zabbix7 DBUser=zabbix7@zabbix7#tntob DBPassword=Aq1[R!KM3%,|{sJ?UJ5;u] DBPort=2883 HANodeName=tntzabbix7-01 NodeAddress=192.168.4.51:10051配置默认端口和主机名/etc/nginx/conf.d/zabbix.conflisten 8080;启动Zabbix server和agent进程,并为它们设置开机自启systemctl restart zabbix-server zabbix-agent2 nginx php-fpm systemctl enable zabbix-server zabbix-agent2 nginx php-fpm查看日志是否有异常cat /var/log/zabbix/zabbix_server.log数据库提示 Unable to start Zabbix server due to unsupported MySQL database version (8.00.00). Must be at least (8.00.30).修改Oceanbase数据库将版本改为8.0.30 重启服务再次查看日志正常systemctl restart zabbix-server zabbix-agent2 nginx php-fpm cat /var/log/zabbix/zabbix_server.log02主机为Zabbix server配置数据库编辑配置文件 /etc/zabbix/zabbix_server.confDBHost=192.168.4.99 DBName=zabbix7 DBUser=zabbix7@zabbix7#tntob DBPassword=Aq1[R!KM3%,|{sJ?UJ5;u] DBPort=2883 HANodeName=tntzabbix7-02 NodeAddress=192.168.4.52:10051配置默认端口和主机名/etc/nginx/conf.d/zabbix.conflisten 8080;启动Zabbix server和agent进程,并为它们设置开机自启systemctl restart zabbix-server zabbix-agent2 nginx php-fpm systemctl enable zabbix-server zabbix-agent2 nginx php-fpm查看日志是否有异常cat /var/log/zabbix/zabbix_server.log无异常"tntzabbix7-02" node started in "standby" mode3、配置zabbix配置01主机http://192.168.4.51:8080/数据库连接主机名和时区默认账号密码为Admin zabbix配置02主机http://192.168.4.52:8080/与01主机相同,只有主机名不同两台主机的状态四、keepalived高可用部署zabbix高可用切换时,备用主机10051端口关闭,可以利用此端口配置keepalived配置01主机安装keealivedyum install -y keepalived编写zabbix高可用检测脚本vi /etc/keepalived/check_zabbix.sh#!/bin/bash # 检查10051端口是否有监听 if ss -tuln | grep -q ':10051\b'; then exit 0 # 检测成功,返回0 else exit 1 # 检测失败,返回1 fi执行权限chmod +x /etc/keepalived/check_zabbix.sh编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_script check_zabbix { script "/etc/keepalived/check_zabbix.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } unicast_src_ip 192.168.4.51 #本机ip unicast_peer { 192.168.4.52 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.50/24 #VIP(自己网段的) } track_script { check_zabbix } }启动服务systemctl enable --now keepalived配置02主机安装keealivedyum install -y keepalived编写zabbix高可用检测脚本vi /etc/keepalived/check_zabbix.sh#!/bin/bash # 检查10051端口是否有监听 if ss -tuln | grep -q ':10051\b'; then exit 0 # 检测成功,返回0 else exit 1 # 检测失败,返回1 fi执行权限chmod +x /etc/keepalived/check_zabbix.sh编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_script check_zabbix { script "/etc/keepalived/check_zabbix.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } unicast_src_ip 192.168.4.52 #本机ip unicast_peer { 192.168.4.51 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.50/24 #抢占的VIP也一样 } track_script { check_zabbix } }启动服务systemctl enable --now keepalived五、高可用测试登录http://192.168.4.50:8080/显示为tntzabbix7-02tntzabbix7-02重启,刷新网页,切换为zabbix7-01zabbix7-01关闭zabbix服务[root@tntzabbix7-01 ~]# systemctl stop zabbix-server刷新网页,切换为tntzabbix7-02启动zabbix7-01服务后并不会主动切回01[root@tntzabbix7-01 ~]# systemctl start zabbix-serverzabbix7-02关闭zabbix服务[root@tntzabbix7-02 ~]# systemctl stop zabbix-server 刷新网页,切换为tntzabbix7-01测试结论高可用能力正常,满足需求。六、zabbix server地址注意,在配置agent的时候,虽然HA地址是192.168.4.50但配置服务器仍要配置server的地址,使用英文逗号间隔192.168.4.51,192.168.4.52七、其他其他配置可查看我的zabbix6文章https://90apt.com/search/zabbix6/八、小结爽 -

-
 keepalived 高可用主备VIP快速部署 IP规划192.168.4.20 VIP虚拟地址 192.168.4.21 keepalived1 192.168.4.22 keepalived2网卡为 ens192系统为Anolis8 龙蜥8关闭防火墙systemctl stop firewalld && systemctl disable firewalldkeepalived默认使用112端口{lamp/}软件安装主机1192.168.4.21 keepalived1安装yum install -y keepalived配置文件备份cp /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak 编辑vi /etc/keepalived/keepalived.conf ! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } virtual_ipaddress { 192.168.4.20/24 #VIP(自己网段的) } }主机2192.168.4.22 keepalived2安装软件yum install -y keepalived配置文件备份cp /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak编辑vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } virtual_ipaddress { 192.168.4.20/24 #抢占的VIP也一样 } }启动服务systemctl enable --now keepalived重启主机1,VIP自动漂移到主机2,启动主机1,VIP漂回来{lamp/}配置业务在两台主机上安装nginxyum install nginx -y systemctl enable --now nginx两台主机显示不同网页主机1echo "keepalived1 nginx" > /usr/share/nginx/html/index.html主机2echo "keepalived2 nginx" > /usr/share/nginx/html/index.html两台主机访问nginx业务正常{lamp/}配置nginx高可用检测两台主机均编写脚本vi /etc/keepalived/check_nginx.sh通过端口监听判断业务是否正常,几乎适用于所有业务,如MQ、nginx、OBProxy等等#!/bin/bash # 检查80端口是否有监听 if ss -tuln | grep -q ':80\b'; then exit 0 # 检测成功,返回0 else exit 1 # 检测失败,返回1 fi配置keepalived1192.168.4.21 keepalived1执行权限chmod +x /etc/keepalived/check_nginx.sh编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_script check_nginx { script "/etc/keepalived/check_nginx.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } virtual_ipaddress { 192.168.4.20/24 #VIP(自己网段的) } track_script { check_nginx } }配置keepalived2192.168.4.22 keepalived2执行权限chmod +x /etc/keepalived/check_nginx.sh编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_script check_nginx { script "/etc/keepalived/check_nginx.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } virtual_ipaddress { 192.168.4.20/24 #抢占的VIP也一样 } track_script { check_nginx } }改完配置文件两台主机都需要重启keepalived服务关闭主机1的nginx服务,VIP自动漂移到主机2,启动主机1的nginx服务,VIP漂回来{lamp/}配置为单播,抵御脑裂配置keepalived1192.168.4.21 keepalived1编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_script check_nginx { script "/etc/keepalived/check_nginx.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } unicast_src_ip 192.168.4.21 #本机ip unicast_peer { 192.168.4.22 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.20/24 #VIP(自己网段的) } track_script { check_nginx } }配置keepalived2192.168.4.22 keepalived2编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_script check_nginx { script "/etc/keepalived/check_nginx.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } unicast_src_ip 192.168.4.22 #本机ip unicast_peer { 192.168.4.21 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.20/24 #抢占的VIP也一样 } track_script { check_nginx } }改完配置文件两台主机都需要重启keepalived服务{lamp/}总结简单好用!
keepalived 高可用主备VIP快速部署 IP规划192.168.4.20 VIP虚拟地址 192.168.4.21 keepalived1 192.168.4.22 keepalived2网卡为 ens192系统为Anolis8 龙蜥8关闭防火墙systemctl stop firewalld && systemctl disable firewalldkeepalived默认使用112端口{lamp/}软件安装主机1192.168.4.21 keepalived1安装yum install -y keepalived配置文件备份cp /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak 编辑vi /etc/keepalived/keepalived.conf ! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } virtual_ipaddress { 192.168.4.20/24 #VIP(自己网段的) } }主机2192.168.4.22 keepalived2安装软件yum install -y keepalived配置文件备份cp /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak编辑vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } virtual_ipaddress { 192.168.4.20/24 #抢占的VIP也一样 } }启动服务systemctl enable --now keepalived重启主机1,VIP自动漂移到主机2,启动主机1,VIP漂回来{lamp/}配置业务在两台主机上安装nginxyum install nginx -y systemctl enable --now nginx两台主机显示不同网页主机1echo "keepalived1 nginx" > /usr/share/nginx/html/index.html主机2echo "keepalived2 nginx" > /usr/share/nginx/html/index.html两台主机访问nginx业务正常{lamp/}配置nginx高可用检测两台主机均编写脚本vi /etc/keepalived/check_nginx.sh通过端口监听判断业务是否正常,几乎适用于所有业务,如MQ、nginx、OBProxy等等#!/bin/bash # 检查80端口是否有监听 if ss -tuln | grep -q ':80\b'; then exit 0 # 检测成功,返回0 else exit 1 # 检测失败,返回1 fi配置keepalived1192.168.4.21 keepalived1执行权限chmod +x /etc/keepalived/check_nginx.sh编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_script check_nginx { script "/etc/keepalived/check_nginx.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } virtual_ipaddress { 192.168.4.20/24 #VIP(自己网段的) } track_script { check_nginx } }配置keepalived2192.168.4.22 keepalived2执行权限chmod +x /etc/keepalived/check_nginx.sh编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_script check_nginx { script "/etc/keepalived/check_nginx.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } virtual_ipaddress { 192.168.4.20/24 #抢占的VIP也一样 } track_script { check_nginx } }改完配置文件两台主机都需要重启keepalived服务关闭主机1的nginx服务,VIP自动漂移到主机2,启动主机1的nginx服务,VIP漂回来{lamp/}配置为单播,抵御脑裂配置keepalived1192.168.4.21 keepalived1编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived1 #只是名字而已,辅节点改为keepalived2(两个名字一定不能一样) } vrrp_script check_nginx { script "/etc/keepalived/check_nginx.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state MASTER #定义主还是备,备用的话写backup interface ens192 #VIP绑定接口 virtual_router_id 66 #整个集群的调度器一致(在同一个集群) priority 100 #(优先权)back改为50(50一间隔) advert_int 1 #发包 authentication { auth_type PASS #主备节点认证 auth_pass 1111 } unicast_src_ip 192.168.4.21 #本机ip unicast_peer { 192.168.4.22 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.20/24 #VIP(自己网段的) } track_script { check_nginx } }配置keepalived2192.168.4.22 keepalived2编辑配置文件vi /etc/keepalived/keepalived.conf! Configuration File for keepalived global_defs { router_id keepalived2 } vrrp_script check_nginx { script "/etc/keepalived/check_nginx.sh" interval 2 #每2秒执行一次 } vrrp_instance VI_1 { state BACKUP #设置为backup interface ens192 nopreempt #设置到back上面,不抢占资源 virtual_router_id 66 priority 50 #辅助改为50 advert_int 1 #检测间隔1s authentication { auth_type PASS auth_pass 1111 #认证类型和密码主备一样,要不然无法互相认证 } unicast_src_ip 192.168.4.22 #本机ip unicast_peer { 192.168.4.21 #其他机器ip,可多个 } virtual_ipaddress { 192.168.4.20/24 #抢占的VIP也一样 } track_script { check_nginx } }改完配置文件两台主机都需要重启keepalived服务{lamp/}总结简单好用! -

-

-
 2017款宝骏510天宝中控开通carplay,附资源。 下载地址:链接:https://pan.baidu.com/s/1B_RiCfHHFwFhaFWcsRBXlg 提取码:5e9e 2017款宝骏510的中控有天宝和航盛两个供应商,并且在苹果官方的carplay认证中也有宝骏的几款车型,航盛的刷机包其实早就公开了,但天宝的确很诡异的没有公开过。从方向盘可以看到siri呼叫按键。如何确定车机的版本呢?我们可以点击中控的主页按钮。点击设置点击系统如图所示,TP即为天宝,如果你是HSAE就是航盛的车机,网上都可以下载刷机包。刷机准备:1、准备一个好点的U盘,我用的“什么值得买”推的夏科u盘,用电脑格式化为FAT32格式。(如果你非要想知道为什么要用FAT32格式,其实也简单,因为这个车机是linux系统,所以理论上你也可以用ext3,但肯定不能是微软的NTFS)2、下载文件解压缩,把update-CN180S目录和upgrade.bin放到U盘根目录,不要有其他文件。3、拔掉点烟器!打开汽车钥匙电源打火,怠速稳定以后插入U盘,几秒后机器自动跳转到升级界面,更新第一个 系统软件4、升级过程大概15分钟左右,有百分比显示,升级完成后会自动重启,然后再次进入主界面,此时才能拔掉U盘。成功升级后,主界面会多出一个carplay图标,插入iPhone数据线(质量差的容易断开,最好用mfi认证的),图标就可以点击进入了。爽哦
2017款宝骏510天宝中控开通carplay,附资源。 下载地址:链接:https://pan.baidu.com/s/1B_RiCfHHFwFhaFWcsRBXlg 提取码:5e9e 2017款宝骏510的中控有天宝和航盛两个供应商,并且在苹果官方的carplay认证中也有宝骏的几款车型,航盛的刷机包其实早就公开了,但天宝的确很诡异的没有公开过。从方向盘可以看到siri呼叫按键。如何确定车机的版本呢?我们可以点击中控的主页按钮。点击设置点击系统如图所示,TP即为天宝,如果你是HSAE就是航盛的车机,网上都可以下载刷机包。刷机准备:1、准备一个好点的U盘,我用的“什么值得买”推的夏科u盘,用电脑格式化为FAT32格式。(如果你非要想知道为什么要用FAT32格式,其实也简单,因为这个车机是linux系统,所以理论上你也可以用ext3,但肯定不能是微软的NTFS)2、下载文件解压缩,把update-CN180S目录和upgrade.bin放到U盘根目录,不要有其他文件。3、拔掉点烟器!打开汽车钥匙电源打火,怠速稳定以后插入U盘,几秒后机器自动跳转到升级界面,更新第一个 系统软件4、升级过程大概15分钟左右,有百分比显示,升级完成后会自动重启,然后再次进入主界面,此时才能拔掉U盘。成功升级后,主界面会多出一个carplay图标,插入iPhone数据线(质量差的容易断开,最好用mfi认证的),图标就可以点击进入了。爽哦 -
 宝骏510 2017款 1.5L 自动时尚 更换途虎 东风轮胎DU01 205/60R16 92V 单价171元 4条684元 本人的宝骏510在今年已经进入了第8个年头,原厂的佳通轮胎已经老化严重趁着途虎养车APP轮胎打折,下单了4条轮胎,东风轮胎DU01 205/60R16 92V 单价171元 4条684元价格里包含了轮胎的安装费、动平衡、常规检测、气门嘴轮胎次日达,预约了周末更换,在途虎工场店轮胎到店后查看出厂日期为25年13、14周,非对称花纹,分内外进行了常规检测,灯光、喇叭、防冻液、刹车油含水量、刹车片厚度、橡胶衬套异响等底盘整体无锈蚀排查到后减震漏油后减震更换,配件+工时费536拆卸后发现后减震完全失效后减震器、轮胎更换中,在更换中螺栓使用了扭矩扳手打扭矩更换了全新的气门嘴和气门帽整体评价途虎:明码标价、螺栓打扭矩,比较满意;但轮胎黄点没有对准气门芯,虽然没什么影响,但不舒服(黄点为轮胎最轻处,对准气门芯处可以减少平衡块用量)轮胎:更换后行驶了40多公里,比老轮胎静音多了,无其他感觉
宝骏510 2017款 1.5L 自动时尚 更换途虎 东风轮胎DU01 205/60R16 92V 单价171元 4条684元 本人的宝骏510在今年已经进入了第8个年头,原厂的佳通轮胎已经老化严重趁着途虎养车APP轮胎打折,下单了4条轮胎,东风轮胎DU01 205/60R16 92V 单价171元 4条684元价格里包含了轮胎的安装费、动平衡、常规检测、气门嘴轮胎次日达,预约了周末更换,在途虎工场店轮胎到店后查看出厂日期为25年13、14周,非对称花纹,分内外进行了常规检测,灯光、喇叭、防冻液、刹车油含水量、刹车片厚度、橡胶衬套异响等底盘整体无锈蚀排查到后减震漏油后减震更换,配件+工时费536拆卸后发现后减震完全失效后减震器、轮胎更换中,在更换中螺栓使用了扭矩扳手打扭矩更换了全新的气门嘴和气门帽整体评价途虎:明码标价、螺栓打扭矩,比较满意;但轮胎黄点没有对准气门芯,虽然没什么影响,但不舒服(黄点为轮胎最轻处,对准气门芯处可以减少平衡块用量)轮胎:更换后行驶了40多公里,比老轮胎静音多了,无其他感觉 -
 ALMA Linux 8飞速搭建zabbix6LTS、微信邮箱短信报警、windows、linux、交换机、vCenter监控、grafana面板、modbus动环采集、ZbxTable分析系统、Mysql、MSsql数据库监控、分组报警、对接oceanbase数据库 一、环境 zabbix所在服务器系统为alma8,zabbix6要求的mariadb版本为10.5-10.6,同时zabbix提供了zabbix-selinux-policy来配置selinux,所以安装中也不再要求关闭selinux。二、安装zabbix 官方安装帮助页面,安装方法随版本更新,官方更新更快https://www.zabbix.com/cn/download1、配置zabbix 软件源rpm -Uvh https://repo.zabbix.com/zabbix/6.0/rhel/8/x86_64/zabbix-release-6.0-4.el8.noarch.rpm dnf clean all2、安装zabbix-server和zabbix-agent2dnf install zabbix-server-mysql zabbix-web-mysql zabbix-apache-conf zabbix-sql-scripts zabbix-selinux-policy zabbix-agent23、安装数据库配置mariabd源 /etc/yum.repos.d/MariaDB.repo# MariaDB 10.6 CentOS repository list - created 2023-02-02 03:14 UTC # https://mariadb.org/download/ [mariadb] name = MariaDB baseurl = https://mirrors.aliyun.com/mariadb/yum/10.6/centos8-amd64 module_hotfixes=1 gpgkey=https://mirrors.aliyun.com/mariadb/yum/RPM-GPG-KEY-MariaDB gpgcheck=1安装数据库、启动、并设置开机启动dnf clean all dnf install mariadb-server systemctl enable --now mariadb4、进行MariaDB数据库初始化mariadb-secure-installation首先是设置密码,会提示先输入密码 Enter current password for root (enter for none):<–初次运行直接回车 Set root password? [Y/n] <– 是否设置root用户密码,输入y并回车 New password: <– 设置root用户的密码 Re-enter new password: <– 再输入一次你设置的密码 Remove anonymous users? [Y/n] <– 是否删除匿名用户 Disallow root login remotely? [Y/n] <–是否禁止root远程登录 Remove test database and access to it? [Y/n] <– 是否删除test数据库 Reload privilege tables now? [Y/n] <– 是否重新加载权限表5、初始化并导入zabbix数据库 mysql -uroot -p登录mariadb> create database zabbix character set utf8mb4 collate utf8mb4_bin; mariadb> create user zabbix@localhost identified by 'password123'; mariadb> grant all privileges on zabbix.* to zabbix@localhost; mariadb> set global log_bin_trust_function_creators = 1; mariadb> quit;导入初始架构和数据,系统将提示您输入新创建的密码zcat /usr/share/zabbix-sql-scripts/mysql/server.sql.gz | mysql --default-character-set=utf8mb4 -uzabbix -p zabbix导入数据库架构后禁用log_bin_trust_function_creators选项mysql -uroot -p mariadb> set global log_bin_trust_function_creators = 0; mariadb> quit;6、配置数据库密码编辑配置文件 /etc/zabbix/zabbix_server.confDBPassword=password1237、配置PHP时区编辑配置文件 /etc/php-fpm.d/zabbix.confphp_value[date.timezone] = Asia/Shanghai8、启动并设置开机启动systemctl enable --now zabbix-server zabbix-agent2 httpd php-fpm9、查看是否有错误信息 cat /var/log/zabbix/zabbix_server.log10、防火墙开放端口firewall-cmd --add-port=80/tcp --permanent firewall-cmd --permanent --add-port=10050-10051/tcp firewall-cmd --reload firewall-cmd --list-ports firewall-cmd --list-services11、替换zabbix自带字体,解决中文乱码百度下载Noto Sans S Chinese字体替换掉默认使用的DejaVuSanscp NotoSansSC-Regular.otf /usr/share/fonts/dejavu/DejaVuSans.ttf12、调整zabbix缓存/etc/zabbix/zabbix_server.confCacheSize=1G13、调整ping进程数/etc/zabbix/zabbix_server.confStartPingers=16三、服务端配置 1、连接到新安装的Zabbix前端: http://server_ip/zabbix注意,mariadb也属于mysql数据库类型2、登录zabbix账号Admin 密码zabbix前端配置完成请务必修改密码四、企业微信消息推送 注意:为了企业的数据安全,从2022年6月20号20点之后,新开启的通讯录同步助手与新创建的自建应用必须在管理端配置可信IP,仅配置的可信IP能调用接口。当前时间2023年6月,企业微信应用验证必须与企业名相同,请考虑使用企业微信机器人推送。1、在企业微信 - 我的企业 - 企业信息 - 企业ID 2、创建zabbix机器人应用企业微信后台 - 应用管理 - 应用 - 创建应用 先进行网页授权及JS-SDK可信域名下的网页可使用网页授权及JS-SDK可信IP位于自行创建的应用-开发接口-企业可信IP 可信IP即服务器所在网络的外网IP,可打开https://ifconfig.me/快速查看,如果企业机房接入多条外网宽带,把外网宽带的IP全都写上3、查看Agentld和Secret 4、准备zabbix机器人脚本环境dnf -y install epel-release dnf -y install python2-pip pip2 install requests查询脚本存放位置cat /etc/zabbix/zabbix_server.conf | grep AlertScript可以看到脚本存放在/usr/lib/zabbix/alertscripts目录中编写脚本 weixin.py并放入上面的目录 ,填入上面获得的三个值#!/usr/bin/env python2 #-*- coding: utf-8 -*- import requests import sys import os import json import logging logging . basicConfig ( level = logging . DEBUG , format = ' %(asctime)s , %(filename)s , %(levelname)s , %(message)s ' , datefmt = ' %a , %d %b %Y %H:%M:%S' , filename = os . path . join ( '/tmp' , 'weixin.log' ), filemode = 'a' ) corpid = 'ww36e' appsecret = '5yFNqeTjrr3I' agentid = 1000002 token_url = 'https://qyapi.weixin.qq.com/cgi-bin/gettoken?corpid=' + corpid + '&corpsecret=' + appsecret req = requests . get ( token_url ) accesstoken = req . json ()[ 'access_token' ] msgsend_url = 'https://qyapi.weixin.qq.com/cgi-bin/message/send?access_token=' + accesstoken touser = sys . argv [ 1 ] subject = sys . argv [ 2 ] #toparty='3|4|5|6' message = sys . argv [ 2 ] + " \n\n " + sys . argv [ 3 ] params ={ "touser" : touser , # "toparty": toparty, "msgtype" : "text" , "agentid" : agentid , "text" : { "content" : message }, "safe" : 0 } req = requests . post ( msgsend_url , data = json . dumps ( params )) logging . info ( 'sendto:' + touser + ';;subject:' + subject + ';;message:' + message )赋予执行权限chmod +x /usr/lib/zabbix/alertscripts/weixin.py创建日志文件touch /tmp/weixin.log chown zabbix:zabbix /tmp/weixin.log测试脚本,用户名为企业微信通讯录中的用户名,一般为拼音全拼,严格区分大小写!/usr/lib/zabbix/alertscripts/weixin.py 用户名 '标题' '测试成功'此时企业微信可以收到zaabix应用发来的信息。5、添加报警媒介zabbix后台 - 管理 - 报警媒介类型名称 weixin类型 脚本脚本名称 weixin.py脚本参数:{ALERT.SENDTO} {ALERT.SUBJECT} {ALERT.MESSAGE} 6、配置Trigger actions触发动作,启用消息推送管理员,填写要发送的信息配置 - 动作 Trigger actions - 创建动作 在 动作 中填写名称在 操作 中编辑操作和恢复操作操作发送消息zabbix管理员组仅发送到微信custom message主题:服务器报警消息:告警主机:{HOST.NAME} 告警地址:{HOST.IP} 监控项目:{ITEM.NAME} 监控取值:{ITEM.LASTVALUE} 告警等级:{TRIGGER.SEVERITY} 当前状态:{TRIGGER.STATUS} 告警信息:{TRIGGER.NAME} 告警时间:{EVENT.DATE} {EVENT.TIME} 事件ID:{EVENT.ID}恢复操作通知所有参与者custom message主题:服务器已恢复消息:告警主机:{HOST.NAME} 告警地址:{HOST.IP} 监控项目:{ITEM.NAME} 监控取值:{ITEM.LASTVALUE} 告警等级:{TRIGGER.SEVERITY} 当前状态:{TRIGGER.STATUS} 告警信息:{TRIGGER.NAME} 告警时间:{EVENT.DATE} {EVENT.TIME} 事件ID:{EVENT.ID} 7、配置Autoregistration actions自动注册,填写要发送的信息在Autoregistration actions自动注册中注意:自动注册的其他内容在下方linux、windows部分发送消息zabbix管理员组仅送到weixinCustom message主题:Linux主机自动注册到zabbix服务器消息:主机名:{HOST.HOST} 主机IP:{HOST.IP} Agent端口:{HOST.PORT} 8、接收微信推送人员管理-用户-报警媒介邮箱推送、微信推送 可以理解为仅配置脚本不同,其他配置参数基本一致邮箱 1、安装mailxyum install mailx -y2、修改mailx配置vim /etc/mail.rc最后添加 set from=xx@qq.com set smtp=smtp.qq.com set smtp-auth-user=xx@qq.com set smtp-auth-password=邮箱密码 set smtp-auth=login3、测试邮箱echo “hello world” | mail -s “testmail” xx@qq.com4、编写邮箱脚本cd /usr/lib/zabbix/alertscripts/vim mailx.sh#!/bin/bash #send mail messages=`echo $3 | tr '\r\n' '\n'` subject=`echo $2 | tr '\r\n' '\n'` echo "${messages}" | mail -s "${subject}" $1 >>/tmp/mailx.log 2>&15、创建日志,添加权限touch /tmp/mailx.logchown -R zabbix.zabbix /tmp/mailx.logchmod +x /usr/lib/zabbix/alertscripts/mailx.shchown -R zabbix.zabbix /usr/lib/zabbix/6、添加使用其他添加过程与微信相同微信推送 1、查看短信平台文档编写短信脚本,注意不通用我用的短信平台采用http get通讯cd /usr/lib/zabbix/alertscripts/cat sendSMS.sh#!/bin/bash #手机号码 MOBILE_NUMBER=$1 #短信主题 MESSAGE_SUBJECT=$2 #短信内容 MESSAGE_UTF8=$3 #调用短信接口 /usr/bin/curl -s -G --data-urlencode userid=用户ID --data-urlencode account=用户名 --data-urlencode password=用户密码 --data-urlencode mobile=${MOBILE_NUMBER} --data-urlencode content="${MESSAGE_SUBJECT}-${MESSAGE_UTF8}" http://www.短信平台接口.com/xx?action=send >> /tmp/sendSMS.log2、添加使用其他添加过程与微信相同五、自动注册windows主机 平台 - 配置 - 动作 - Autoregistration actions自动注册 创建动作元数据中的 Linux 为下方脚本里的 HostMetadata=windows 严格区分大小写操作添加主机添加主机群组关联模板下载安装agent2客户端https://www.zabbix.com/cn/download_agents最新版本为 Zabbix agent 2 v6.0.5修改配置 HostMetadata=windowsC:\Program Files\Zabbix Agent 2\zabbix_agent2.conf重启服务收到自动注册提示六、自动注册linux主机 zabbix平台自动注册linux与windows方法基本相同,元数据修改为linux在linux客户端上可以使用自动化脚本安装zabbix agent2客户端我这里仅放一个centos7/8的安装脚本,内容为卸载agent1安装agent2#/bin/bash echo "关闭selinux" sed -i '/SELINUX/s/enforcing/disabled/' /etc/selinux/config setenforce 0 echo "下载zabbix-agent2,卸载agent1" OSVERSION=`cat /etc/redhat-release |awk -F "release " '{print $2}'|awk -F "." '{print $1}'` rpm -Uvh https://repo.zabbix.com/zabbix/6.0/rhel/$OSVERSION/x86_64/zabbix-release-6.0-1.el$OSVERSION.noarch.rpm yum clean all yum remove zabbix-agent -y yum install zabbix-agent2 -y echo "修改zabbix-agent2配置文件" ipaddr=$(ip a show |grep ens|grep inet |awk '{print $2}'|awk -F '/' '{print $1}') zabbix_server='192.168.1.110' hostname=$(hostname) sed -i "s/^Server=127.0.0.1/Server=${zabbix_server}/g" /etc/zabbix/zabbix_agent2.conf sed -i "s/^ServerActive=127.0.0.1/ServerActive=${zabbix_server}/g" /etc/zabbix/zabbix_agent2.conf sed -i "s/Hostname=Zabbix server/Hostname=${hostname}/g" /etc/zabbix/zabbix_agent2.conf sed -i "s/# HostMetadata=/HostMetadata=linux/g" /etc/zabbix/zabbix_agent2.conf echo "防火墙放行zabbix-agent端口" firewall-cmd --permanent --add-port=10050-10051/tcp firewall-cmd --reload echo "启动zabbix-agent服务" systemctl enable --now zabbix-agent2 zabbixagentpid=`ps -ef |grep zabbix_agent2|grep -w 'zabbix_agent2'|grep -v 'grep'|awk '{print $2}'` if [ "$zabbixagentpid" ];then echo "zabbix agent2 正在运行 " else echo "zabbix agent2 安装失败!!!" fi七、通过SNMP监控交换机 1、为zabbix添加SNMPv2模板SNMPv2模板下载https://share.zabbix.com/templates/network-devices-fortigate-template-fortinet-all-discovery/#body2、交换机配置snmpv2snmp-agent sys-info version v2c snmp-agent community read public snmp-agent community write private snmp-agent trap enable snmp-agent target-host trap address udp-domain 192.168.1.110 params securityname public v2c snmp-agent3、查找MIBH3C常用MIBhttps://www.h3c.com/cn/Service/Document_Software/TechnicalInfo/PorductMaintanInfo/Switches/DailyMainten/MIBList/4、安装snmp调试工具并进行测试dnf -y install net-snmp-utilssnmpwalk为模糊测试snmpwalk -v 2c -c public 192.168.237.50 .1.3.6.1.4.1.2021.10.1.3snmpget是zabbix的精准获取方式snmpget -v 2c -c public 192.168.237.50 .1.3.6.1.4.1.2021.10.1.35、举例如S5130 CPU使用率,查询H3C手册为 1.3.6.1.4.1.25506.8.35.18.1.3使用snmpwalk -v 2c -c public 192.168.237.50 1.3.6.1.4.1.25506.8.35.18.1.3后返回SNMPv2-SMI::enterprises.25506.8.35.18.1.3.0 = INTEGER: 16得知最后多一位.0使用snmpget -v 2c -c public 192.168.237.50 1.3.6.1.4.1.25506.8.35.18.1.3.0得到结果相同,则此项为s5130型号的CPU使用率在zabbix新建监控项,即可实现CPU使用率记录新建触发器,即可实现CPU使用率报警前5次报警值均超过80时进行CPU使用率过高报警最终效果其他参数:CPU使用率 1.3.6.1.4.1.25506.8.35.18.4.3.1.4.0.1 内存使用率 1.3.6.1.4.1.25506.8.35.18.1.16.0 固件版本 1.3.6.1.2.1.1.1.0 开机时间 1.3.6.1.2.1.1.3.0 SN 1.3.6.1.4.1.25506.2.6.1.2.1.1.2.2 温度 1.3.6.1.4.1.25506.2.6.1.1.1.1.12.212八、添加vsphere vCenter监控 1、开启VMware支持并重启zabbix-server服务/etc/zabbix/zabbix_server.conf ### Option: StartVMwareCollectors StartVMwareCollectors=52、检查vCenter sdk接口返回500代码代表接口在工作curl -i -k --data "" https://172.16.0.1/sdk HTTP/2 500 cache-control: no-cache content-type: text/xml; charset=utf-8 date: Tue, 28 Jun 2022 01:36:00 GMT x-envoy-upstream-service-time: 0 server: envoy3、登录每台ESXi主机开启MOB服务系统高级设置,搜索Config.HostAgent.plugins.solo.enableMob,确定值改为true4、zabbix创建主机注意是修改继承的宏 https://172.16.0.1/sdk5、查看数据一段时间后,zabbix可以获取到所有的vCenter、ESXi和虚拟机的信息九、grafana面板 1、安装当前最新版本grafana-10.0.1sudo yum install -y https://dl.grafana.com/oss/release/grafana-10.0.1-1.x86_64.rpm注意配置开机启动并配置防火墙,默认使用3000端口2、安装grafana zabbix插件grafana-cli plugins list-remote grafana-cli plugins install alexanderzobnin-zabbix-app systemctl restart grafana-server3、登录grafana接入zabbix源http://IP:3000/ 打开grafana界面,打开后输入admin/admin登录,登陆后按提示更改admin密码。启用zabbix插件配置数据源http://ip/zabbix/api_jsonrpc.php保存并测试成功新建面板即可十、首页图表监控 首页添加构件十一、modbus动环采集 https://90apt.com/3387十二、ZbxTable分析系统 十三、数据库监控 (一)微软MSSQL数据库监控安装完SQLServer数据库,开启数据库远程访问配置对IP的监听配置防火墙端口开放测试端口RHEL8系统安装ODBC驱动https://learn.microsoft.com/en-us/sql/connect/odbc/linux-mac/installing-the-microsoft-odbc-driver-for-sql-server?view=sql-server-ver16&tabs=redhat18-install%2Calpine17-install%2Cdebian8-install%2Credhat7-13-install%2Crhel7-offlinesudo su #Download appropriate package for the OS version #Choose only ONE of the following, corresponding to your OS version #RHEL 7 and Oracle Linux 7 curl https://packages.microsoft.com/config/rhel/7/prod.repo > /etc/yum.repos.d/mssql-release.repo #RHEL 8 and Oracle Linux 8 curl https://packages.microsoft.com/config/rhel/8/prod.repo > /etc/yum.repos.d/mssql-release.repo #RHEL 9 curl https://packages.microsoft.com/config/rhel/9.0/prod.repo > /etc/yum.repos.d/mssql-release.repo exit sudo yum remove unixODBC-utf16 unixODBC-utf16-devel #to avoid conflicts sudo ACCEPT_EULA=Y yum install -y msodbcsql18 # optional: for bcp and sqlcmd sudo ACCEPT_EULA=Y yum install -y mssql-tools18 echo 'export PATH="$PATH:/opt/mssql-tools18/bin"' >> ~/.bashrc source ~/.bashrc # optional: for unixODBC development headers sudo yum install -y unixODBC-devel配置/etc/odbc.inihttps://learn.microsoft.com/zh-cn/sql/connect/odbc/linux-mac/connection-string-keywords-and-data-source-names-dsns?view=sql-server-ver16[TEST] Driver = ODBC Driver 18 for SQL Server # Server = [protocol:]server[,port] Server = tcp:172.16.10.102,1433 TrustServerCertificate=YES # # Note: # Port isn't a valid keyword in the odbc.ini file # for the Microsoft ODBC driver on Linux or macOS 测试,连接成功isql -v TEST user passwd +---------------------------------------+ | Connected! | | | | sql-statement | | help [tablename] | | echo [string] | | quit | | | +---------------------------------------+ SQL> 配置zabbix模板,为目标主机配置一个MSSQL by ODBC在继承以及主机 宏中修改值{$MSSQL.DSN}即上方odbc.ini中定义的[TEST]{$MSSQL.USER}和{$MSSQL.PASSWORD}是自定义的账号密码注意右侧可以选择密文模式保存(二)MYSQL数据库监控为目标主机关联MySQL by Zabbix agent 2模板为MYSQL创建监控专用用户并配置宏mysql -uroot -p use mysql; CREATE USER 'zbx_monitor'@'%' IDENTIFIED BY '<password>'; GRANT REPLICATION CLIENT,PROCESS,SHOW DATABASES,SHOW VIEW ON *.* TO 'zbx_monitor'@'%';{$MYSQL.USER}和{$MYSQL.PASSWORD}是自定义的账号密码注意右侧可以选择密文模式保存十三、分组报警 1、将不同主机的告警发送给不同用户创建主机群组,并将主机添加至主机组,如动环告警 2、为主机添加群组3、创建用户群组动环报警组4、创建用户加入群组创建用户donghuanyonghu,加入动环报警组5、为用户创建报警媒介我这里用企业微信报警6、触发器操作发送报告的触发器7、操作发送群组配置完成十四、总结 对接oceanbase数据库见oceanbase文章十五、总结 功能强大、简单方便、干净卫生
ALMA Linux 8飞速搭建zabbix6LTS、微信邮箱短信报警、windows、linux、交换机、vCenter监控、grafana面板、modbus动环采集、ZbxTable分析系统、Mysql、MSsql数据库监控、分组报警、对接oceanbase数据库 一、环境 zabbix所在服务器系统为alma8,zabbix6要求的mariadb版本为10.5-10.6,同时zabbix提供了zabbix-selinux-policy来配置selinux,所以安装中也不再要求关闭selinux。二、安装zabbix 官方安装帮助页面,安装方法随版本更新,官方更新更快https://www.zabbix.com/cn/download1、配置zabbix 软件源rpm -Uvh https://repo.zabbix.com/zabbix/6.0/rhel/8/x86_64/zabbix-release-6.0-4.el8.noarch.rpm dnf clean all2、安装zabbix-server和zabbix-agent2dnf install zabbix-server-mysql zabbix-web-mysql zabbix-apache-conf zabbix-sql-scripts zabbix-selinux-policy zabbix-agent23、安装数据库配置mariabd源 /etc/yum.repos.d/MariaDB.repo# MariaDB 10.6 CentOS repository list - created 2023-02-02 03:14 UTC # https://mariadb.org/download/ [mariadb] name = MariaDB baseurl = https://mirrors.aliyun.com/mariadb/yum/10.6/centos8-amd64 module_hotfixes=1 gpgkey=https://mirrors.aliyun.com/mariadb/yum/RPM-GPG-KEY-MariaDB gpgcheck=1安装数据库、启动、并设置开机启动dnf clean all dnf install mariadb-server systemctl enable --now mariadb4、进行MariaDB数据库初始化mariadb-secure-installation首先是设置密码,会提示先输入密码 Enter current password for root (enter for none):<–初次运行直接回车 Set root password? [Y/n] <– 是否设置root用户密码,输入y并回车 New password: <– 设置root用户的密码 Re-enter new password: <– 再输入一次你设置的密码 Remove anonymous users? [Y/n] <– 是否删除匿名用户 Disallow root login remotely? [Y/n] <–是否禁止root远程登录 Remove test database and access to it? [Y/n] <– 是否删除test数据库 Reload privilege tables now? [Y/n] <– 是否重新加载权限表5、初始化并导入zabbix数据库 mysql -uroot -p登录mariadb> create database zabbix character set utf8mb4 collate utf8mb4_bin; mariadb> create user zabbix@localhost identified by 'password123'; mariadb> grant all privileges on zabbix.* to zabbix@localhost; mariadb> set global log_bin_trust_function_creators = 1; mariadb> quit;导入初始架构和数据,系统将提示您输入新创建的密码zcat /usr/share/zabbix-sql-scripts/mysql/server.sql.gz | mysql --default-character-set=utf8mb4 -uzabbix -p zabbix导入数据库架构后禁用log_bin_trust_function_creators选项mysql -uroot -p mariadb> set global log_bin_trust_function_creators = 0; mariadb> quit;6、配置数据库密码编辑配置文件 /etc/zabbix/zabbix_server.confDBPassword=password1237、配置PHP时区编辑配置文件 /etc/php-fpm.d/zabbix.confphp_value[date.timezone] = Asia/Shanghai8、启动并设置开机启动systemctl enable --now zabbix-server zabbix-agent2 httpd php-fpm9、查看是否有错误信息 cat /var/log/zabbix/zabbix_server.log10、防火墙开放端口firewall-cmd --add-port=80/tcp --permanent firewall-cmd --permanent --add-port=10050-10051/tcp firewall-cmd --reload firewall-cmd --list-ports firewall-cmd --list-services11、替换zabbix自带字体,解决中文乱码百度下载Noto Sans S Chinese字体替换掉默认使用的DejaVuSanscp NotoSansSC-Regular.otf /usr/share/fonts/dejavu/DejaVuSans.ttf12、调整zabbix缓存/etc/zabbix/zabbix_server.confCacheSize=1G13、调整ping进程数/etc/zabbix/zabbix_server.confStartPingers=16三、服务端配置 1、连接到新安装的Zabbix前端: http://server_ip/zabbix注意,mariadb也属于mysql数据库类型2、登录zabbix账号Admin 密码zabbix前端配置完成请务必修改密码四、企业微信消息推送 注意:为了企业的数据安全,从2022年6月20号20点之后,新开启的通讯录同步助手与新创建的自建应用必须在管理端配置可信IP,仅配置的可信IP能调用接口。当前时间2023年6月,企业微信应用验证必须与企业名相同,请考虑使用企业微信机器人推送。1、在企业微信 - 我的企业 - 企业信息 - 企业ID 2、创建zabbix机器人应用企业微信后台 - 应用管理 - 应用 - 创建应用 先进行网页授权及JS-SDK可信域名下的网页可使用网页授权及JS-SDK可信IP位于自行创建的应用-开发接口-企业可信IP 可信IP即服务器所在网络的外网IP,可打开https://ifconfig.me/快速查看,如果企业机房接入多条外网宽带,把外网宽带的IP全都写上3、查看Agentld和Secret 4、准备zabbix机器人脚本环境dnf -y install epel-release dnf -y install python2-pip pip2 install requests查询脚本存放位置cat /etc/zabbix/zabbix_server.conf | grep AlertScript可以看到脚本存放在/usr/lib/zabbix/alertscripts目录中编写脚本 weixin.py并放入上面的目录 ,填入上面获得的三个值#!/usr/bin/env python2 #-*- coding: utf-8 -*- import requests import sys import os import json import logging logging . basicConfig ( level = logging . DEBUG , format = ' %(asctime)s , %(filename)s , %(levelname)s , %(message)s ' , datefmt = ' %a , %d %b %Y %H:%M:%S' , filename = os . path . join ( '/tmp' , 'weixin.log' ), filemode = 'a' ) corpid = 'ww36e' appsecret = '5yFNqeTjrr3I' agentid = 1000002 token_url = 'https://qyapi.weixin.qq.com/cgi-bin/gettoken?corpid=' + corpid + '&corpsecret=' + appsecret req = requests . get ( token_url ) accesstoken = req . json ()[ 'access_token' ] msgsend_url = 'https://qyapi.weixin.qq.com/cgi-bin/message/send?access_token=' + accesstoken touser = sys . argv [ 1 ] subject = sys . argv [ 2 ] #toparty='3|4|5|6' message = sys . argv [ 2 ] + " \n\n " + sys . argv [ 3 ] params ={ "touser" : touser , # "toparty": toparty, "msgtype" : "text" , "agentid" : agentid , "text" : { "content" : message }, "safe" : 0 } req = requests . post ( msgsend_url , data = json . dumps ( params )) logging . info ( 'sendto:' + touser + ';;subject:' + subject + ';;message:' + message )赋予执行权限chmod +x /usr/lib/zabbix/alertscripts/weixin.py创建日志文件touch /tmp/weixin.log chown zabbix:zabbix /tmp/weixin.log测试脚本,用户名为企业微信通讯录中的用户名,一般为拼音全拼,严格区分大小写!/usr/lib/zabbix/alertscripts/weixin.py 用户名 '标题' '测试成功'此时企业微信可以收到zaabix应用发来的信息。5、添加报警媒介zabbix后台 - 管理 - 报警媒介类型名称 weixin类型 脚本脚本名称 weixin.py脚本参数:{ALERT.SENDTO} {ALERT.SUBJECT} {ALERT.MESSAGE} 6、配置Trigger actions触发动作,启用消息推送管理员,填写要发送的信息配置 - 动作 Trigger actions - 创建动作 在 动作 中填写名称在 操作 中编辑操作和恢复操作操作发送消息zabbix管理员组仅发送到微信custom message主题:服务器报警消息:告警主机:{HOST.NAME} 告警地址:{HOST.IP} 监控项目:{ITEM.NAME} 监控取值:{ITEM.LASTVALUE} 告警等级:{TRIGGER.SEVERITY} 当前状态:{TRIGGER.STATUS} 告警信息:{TRIGGER.NAME} 告警时间:{EVENT.DATE} {EVENT.TIME} 事件ID:{EVENT.ID}恢复操作通知所有参与者custom message主题:服务器已恢复消息:告警主机:{HOST.NAME} 告警地址:{HOST.IP} 监控项目:{ITEM.NAME} 监控取值:{ITEM.LASTVALUE} 告警等级:{TRIGGER.SEVERITY} 当前状态:{TRIGGER.STATUS} 告警信息:{TRIGGER.NAME} 告警时间:{EVENT.DATE} {EVENT.TIME} 事件ID:{EVENT.ID} 7、配置Autoregistration actions自动注册,填写要发送的信息在Autoregistration actions自动注册中注意:自动注册的其他内容在下方linux、windows部分发送消息zabbix管理员组仅送到weixinCustom message主题:Linux主机自动注册到zabbix服务器消息:主机名:{HOST.HOST} 主机IP:{HOST.IP} Agent端口:{HOST.PORT} 8、接收微信推送人员管理-用户-报警媒介邮箱推送、微信推送 可以理解为仅配置脚本不同,其他配置参数基本一致邮箱 1、安装mailxyum install mailx -y2、修改mailx配置vim /etc/mail.rc最后添加 set from=xx@qq.com set smtp=smtp.qq.com set smtp-auth-user=xx@qq.com set smtp-auth-password=邮箱密码 set smtp-auth=login3、测试邮箱echo “hello world” | mail -s “testmail” xx@qq.com4、编写邮箱脚本cd /usr/lib/zabbix/alertscripts/vim mailx.sh#!/bin/bash #send mail messages=`echo $3 | tr '\r\n' '\n'` subject=`echo $2 | tr '\r\n' '\n'` echo "${messages}" | mail -s "${subject}" $1 >>/tmp/mailx.log 2>&15、创建日志,添加权限touch /tmp/mailx.logchown -R zabbix.zabbix /tmp/mailx.logchmod +x /usr/lib/zabbix/alertscripts/mailx.shchown -R zabbix.zabbix /usr/lib/zabbix/6、添加使用其他添加过程与微信相同微信推送 1、查看短信平台文档编写短信脚本,注意不通用我用的短信平台采用http get通讯cd /usr/lib/zabbix/alertscripts/cat sendSMS.sh#!/bin/bash #手机号码 MOBILE_NUMBER=$1 #短信主题 MESSAGE_SUBJECT=$2 #短信内容 MESSAGE_UTF8=$3 #调用短信接口 /usr/bin/curl -s -G --data-urlencode userid=用户ID --data-urlencode account=用户名 --data-urlencode password=用户密码 --data-urlencode mobile=${MOBILE_NUMBER} --data-urlencode content="${MESSAGE_SUBJECT}-${MESSAGE_UTF8}" http://www.短信平台接口.com/xx?action=send >> /tmp/sendSMS.log2、添加使用其他添加过程与微信相同五、自动注册windows主机 平台 - 配置 - 动作 - Autoregistration actions自动注册 创建动作元数据中的 Linux 为下方脚本里的 HostMetadata=windows 严格区分大小写操作添加主机添加主机群组关联模板下载安装agent2客户端https://www.zabbix.com/cn/download_agents最新版本为 Zabbix agent 2 v6.0.5修改配置 HostMetadata=windowsC:\Program Files\Zabbix Agent 2\zabbix_agent2.conf重启服务收到自动注册提示六、自动注册linux主机 zabbix平台自动注册linux与windows方法基本相同,元数据修改为linux在linux客户端上可以使用自动化脚本安装zabbix agent2客户端我这里仅放一个centos7/8的安装脚本,内容为卸载agent1安装agent2#/bin/bash echo "关闭selinux" sed -i '/SELINUX/s/enforcing/disabled/' /etc/selinux/config setenforce 0 echo "下载zabbix-agent2,卸载agent1" OSVERSION=`cat /etc/redhat-release |awk -F "release " '{print $2}'|awk -F "." '{print $1}'` rpm -Uvh https://repo.zabbix.com/zabbix/6.0/rhel/$OSVERSION/x86_64/zabbix-release-6.0-1.el$OSVERSION.noarch.rpm yum clean all yum remove zabbix-agent -y yum install zabbix-agent2 -y echo "修改zabbix-agent2配置文件" ipaddr=$(ip a show |grep ens|grep inet |awk '{print $2}'|awk -F '/' '{print $1}') zabbix_server='192.168.1.110' hostname=$(hostname) sed -i "s/^Server=127.0.0.1/Server=${zabbix_server}/g" /etc/zabbix/zabbix_agent2.conf sed -i "s/^ServerActive=127.0.0.1/ServerActive=${zabbix_server}/g" /etc/zabbix/zabbix_agent2.conf sed -i "s/Hostname=Zabbix server/Hostname=${hostname}/g" /etc/zabbix/zabbix_agent2.conf sed -i "s/# HostMetadata=/HostMetadata=linux/g" /etc/zabbix/zabbix_agent2.conf echo "防火墙放行zabbix-agent端口" firewall-cmd --permanent --add-port=10050-10051/tcp firewall-cmd --reload echo "启动zabbix-agent服务" systemctl enable --now zabbix-agent2 zabbixagentpid=`ps -ef |grep zabbix_agent2|grep -w 'zabbix_agent2'|grep -v 'grep'|awk '{print $2}'` if [ "$zabbixagentpid" ];then echo "zabbix agent2 正在运行 " else echo "zabbix agent2 安装失败!!!" fi七、通过SNMP监控交换机 1、为zabbix添加SNMPv2模板SNMPv2模板下载https://share.zabbix.com/templates/network-devices-fortigate-template-fortinet-all-discovery/#body2、交换机配置snmpv2snmp-agent sys-info version v2c snmp-agent community read public snmp-agent community write private snmp-agent trap enable snmp-agent target-host trap address udp-domain 192.168.1.110 params securityname public v2c snmp-agent3、查找MIBH3C常用MIBhttps://www.h3c.com/cn/Service/Document_Software/TechnicalInfo/PorductMaintanInfo/Switches/DailyMainten/MIBList/4、安装snmp调试工具并进行测试dnf -y install net-snmp-utilssnmpwalk为模糊测试snmpwalk -v 2c -c public 192.168.237.50 .1.3.6.1.4.1.2021.10.1.3snmpget是zabbix的精准获取方式snmpget -v 2c -c public 192.168.237.50 .1.3.6.1.4.1.2021.10.1.35、举例如S5130 CPU使用率,查询H3C手册为 1.3.6.1.4.1.25506.8.35.18.1.3使用snmpwalk -v 2c -c public 192.168.237.50 1.3.6.1.4.1.25506.8.35.18.1.3后返回SNMPv2-SMI::enterprises.25506.8.35.18.1.3.0 = INTEGER: 16得知最后多一位.0使用snmpget -v 2c -c public 192.168.237.50 1.3.6.1.4.1.25506.8.35.18.1.3.0得到结果相同,则此项为s5130型号的CPU使用率在zabbix新建监控项,即可实现CPU使用率记录新建触发器,即可实现CPU使用率报警前5次报警值均超过80时进行CPU使用率过高报警最终效果其他参数:CPU使用率 1.3.6.1.4.1.25506.8.35.18.4.3.1.4.0.1 内存使用率 1.3.6.1.4.1.25506.8.35.18.1.16.0 固件版本 1.3.6.1.2.1.1.1.0 开机时间 1.3.6.1.2.1.1.3.0 SN 1.3.6.1.4.1.25506.2.6.1.2.1.1.2.2 温度 1.3.6.1.4.1.25506.2.6.1.1.1.1.12.212八、添加vsphere vCenter监控 1、开启VMware支持并重启zabbix-server服务/etc/zabbix/zabbix_server.conf ### Option: StartVMwareCollectors StartVMwareCollectors=52、检查vCenter sdk接口返回500代码代表接口在工作curl -i -k --data "" https://172.16.0.1/sdk HTTP/2 500 cache-control: no-cache content-type: text/xml; charset=utf-8 date: Tue, 28 Jun 2022 01:36:00 GMT x-envoy-upstream-service-time: 0 server: envoy3、登录每台ESXi主机开启MOB服务系统高级设置,搜索Config.HostAgent.plugins.solo.enableMob,确定值改为true4、zabbix创建主机注意是修改继承的宏 https://172.16.0.1/sdk5、查看数据一段时间后,zabbix可以获取到所有的vCenter、ESXi和虚拟机的信息九、grafana面板 1、安装当前最新版本grafana-10.0.1sudo yum install -y https://dl.grafana.com/oss/release/grafana-10.0.1-1.x86_64.rpm注意配置开机启动并配置防火墙,默认使用3000端口2、安装grafana zabbix插件grafana-cli plugins list-remote grafana-cli plugins install alexanderzobnin-zabbix-app systemctl restart grafana-server3、登录grafana接入zabbix源http://IP:3000/ 打开grafana界面,打开后输入admin/admin登录,登陆后按提示更改admin密码。启用zabbix插件配置数据源http://ip/zabbix/api_jsonrpc.php保存并测试成功新建面板即可十、首页图表监控 首页添加构件十一、modbus动环采集 https://90apt.com/3387十二、ZbxTable分析系统 十三、数据库监控 (一)微软MSSQL数据库监控安装完SQLServer数据库,开启数据库远程访问配置对IP的监听配置防火墙端口开放测试端口RHEL8系统安装ODBC驱动https://learn.microsoft.com/en-us/sql/connect/odbc/linux-mac/installing-the-microsoft-odbc-driver-for-sql-server?view=sql-server-ver16&tabs=redhat18-install%2Calpine17-install%2Cdebian8-install%2Credhat7-13-install%2Crhel7-offlinesudo su #Download appropriate package for the OS version #Choose only ONE of the following, corresponding to your OS version #RHEL 7 and Oracle Linux 7 curl https://packages.microsoft.com/config/rhel/7/prod.repo > /etc/yum.repos.d/mssql-release.repo #RHEL 8 and Oracle Linux 8 curl https://packages.microsoft.com/config/rhel/8/prod.repo > /etc/yum.repos.d/mssql-release.repo #RHEL 9 curl https://packages.microsoft.com/config/rhel/9.0/prod.repo > /etc/yum.repos.d/mssql-release.repo exit sudo yum remove unixODBC-utf16 unixODBC-utf16-devel #to avoid conflicts sudo ACCEPT_EULA=Y yum install -y msodbcsql18 # optional: for bcp and sqlcmd sudo ACCEPT_EULA=Y yum install -y mssql-tools18 echo 'export PATH="$PATH:/opt/mssql-tools18/bin"' >> ~/.bashrc source ~/.bashrc # optional: for unixODBC development headers sudo yum install -y unixODBC-devel配置/etc/odbc.inihttps://learn.microsoft.com/zh-cn/sql/connect/odbc/linux-mac/connection-string-keywords-and-data-source-names-dsns?view=sql-server-ver16[TEST] Driver = ODBC Driver 18 for SQL Server # Server = [protocol:]server[,port] Server = tcp:172.16.10.102,1433 TrustServerCertificate=YES # # Note: # Port isn't a valid keyword in the odbc.ini file # for the Microsoft ODBC driver on Linux or macOS 测试,连接成功isql -v TEST user passwd +---------------------------------------+ | Connected! | | | | sql-statement | | help [tablename] | | echo [string] | | quit | | | +---------------------------------------+ SQL> 配置zabbix模板,为目标主机配置一个MSSQL by ODBC在继承以及主机 宏中修改值{$MSSQL.DSN}即上方odbc.ini中定义的[TEST]{$MSSQL.USER}和{$MSSQL.PASSWORD}是自定义的账号密码注意右侧可以选择密文模式保存(二)MYSQL数据库监控为目标主机关联MySQL by Zabbix agent 2模板为MYSQL创建监控专用用户并配置宏mysql -uroot -p use mysql; CREATE USER 'zbx_monitor'@'%' IDENTIFIED BY '<password>'; GRANT REPLICATION CLIENT,PROCESS,SHOW DATABASES,SHOW VIEW ON *.* TO 'zbx_monitor'@'%';{$MYSQL.USER}和{$MYSQL.PASSWORD}是自定义的账号密码注意右侧可以选择密文模式保存十三、分组报警 1、将不同主机的告警发送给不同用户创建主机群组,并将主机添加至主机组,如动环告警 2、为主机添加群组3、创建用户群组动环报警组4、创建用户加入群组创建用户donghuanyonghu,加入动环报警组5、为用户创建报警媒介我这里用企业微信报警6、触发器操作发送报告的触发器7、操作发送群组配置完成十四、总结 对接oceanbase数据库见oceanbase文章十五、总结 功能强大、简单方便、干净卫生 -
 群晖Active Backup for Business在vSphere vSAN集群中即时还原失败的原因和解决措施 问题在群晖Active Backup for Business中进行即时还原时,显示无法即时还原任务,状态 失败环境VMware ESXi, 7.0.3, 24585291VMware vCenter Server 版本:7.0.3.02200vSAN集群原因联系群晖官方售后查询日志发现,是NFS存储无法挂载判断为NFS被vSphere占用,检查发现vSphere HA,检测信号数据存储默认将群晖的NFS作为了检测信号存储关闭vSphere HA并卸载群晖NFS后,能够正常即时还原解决措施vSphere HA肯定要用,使用群晖创建iSCSI网络存储,将vSphere HA检测信号数据存储设置为iSCSI网络存储,不占用群晖NFS成功解决
群晖Active Backup for Business在vSphere vSAN集群中即时还原失败的原因和解决措施 问题在群晖Active Backup for Business中进行即时还原时,显示无法即时还原任务,状态 失败环境VMware ESXi, 7.0.3, 24585291VMware vCenter Server 版本:7.0.3.02200vSAN集群原因联系群晖官方售后查询日志发现,是NFS存储无法挂载判断为NFS被vSphere占用,检查发现vSphere HA,检测信号数据存储默认将群晖的NFS作为了检测信号存储关闭vSphere HA并卸载群晖NFS后,能够正常即时还原解决措施vSphere HA肯定要用,使用群晖创建iSCSI网络存储,将vSphere HA检测信号数据存储设置为iSCSI网络存储,不占用群晖NFS成功解决 -